Almost 94% of all malware attacks are delivered via email. These attacks may include ransomware, adware, spyware, and more. Lately we have observed a growing trend of distributing malware through password-protected email attachments. Let’s look at an example of what this kind of malware attack looks like so that you better safeguard your inbox.
Related: Microsoft reports a “leap in attack sophistication”
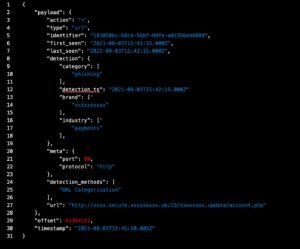
Example of the malware attack
The employee receives an email that appears to be from a trusted and well-known sender, or a common brand, with a catchy subject (ex. ‘Invoice’, ‘Payment verification’, etc). The email contains an attached file that is zipped and password-protected by the attacker. The password creates the illusion the attachment must contain confidential personal information that had to be secured.
The password to open the file from the zip is included in the email:
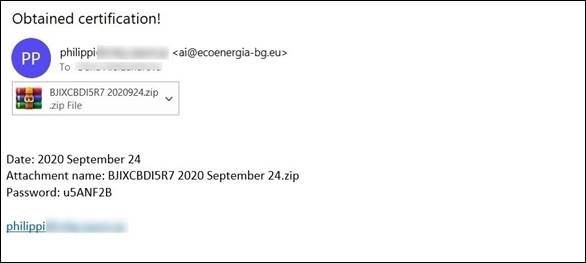
Example of the malicious email
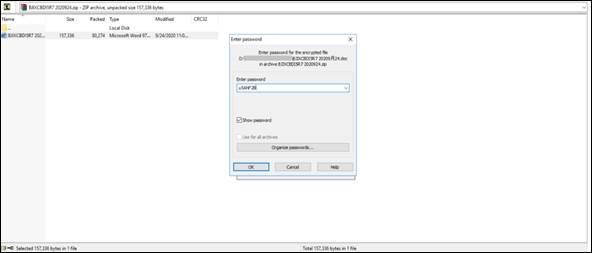
Field to enter the password to open the zipped email’s attachment
Once the password is entered and the file is opened, the user is infected by the malware. Usually, it is what is referred to as a trojan attack which is hidden within the email attachment.
Learn more about “industry” trends, and how phishing kits work.
Emotet trojan malware hidden in email attachments
The Emotet trojan malware is the most common type of malware attack we see when it comes to password-protected email attachments. It’s usually delivered through mail spam and phishing emails that contain infected Microsoft Word or PDF files. When opening the file, the victim is tricked into enabling the macros and triggering the malware logic.
As seen in the example below, the victim opened the encrypted, zipped attachment—a Microsoft Word file. That file fakes a Microsoft Office Activation Wizard that urges the recipient to ‘Enable Editing’ and ‘Enable Content’ to view and edit the file.
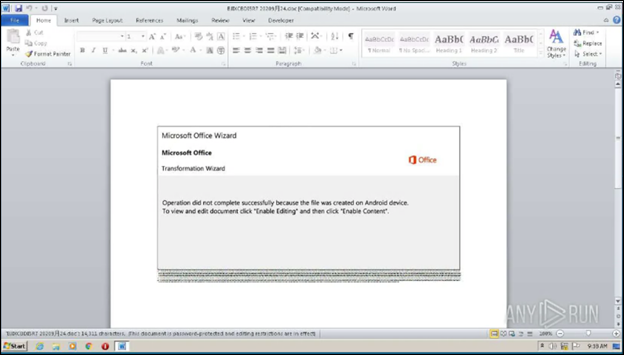
Example of the content of the Emotet infected Microsoft Word document
If the user follows the ‘Enable Editing’ and ‘Enable Content’ processes, they will enable the malicious macros ingrained in it. And the victim won’t even notice it. The file starts to silently run a PowerShell script:

Decoding the script reveals a downloader code:
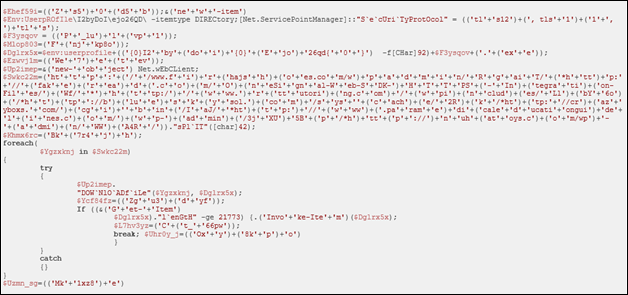
As a result, Emotet will download and execute additional malware, which will be installed directly on the victim’s PC and bypass all possible detection.
Attacks using password-protected zip files (and taking advantage of our social engineering) are virtually invisible to most email filtering techniques.
Protect Against Malware Attacks with Cyren Inbox Security
Cyren Inbox Security was built to safeguard each and every Microsoft 365 mailbox in your organization. It is a continuous and automated layer of security right in the user mailbox:
● Persistently rescans inbound, outbound and delivered emails in all folders
● Reduces investigative overhead with automated incident and case management workflows
● A seamless mailbox plugin lets users scan and report suspicious emails
Our malware detection is unsurpassed. Cyren’s global security cloud processes 25 billion email and web security transactions every day; identifies 9 new threats and blocks over 3,000 known threats each second.
Ready to play with Cyren Inbox Security for Microsoft 365? Start a 30-day trial, no credit card needed >
Discover a behind the scenes look at phishing kits.