The attack launched in 2017 by a Petya ransomware variant is hitting institutions in multiple countries, crippling transportation infrastructure like the airport and subway in Kiev, shutting down shipping terminals in the Netherlands, and compromising business networks from Russia’s Rosneft to British advertising giant WPP.
There are still more questions than answers regarding this new ransomware campaign, but Cyren researchers have confirmed that the malware has married a derivation of last year’s Petya ransomware with the wormlike EternalBlue exploit, used by WannaCry only last month to spread from computer to computer via a vulnerability in a Microsoft file sharing protocol, details of which we discussed here.
Email Inbox Identified, But Now Victims Can’t Get their Decryption Keys
This new Petya ransomware variant asks for the equivalent of $300 in Bitcoin to be transferred to the Bitcoin address 1Mz7153HmuxXTuR2R1t78mGsdzaAtNbBWX. You can see the account details and confer how many ransom payments have been at the Blockchain page here.
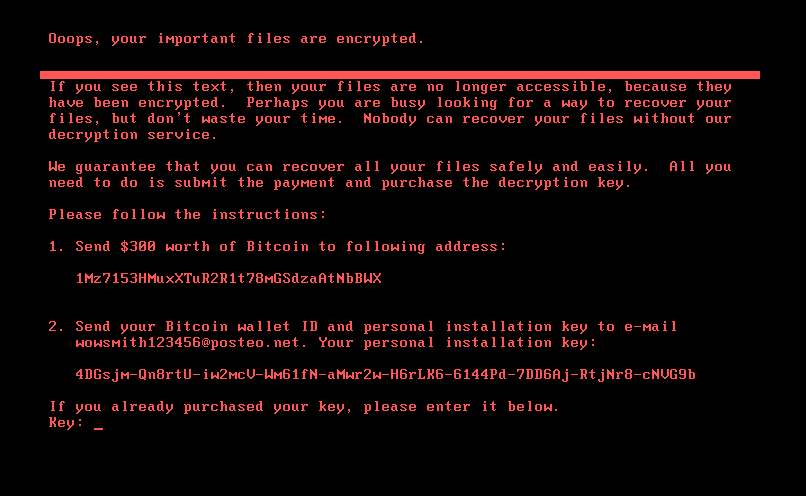
After sending $300 worth of Bitcoin to the address, the victim is supposed to send his Bitcoin wallet ID and his personal installation key to the address wowsmith123456@posteo.net to receive the decryption key. It has now been confirmed that the e-mail provider Posteo has blocked this address, so even if you pay, you will not get the decryption key, since the attacker will not receive the victims e-mail.
How It Works
THe Petya variant uses the rundll32.exe process to run itself. Files are then encrypted by a file in the Windows folder called perfc.dat (Sha-256: 027cc450ef5f8c5f653329641ec1fed91f694e0d229928963b30f6b0d7d3a745).
Petya schedules a task to reboot the victim’s computer within an hour. (schtasks.exe ” /TR “C:Windowssystem32shutdown.exe /r /f) The Master Boot Record (MBR) is modified in such a way that the encryption is carried out, and a custom bootloader is loaded that shows the ransom note and prevents the computer from booting into the Windows operating system.
Here is the ransom note that is displayed after the computer has rebooted:
Doesn’t Use a New Extension
Petya encrypts files with the following file extensions, but does not add a new extension like most ransomware today:
3ds .7z .accdb .ai .asp .aspx .avhd .back .bak .c .cfg .conf .cpp .cs .ctl .dbf .disk .djvu .doc .docx .dwg .eml .fdb .gz .h .hdd .kdbx .mail .mdb .msg .nrg .ora .ost .ova .ovf .pdf .php .pmf .ppt .pptx .pst .pvi .py .pyc .rar .rtf .sln .sql .tar .vbox .vbs .vcb .vdi .vfd .vmc .vmdk .vmsd .vmx .vsdx .vsv .work .xls .xlsx .xvd .zip
Cyren detects the Petya ransomware attack as W32/Ransom.Petya.J!Eldorado.
Samples related to the attack:
- 027cc450ef5f8c5f653329641ec1fed91f694e0d229928963b30f6b0d7d3a745
- 64b0b58a2c030c77fdb2b537b2fcc4af432bc55ffb36599a31d418c7c69e94b1
Speculation on the Initial Distribution
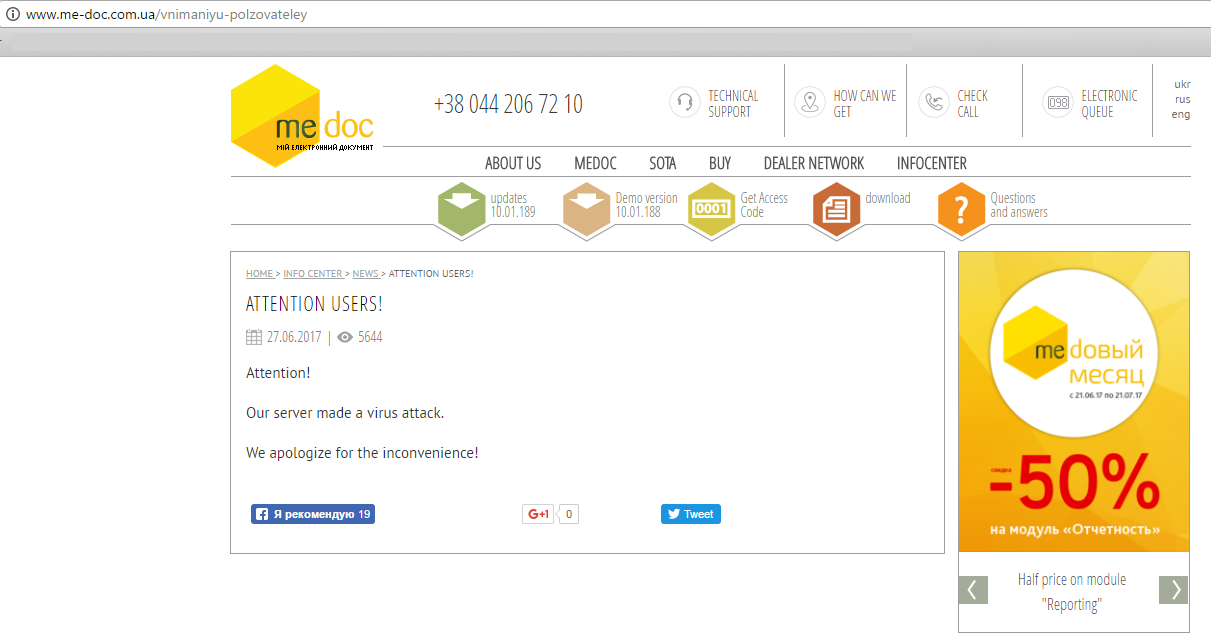
It is being heavily speculated that the attack was initially so concentrated in the Ukraine because it was spreading via a compromised software update from MEDOC, a Ukrainian accounting software, which came to issue a public apology on their website, as seen in the screenshot captured below (English version of the site shown).
Cyren does not recommend paying the ransom fee and strongly encourages users to apply the MS17-010 security patch by running Windows Update. It’s also good to block port 445.
Visit Cyren’s ransomware resource page for a primer on ransomware or download our recent ransomware cyberthreat report for an in-depth briefing.
