Cyber security is key to protecting APIs and SaaS gateways from emerging threats. Businesses rely on secure infrastructure to protect their data, customer trust and achieve strategic goals. At Data443 we help organizations tackle these challenges head on with our Web Security Engine. Here’s how a leading technology services company did it with our advanced URL filtering.
Use Case Situation
A leading technology services company realized they needed to add capabilities to protect inbound traffic to API and SaaS gateways. While they had minimal reliance on legacy security tools they knew emerging threats required a proactive and advanced approach. Their goal was simple: protect customer environments while delivering service uninterrupted.
Challenge: Threats
The company had a big challenge: protect API and SaaS gateways from new and more complex attacks. Traffic analysis and threat mitigation methods were not enough to address:
Malicious URLs evolving fast.
Attackers using social engineering and phishing to get to sensitive info or restricted systems.
Real time detection and response.
Seamless integration with existing infrastructure.
They needed a solution that could do traffic analysis and real time threat blocking without disrupting their business or customer experience.
Cyber Threat Intelligence
In the world of cyber security, cyber threat intelligence is key to protecting an organization’s digital assets. It’s the systematic collection, analysis and dissemination of information about potential or actual cyber threats to an organization’s systems, networks or data. This intelligence comes from multiple sources including open source intelligence, social media and human intelligence to give a 360 degree view of the threat landscape.
Cyber threat intelligence is not just about collecting data; it’s about turning that data into insights. By understanding the tactics, techniques and procedures (TTPs) of threat actors you can anticipate and mitigate threats better. This proactive approach is key to building a cybersecurity strategy that can adapt to the changing threat landscape.
Threat Intelligence Use Cases
Threat intelligence is used across multiple areas of an organization’s cybersecurity, to detect, respond to and mitigate threats. Here are some examples:
Incident Response: In the event of an attack, threat intelligence provides the information to help security teams quickly determine what and how big the attack is. This means faster incident response, less data breaches and less impact to the business.
Threat Hunting: Proactively looking for threats within your systems and networks is key to staying ahead of attackers. Threat intelligence helps security professionals to identify indicators of compromise (IOCs) and other signs of malicious activity so they can detect and prevent early.
Vulnerability Management: Not all vulnerabilities are created equal. Threat intelligence helps to prioritize vulnerabilities based on how likely threat actors will exploit them. This targeted approach to vulnerability management means you address the biggest security threats first.
Security Information and Event Management (SIEM): Threat intelligence integrated with SIEM systems makes them more effective by providing context and prioritization of security alerts. So security teams can focus on the biggest threats and respond faster.
Threats and Trends
The threat landscape is changing daily, new threats and trends emerge all the time. Understanding these threats is key to maintaining network security. Some of the biggest threats and trends are:
Ransomware: This type of malware encrypts an organization’s data and demands payment for the decryption key. Ransomware can bring business to a standstill and cost millions.
Phishing: A common form of social engineering, phishing attacks trick users into giving away sensitive information like login credentials or financial info. These are often the entry point for more attacks.
Advanced Persistent Threats (APTs): APTs are sophisticated long term attacks designed to stay undetected while extracting valuable data. These threats target high value assets and require advanced security to detect and mitigate.
Internet of Things (IoT) Attacks: As IoT devices become more business critical, they introduce new vulnerabilities. Cyber attacks on IoT devices can crash critical systems and compromise sensitive data.
Solution: Incident Response
The company used Data443’s Web Security Engine to solve their problem. For advanced URL filtering our solution:
Real-Time Detection: Ability to detect and block malicious URLs in real-time, stop bad traffic from reaching sensitive endpoints.
Precision Filtering: More accurate filtering of legitimate traffic from threats, fewer false positives.
Seamless Integration: Integration with their existing architecture means quick deployment and minimal disruption.
And mobile devices needed to be secured to protect corporate data accessed through smartphones and tablets. Our solution does this by including Mobile Device Management (MDM) to protect against malicious apps and phishing attacks.
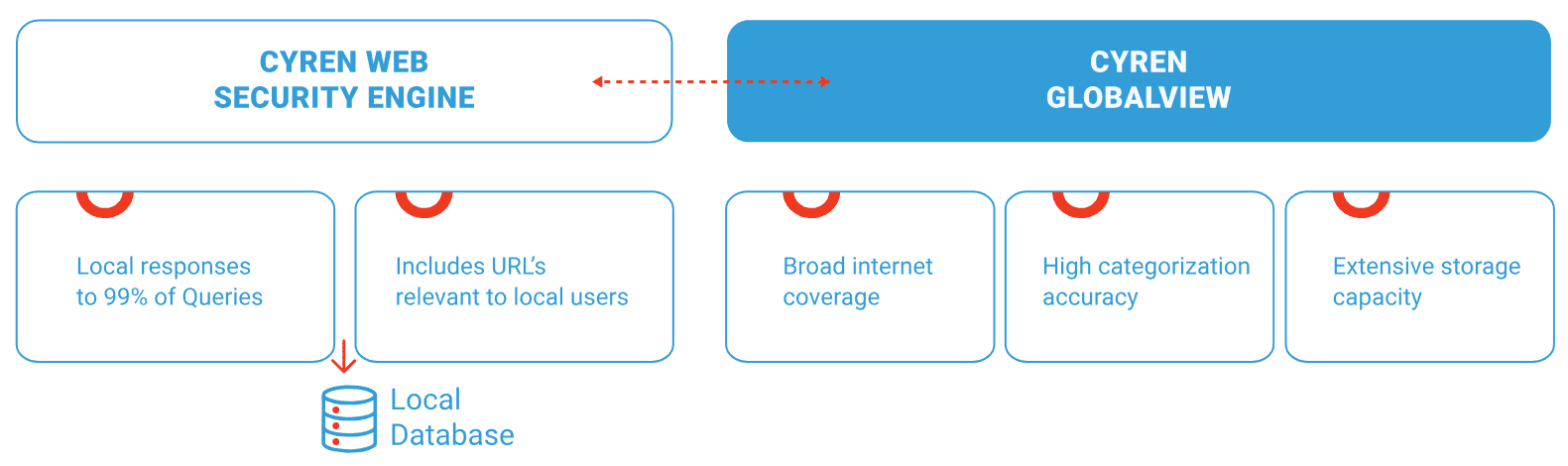
The Cyren Web Security Engine, now part of Data443, is a powerful and comprehensive web security solution. Powered by a massive cloud-based threat intelligence network it has unmatched visibility into web threats and provides precise filtering and blocking. It categorizes billions of URLs across multiple threat and content categories so you can detect and mitigate risks faster. Designed to handle high volume traffic it’s optimized for large scale API and SaaS environments. And with developer friendly APIs and SDKs it’s easy to integrate into your existing platforms and workflows so it’s the perfect solution for businesses looking to secure their digital assets against evolving threats.
By doing this the company was able to address incoming threats while maintaining business as usual and customer satisfaction.
Actionable Threat Intelligence
Actionable threat intelligence is the cornerstone of a robust cybersecurity strategy. This type of intelligence must be specific, timely, relevant, and accurate to enable effective action against cyber threats.
Specificity ensures that the intelligence is tailored to an organization’s unique systems, networks, and data, making it directly applicable to its security needs. Timeliness is crucial, as the value of threat intelligence diminishes over time. Real-time delivery allows security teams to respond swiftly, often before any damage occurs. Relevance focuses efforts on the most critical threats and vulnerabilities, ensuring that security measures address the issues that matter most. Accuracy is equally essential; reliable threat intelligence must be error-free and unbiased, derived from credible sources and thorough analysis to ensure security teams can act with confidence.
By leveraging actionable threat intelligence, organizations can enhance their incident response, improve vulnerability management, and anticipate emerging threats. This proactive approach is fundamental to reducing the risk of data breaches, mitigating cyberattacks, and strengthening overall cybersecurity.
Outcome: Network Security
The deployment of Data443’s Web Security Engine was a game changer. The company achieved:
Security: A significant reduction in API and SaaS gateway attacks. Bringing in external resources like Google and Mandiant experts into the security team was key to this.
Customer Trust: Demonstrated they were a trusted cybersecurity partner by providing strong protection.
Alignment with Business Goals: Strengthened their ability to support their 2025 goals including expanding their service portfolio and staying competitive.
Why Data443 For Cyber Threat Intelligence?
At Data443 we know every business has unique challenges in securing their digital assets. Our Web Security Engine is designed to fit those needs, providing leading edge protection with precision and speed. Whether you’re protecting API gateways, SaaS platforms or other critical systems our solutions mean you’ll always be one step ahead of evolving threats.
