Understanding “normal” behaviors in email exchanges are key to combating advanced phishing and BEC attacks
by John Stevenson
Detecting Business Email Compromise (BEC)
In the final part of our series of blogs on Business Email Compromise (BEC), it’s time to look at how AI, ML, and NLP all have a part to play in helping to detect the sometimes-subtle behavioral anomalies that indicate the presence of a Business Email Compromise (BEC) attack.
The primary motivation for a BEC attack is financial fraud. An analysis of the Cyren data lake of malicious emails reveals that in four out of five cases employee impersonation was used as a classic “foot in the door” technique to try and trick the unwary. This is frequently accompanied by requests to change payment details, update banking information, or steal credentials such as those giving access to Microsoft 365, Sharepoint, or similar.
So far in this series we’ve looked at how robust email security solutions analyze message metadata and the language in email content to detect these attacks. Now let’s see how adding contextual information and identifying behavioral anomalies gives the defender a real advantage over the attacker.
Context is king
When it comes to detecting a BEC message, some of the earliest clues to the fact that something malicious is happening don’t necessarily come from individual messages but from combinations of messages.
Consider an interchange that begins with a seemingly innocuous message asking if the recipient is in the office that day. Of itself, it is innocent enough but if the recipient responds positively, they implicitly accept that the sender is genuine and open the way for ensuing messages to set up the next stage in an attack. Context is king and a robust email security solution needs to be able to analyze email trails like this to identify indicators of an advanced phishing or BEC attack.
Anomaly detection
We’re creatures of habit. We acquire and repeat patterns of behavior in every aspect of our life and work is no different. These patterns extend to whom we talk to, how we talk to them, and what we say. And they extend to email too! By baselining “normal” behaviors in email traffic we can detect the anomalies that might indicate the presence of a BEC attack.
Consider the following email, one that is representative of the kind of malicious message we see from the Cyren data lake:
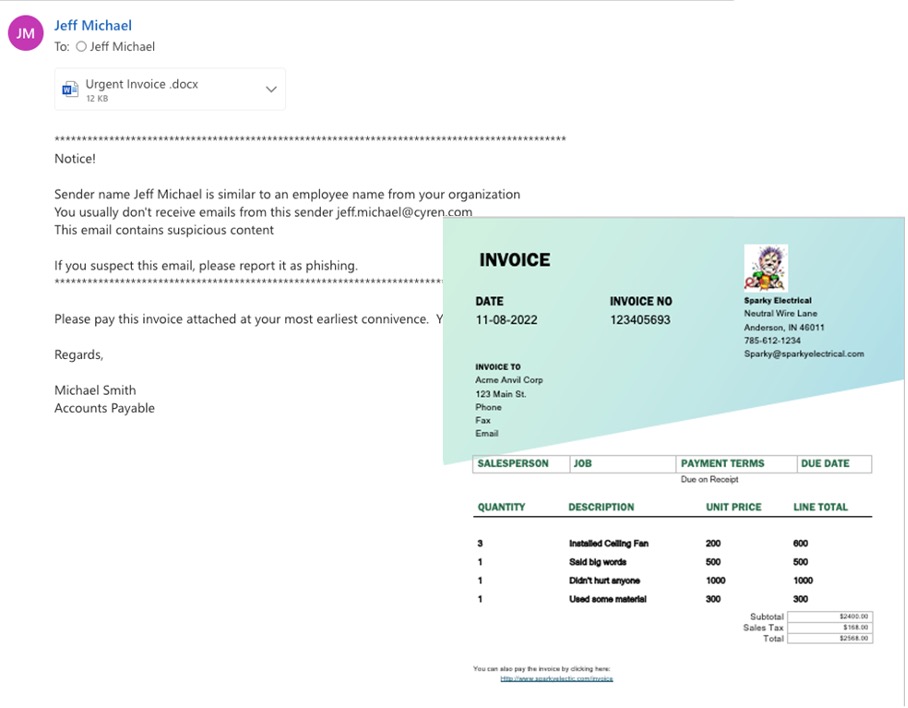
On the face of it, the message looks fine but there are a number of anomalies that a robust email security solution is able to identify.
The sender has never sent the recipient an attachment before:

There’s an informational warning indicating that the person may not be who they claim to be:
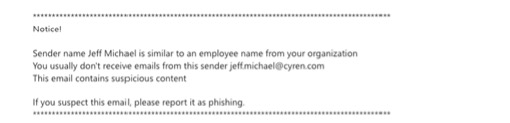
The sender has not previously requested payment on an invoice:

The sender would not normally signoff with Regards:

The attachment contains a URL in the footer:

Taken together these behavioral anomalies help to inform the email security solution that the message is both malicious and fraudulent.
Stopping BEC attacks in the inbox
Twenty-five years ago, firewalls deployed on the network boundary were considered sufficient to repel attacks from intruders. Then it became clear that the bad guys were still getting in and that intrusion detection technologies were needed to look for their presence inside the network. The same change is now taking place in the world of email security.
Modern BEC attacks use an array of techniques to evade detection and defraud the unwary. Sometimes a piece of zero-day malware is concealed in an image. Other times a harmless URL suddenly becomes active – or “weaponized” – days after delivery. Sophisticated phishing and BEC attacks like this, routinely evade detection by both the boundary email security defense and Microsoft’s native security controls.
For this reason, it’s essential that a robust email security solution capable of dealing with BEC attacks, operates where it matters – inside the user inbox.
About Cyren Inbox Security
Cyren Inbox Security (CIS) is a modern Integrated Cloud Email Security SaaS solution that augments native Microsoft and traditional secure email gateway defenses. CIS utilizes AI/ML/NLP capabilities with behavioral analytics, and up-to-the-minute cyber threat intelligence, to automatically protect against, and manage the remediation of email threats that have successfully evaded all other defenses to reach the user’s Microsoft Office 365 inbox.
