Locky Ransomware continues to be distributed in large numbers, however, the email attachments have been changed, probably due to greater blocking of the JavaScript files that have been favored until now.
The Locky attack begins with an email attachment that downloads the actual Locky ransomware. Last week, the Downloader component was switched to Word documents with embedded macros (.docm extension).
This week, for the first time, Locky downloaders are using the WSF file format. A Windows Script File (WSF) allows mixing the scripting languages JScript and VBScript within a single file. We speculate that .wsf files are currently not blocked by default in most email security systems and this has motivated the switch. The attachment still arrives zipped, and in this example is supposedly a “reference letter”:
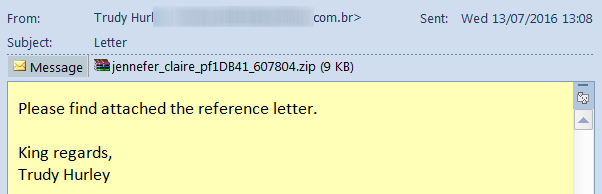
The randomly named .wsf file is somewhat larger than the equivalent JavaScript files previously used.
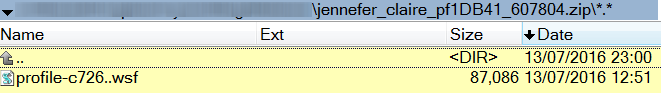
A cursory analysis shows that the .wsf file is simply a JavaScript file with <job> </job> wrapped around it.
<job><script language=”JScript”>… …</script></job>
The docm and wsf variants are all detected and blocked by CYREN.
