Recently, a lot of phishing campaigns have been moving the embedded links from the body of an email into an attachment, to increase the odds of evading detection. We theorize this is a kind of “social engineering” ploy to move the user along quickly and get them into a clicking frame of mind.
During recent analysis of samples of malicious PDF attachments, we have seen a lot of Apple-themed phishing content, and thought it might be instructive to share how rich and varied the world of Apple phishing has become. From purchases in the app store to a range of activities using one’s Apple ID, threat actors have developed many ways to entice users to click on that malicious link. Without the proper phishing protection, these attacks can lead to the theft of precious Apple credentials.
Types of Apple phishing email themes
We’ve classified the variety of Apple phishing email themes, which are used by cybercriminals to induce users to open the attachment, into six thematic areas:
- Apple ID – PDFs that directly approach the user regarding the status of their credentials.
- Apple App Store – PDFs that are disguised as Apple App Store invoices, purchases or notifications.
- Apple iTunes – PDFs that are disguised as Apple iTunes purchases, subscriptions or notifications.
- Apple Gift Cards – PDFs that are disguised as purchase invoices of Apple Gift Cards.
- Apple Pay – PDFs that are disguised as Apple Pay notifications.
- Apple (Generic) – PDFs that were not automatically identified as any of the above themes, these may have been flagged because the PDF text or images contain strings related to Apple (such as Apple Inc. or apple.com or simply the Apple logo).
Below is a pie chart showing a breakdown of what we’ve been seeing during the start of 2019. It shows that a straightforward appeal to get the user to reset or confirm their Apple ID is used in the majority of cases, or 56 percent of the time. In second place come attempts thematically related to Apple iTunes, seen just over 30 percent of the time. Apple App Store, Apple Gift Card, and Apple Pay themed appeals add up to roughly 11 percent of the credential phishing attempts, leaving around 2 percent in the somewhat grab-bag generic Apple category.

Figure 1 – Breakdown of topical approaches used to phish Apple ID credentials from users
Below are example PDFs, illustrating the various themes used.
Did you buy that app?
Cyber thieves are leveraging popular apps like games with in-app purchasing functionality. In this scenario, the customer will get an Apple phishing email about a subscription they didn’t sign up for. They will be annoyed and highly motivated to cancel the phony subscription. And, of course, in order to cancel, the first step is to “log in” with one’s Apple ID credentials at a spoofed web page, which the criminals immediately capture.
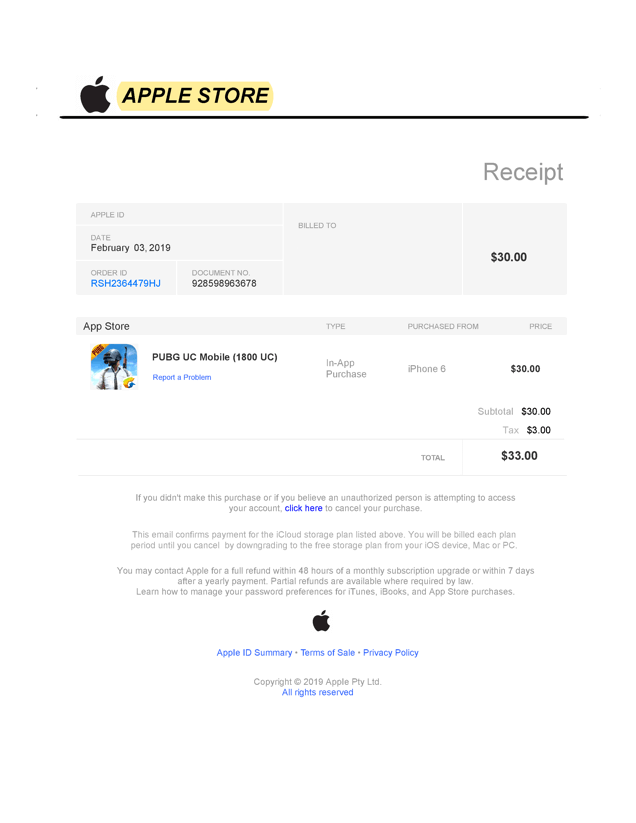
Figure 2 – A fake in-app purchase receipt enticing the user to cancel the purchase.
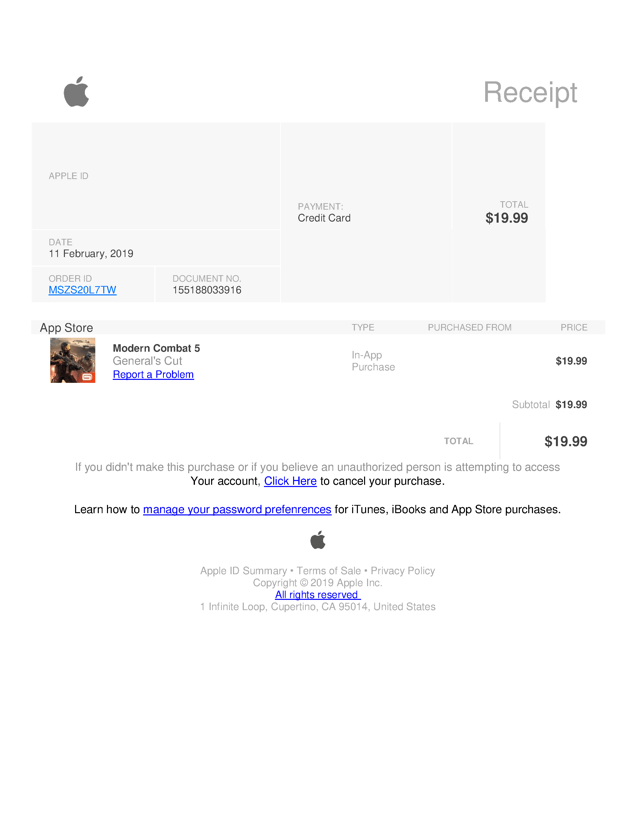
Figure 3 – Another fake in-app purchase receipt enticing the user to cancel the purchase (after giving login credentials, of course).

Figure 4 – A fake subscription confirmation receipt enticing the user to cancel the purchase.
Thank you for buying that gift card, song or…MacBook?
The same essential tactic—you’ve just bought this, but the terms of purchase allow you to still cancel (but you better do it quickly)—is not limited to app purchases, of course. Given the breadth of e-commerce offerings Apple has, the principle is applied to everything from music subscriptions to large purchases like MacBooks (to the recipient’s surprise and likely total annoyance!).
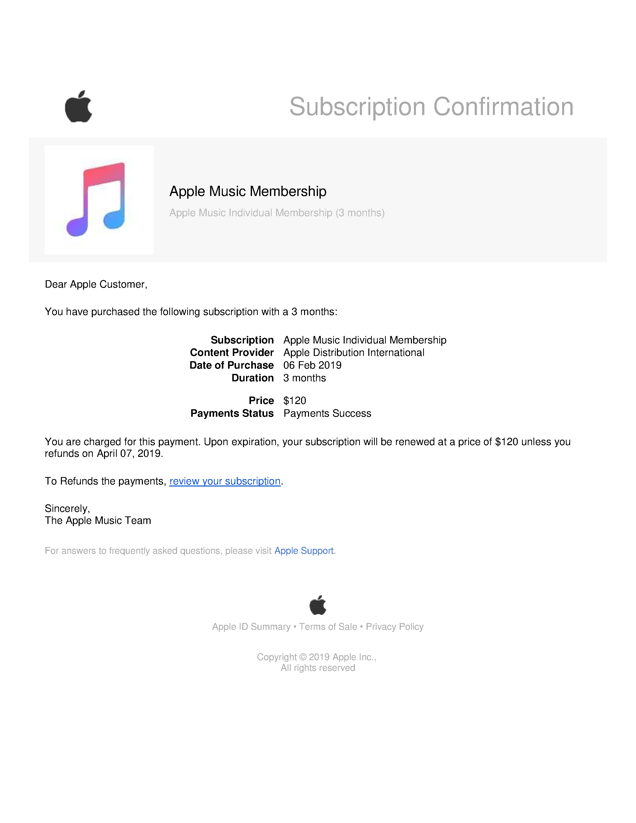
Figure 5 – A fake music subscription confirmation receipt trying to lead the user to cancel the purchase.
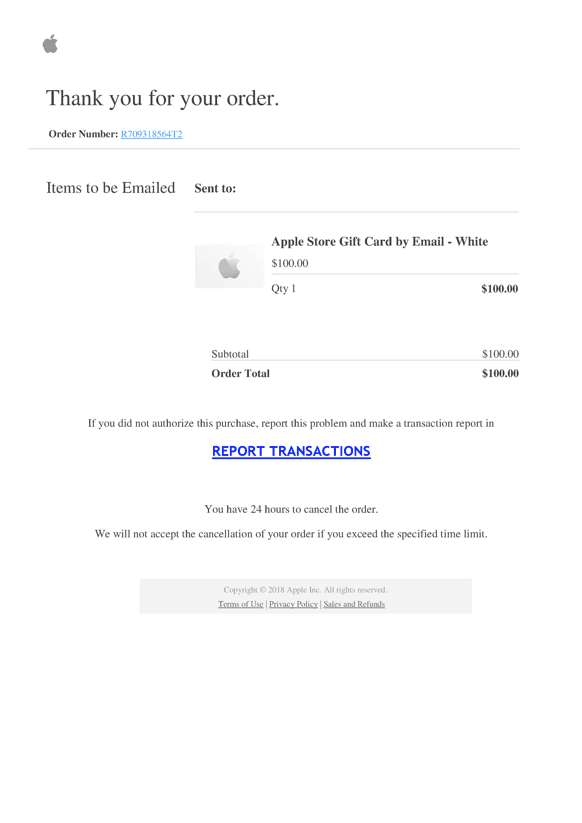
Figure 6 – This fake gift card receipt has a strange “REPORT TRANSACTIONS” call-to-action.
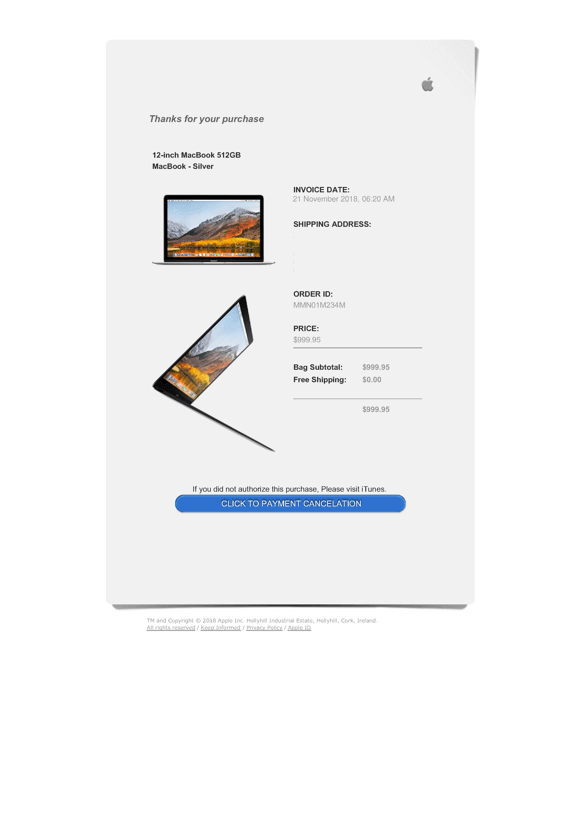
Figure 7 – This fake MacBook purchase receipt also has an unusual call-to-action focusing on cancelation.
It wasn’t you, so could you cancel
Oddly enough, another Apple phishing email tactic is to purport to report unauthorized account activity to the email recipient, but then put the onus of canceling the transaction on the victim.
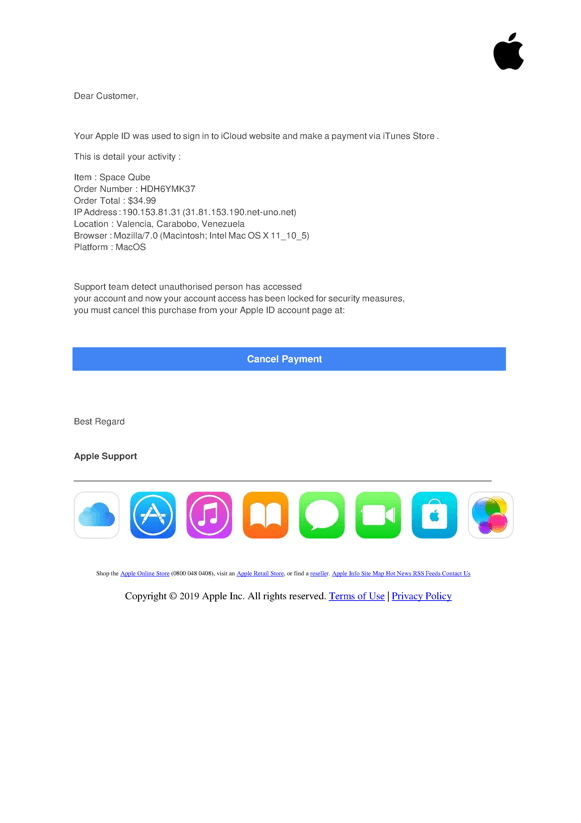
Figure 8 – Another example of the “cancel payment” theme, which allegedly reports account fraud that the recipient must log in to undo.
Did you do something wrong?
For security-related issues, Apple (like everybody else) is known to send notifications to its users. Threat actors like to send fake notifications because they can be effective in creating a sense of urgency, something cyber thieves seek to create. Thematically these notification scams can be divided into two categories:
1. Warnings about suspected account compromise, including unauthorized device access or the classic “unusual login attempts.”
2. Accusations that you’ve committed a usage policy violation, i.e., that you’ve violated the terms of service. Some example fraudulent emails are shown below.
Account compromise, unauthorized device access, or unusual login attempts
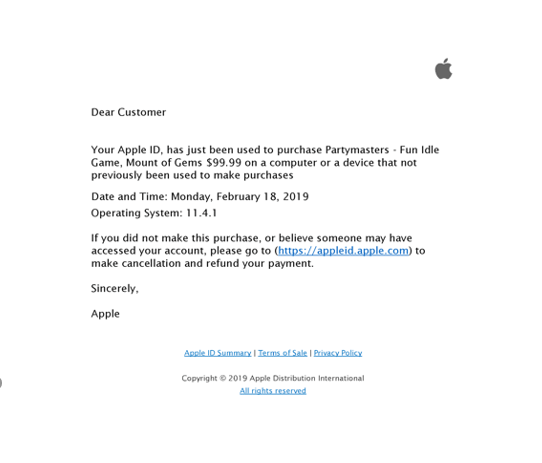
Figure 9 – Example “notification” regarding a purchase from a new device.
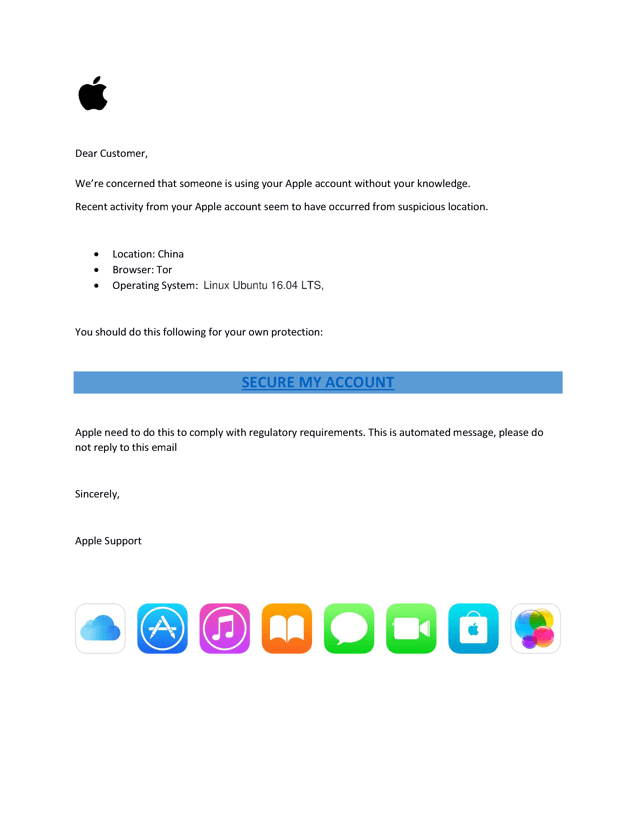
Figure 10 – Notice alleging use from a suspicious location.

Figure 11 – “Your Apple ID has been locked” with a “Verify Update” call-to-action.

Figure 12 – Another example of enticing users with an “unlock your account” theme.
Policy violation
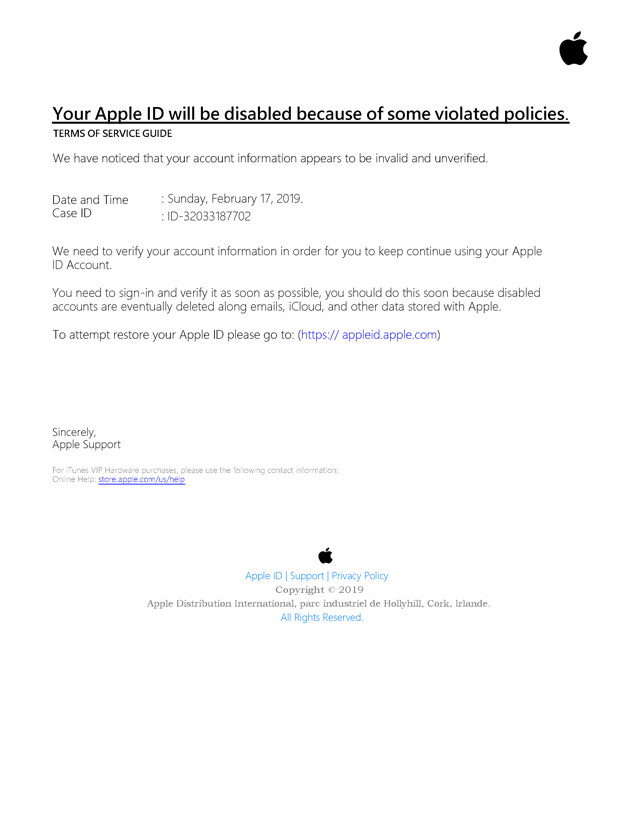
Figure 13 – A policy violation example.
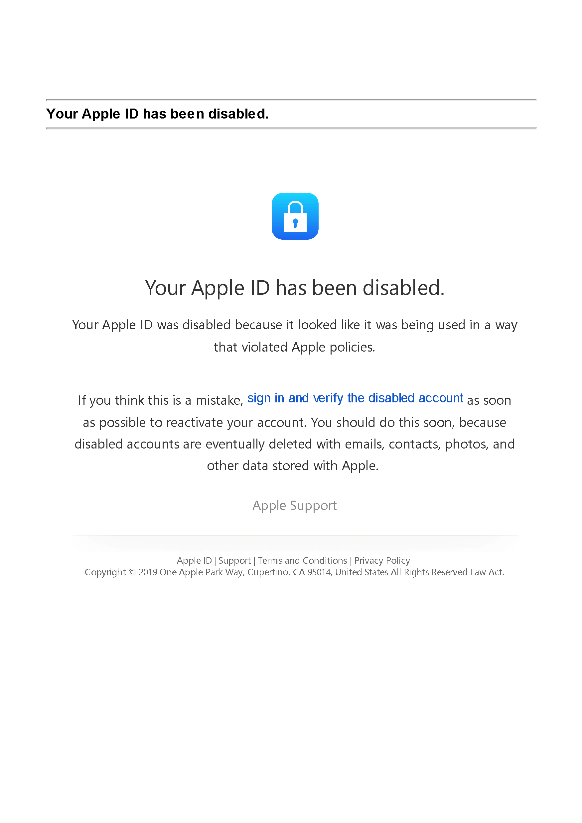
Figure 14 – Another example of “your account has been disabled.”
Got hooked by an Apple phishing email?
If a target clicks on one of the links in these phishing examples, most of the time it leads the target to a fake Apple website. Below is an image of an actual example of an Apple phishing website.

Checking the code of the phishing site, it is AES-256 encrypted and uses an enc.js to decrypt the contents. This is a common tactic to hide the original code of the phishing page, and is used as an evasive tactic, that is to say, to make detection by security systems more difficult.
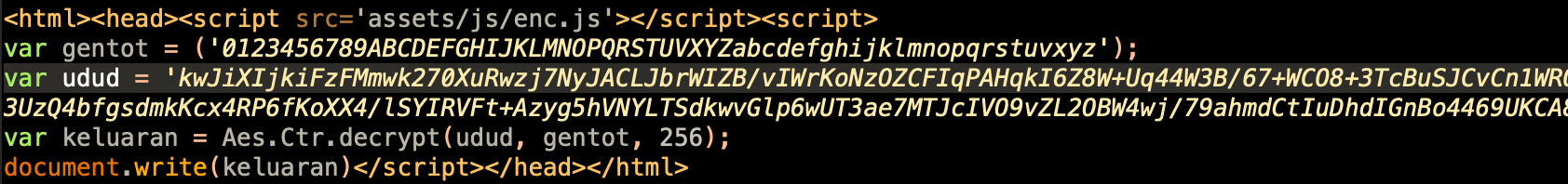
It is notable that the fake website may look exactly like the real Apple login page, so we highly recommend users make sure that they are accessing verified links before entering their account credentials. This can be done by checking webpage certificates, using a URL category checker or by simply checking that the website domain is apple.com, and by having effective, automated phishing protection in place.
