The current “Bad Rabbit” ransomware outbreak has been generating quite a bit of news, with some conflicting accounts of its origin. Clarifying here that Bad Rabbit is a variant of the widely reported “NotPetya” ransomware, which we covered in a blog earlier this year.
Bad Rabbit leverages one of the U.S. National Security Agency-developed exploits stolen and released by the Shadow Brokers group last April. Among those exploits was EternalBlue, used by WannaCry last May. Bad Rabbit utilizes EternalRomance, which, like EternalBlue, targets a (different) vulnerability in SMBv1, the Microsoft Server Message Block (SMB) file sharing protocol.
Although Bad Rabbit shares some similarities to NotPetya (for example, a virtually identical ransom note and propagation via the SMB vulnerability), much of the NotPetya code has been rewritten. This time around, Bad Rabbit employs a Trojan-like tool to mine credentials from infected systems, something that NotPetya did not do.
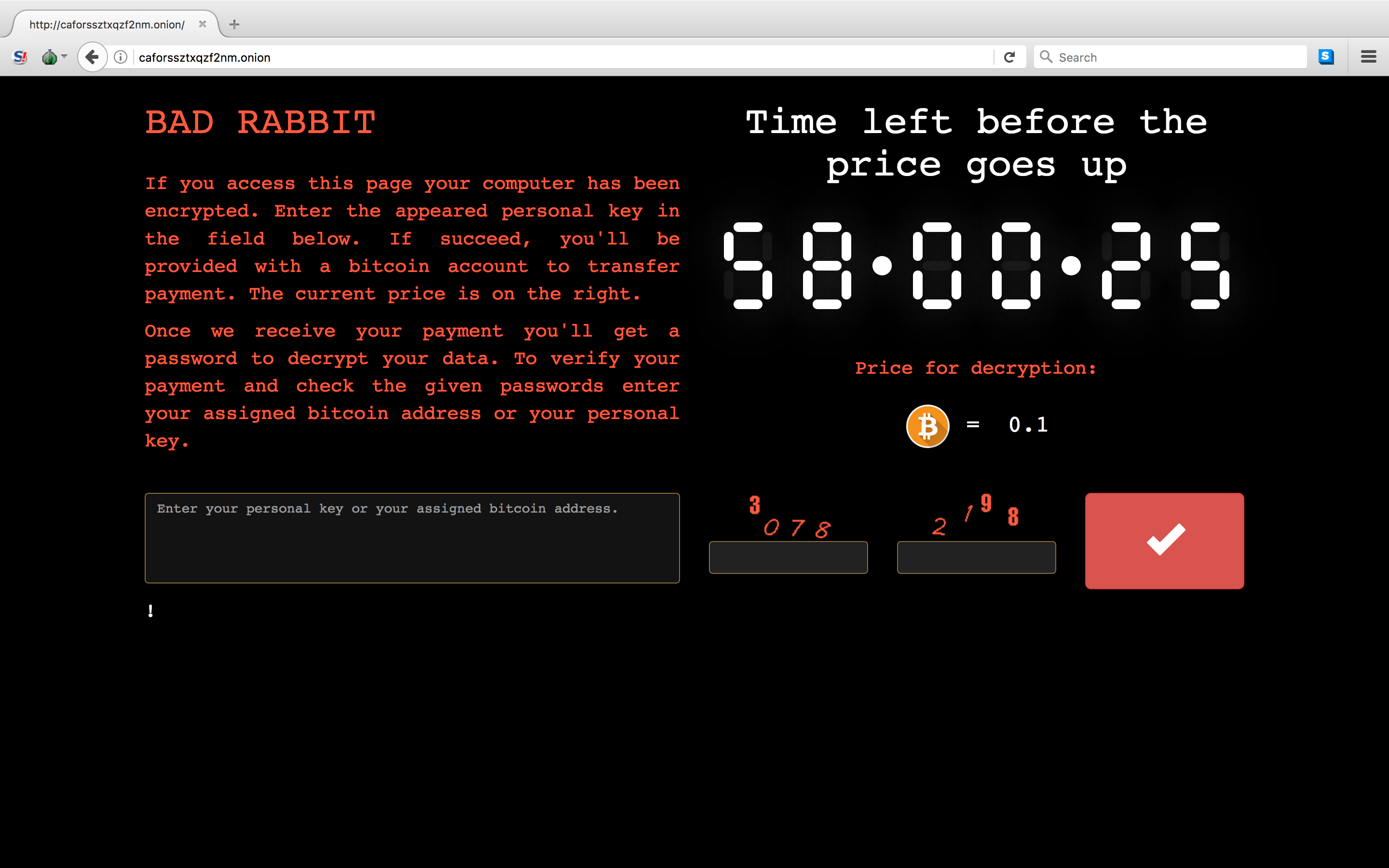
Figure 1: Ransom page from the Bad Rabbit ransomware.
Cyren detects Bad Rabbit as W32/DiskCoder.A.gen!Eldorado and W32/DiskCoder.B.gen!Eldorado.
Cyren offers protection from dangerous ransomware attacks, like Bad Rabbit, through cloud-based Email Security Gateway and Web Security Gateway services. Learn more about ransomware at our ransomware resource page.
