In the past week we’ve been receiving reports of different—but seemingly related—email malware campaigns targeting banks in both the US and Europe, specifically in the form of Excel Workbooks containing a malicious macro being sent as an attachment to emails. What’s interesting is that even though the email themes used are varied, the attached bait documents are mostly similar.
Below we have provided an example email and a step-by-step analysis of the malicious Excel Workbook attachment being utilized, along with Indicators of Compromise listed at the bottom. We have not been successful in acquiring the final payload from the malware servers, so we have no idea what the main purpose of this campaign is at this moment. We will update this blog with any new information.
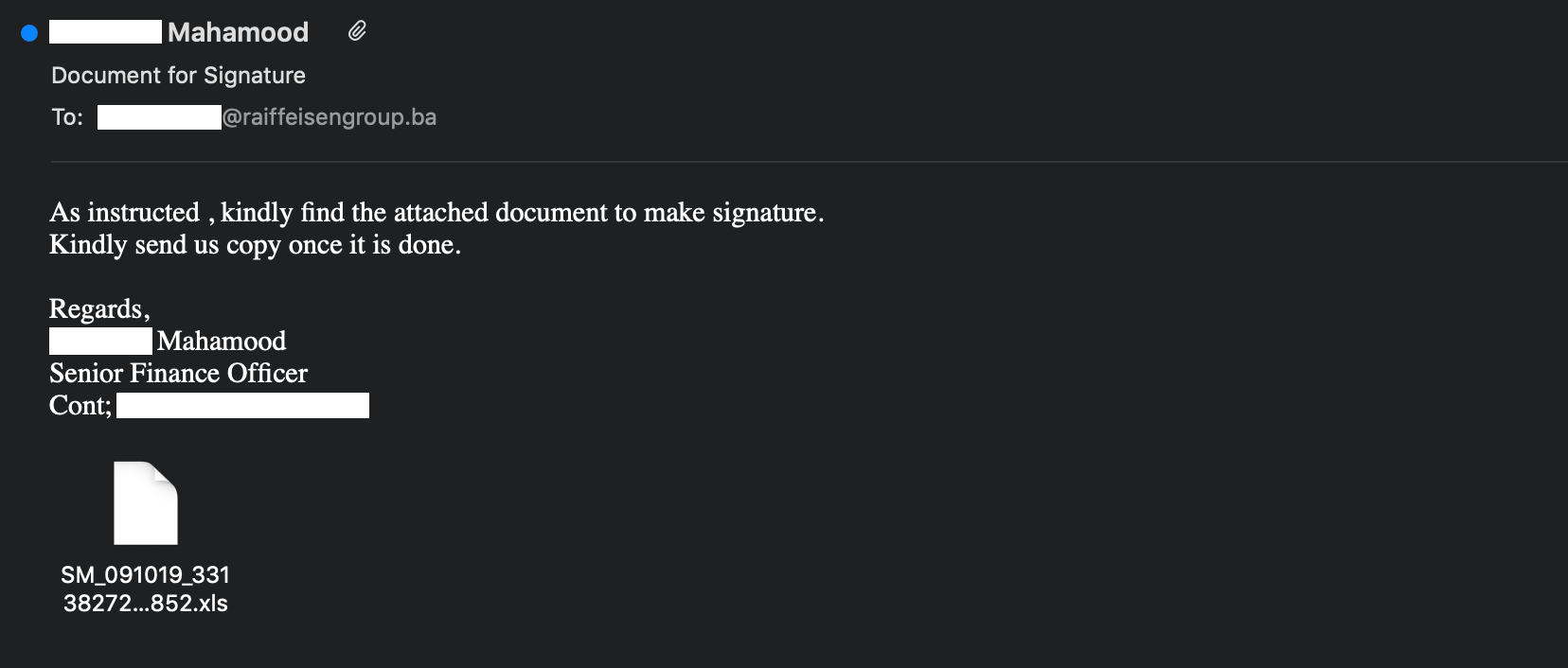
Example email from one of the related campaigns utilizing the Excel Workbook attachment.
How It Works: Payload Analysis
Excel Workbook Attachment
- Once you open this Excel Workbook, you will see a decoy image prompting you to enable the macro content from the Office Security Options
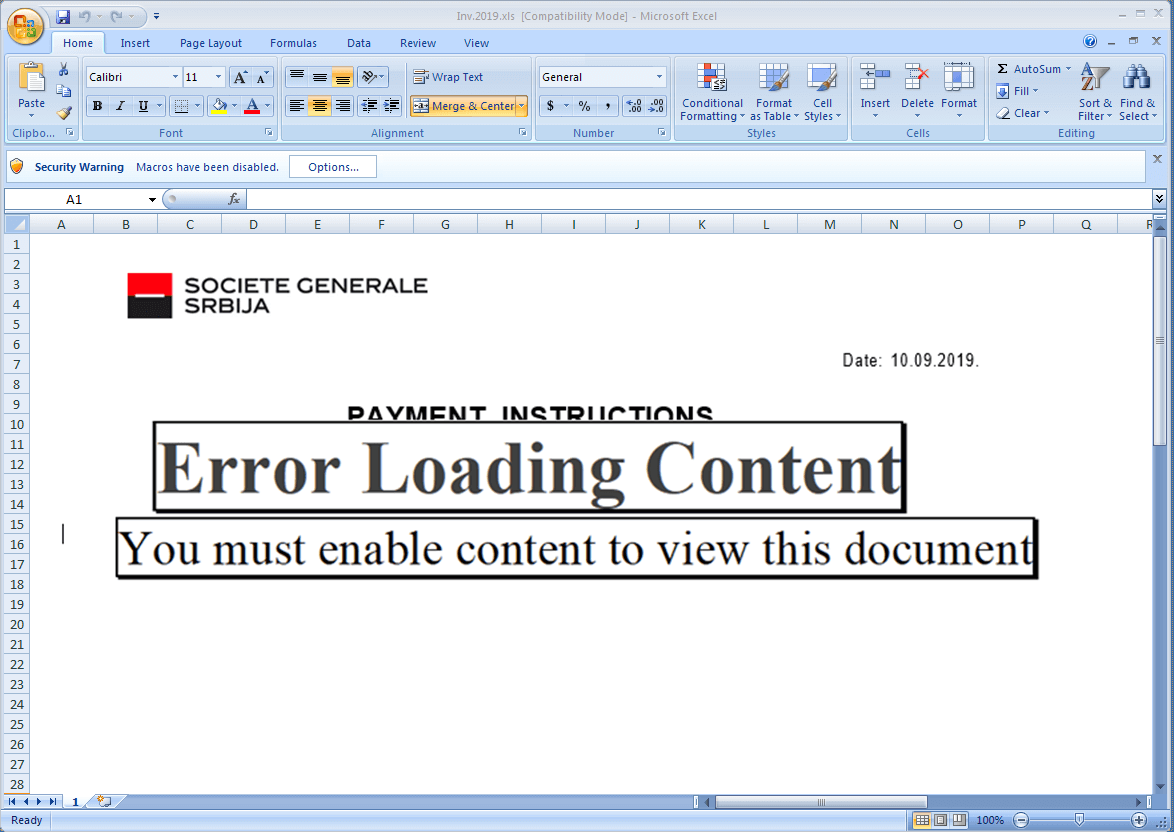
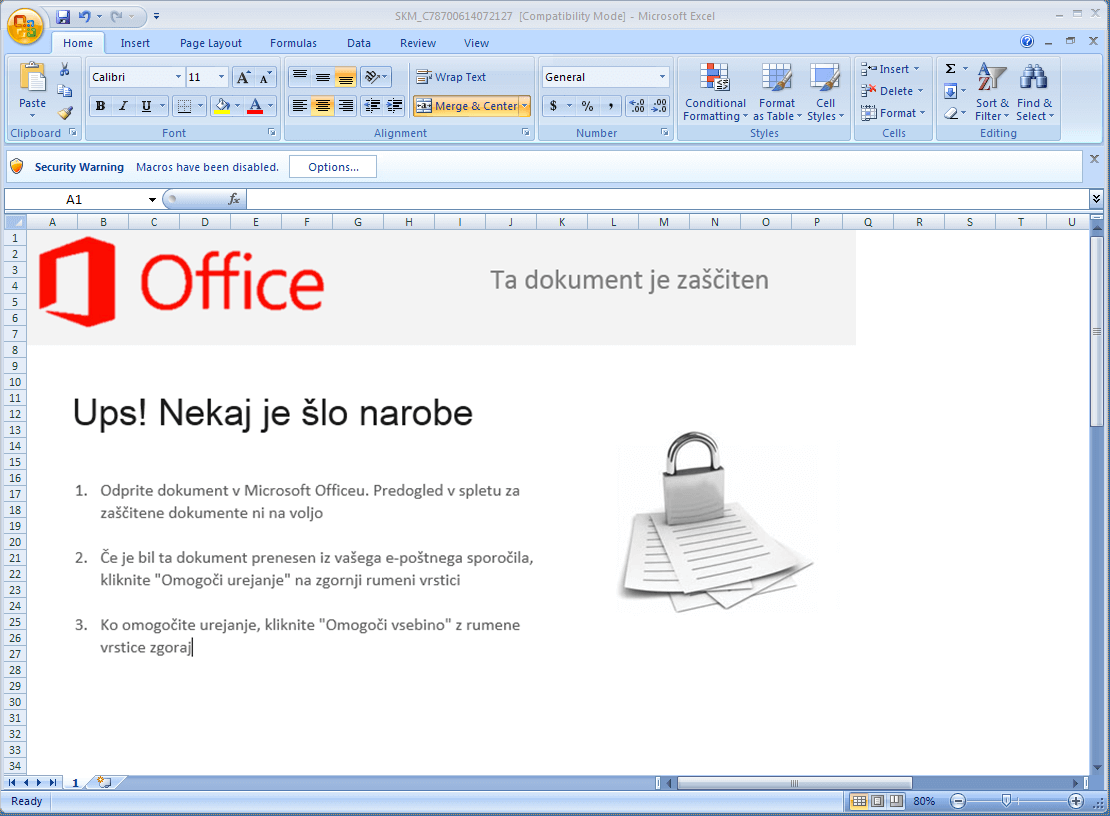
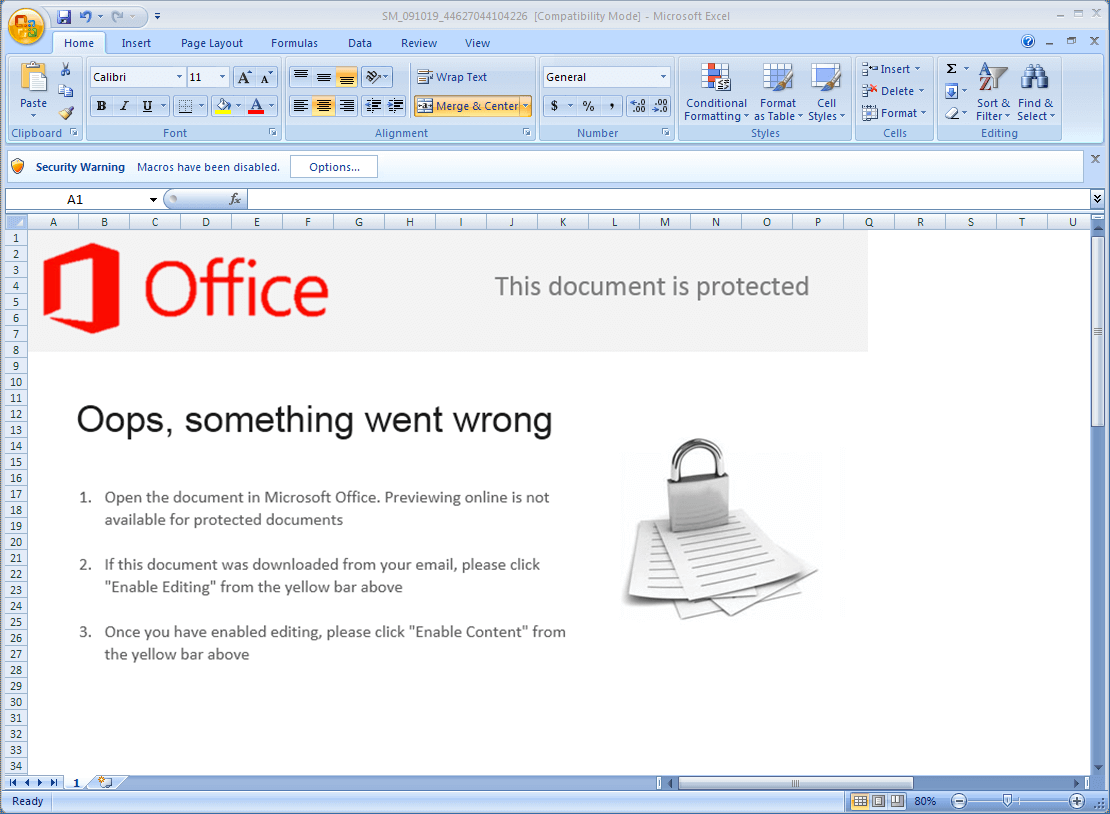
- Drops embedded XLSX to the Windows temporary directory as 13.xlsx
- Renames XLSX file 13.xlsx.zip
- Extracts either carpc2.dll for 64-bit or carpc2.dll for 32-bit Windows
- Loads the extracted DLL with LoadLibrary API and calls the Get2 export function
DLL Behaviour
- Once loaded, the DLL decrypts a needed function, which also decrypts and decompresses the main DLL at runtime.
- The 32-bit main DLL is packed with UPX unlike the 64-bit version which is not.
- The main DLL will then gather the following information from the affected system:
- Computer Name
- User Name
- OS Version
- Currently running process names
- This information is then used as parameters for the beacon to its server/s
- Depending on the server’s response, it may attempt to download and execute a final payload into the affected system.
URL Parameter format
&D=<COMPUTERNAME>&U=<USERNAME>&OS=<OS VERSION>&PR=<URL ENCODED PROGRAM NAME LIST>
Example:
&D=PWNM3&U=M3PWN&OS=6.2&PR=ApplicationFrameHost%2eexe%7cMSASCuiL%2eexe%7cMicrosoft%2ePhotos%2eexe%7cOneDrive%2eexe%7cRuntimeBroker%2eexe%7cSearchUI%2eexe%7cShellExperienceHost%2eexe%7cSystemSettings%2eexe%7cdllhost%2eexe%7cexplorer%2eexe%7cida%2eexe%7cjusched%2eexe%7cloaddll%2eexe%7collydbg%2eexe%7cprocexp%2eexe%7cprocexp64%2eexe%7csihost%2eexe%7csvchost%2eexe%7ctaskhostw%2eexe%7ctbzrcache%2eexe%7cvmtoolsd%2eexe%7c
User-Agent
Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 5.1; Trident/4.0; .NET CLR 1.1.4322; .NET CLR 2.0.50727; .NET CLR 3.0.4506.2152; .NET CLR 3.5.30729; InfoPath.2; CIBA; MS-RTC LM 8)
Indicators of Compromise and Cyren Detections
| Object ID | Object Type | Subject/Filename/Remarks | Region | Cyren Detection/s |
| ad324e00e98a9997fa37d69cf35eede21f12bdf8cc4e00158856f2fb46fc7153 | INSTRUKCIJE | W32/Agent.BEH.gen!Eldorado | ||
| 81eb3102810bd069ea810ada270eebaea22c20c423de565608a928010a0b806a | OLE Workbook | Inv.2019.xls | W32/Agent.BEH.gen!Eldorado | |
| df7b6fef7a8050598c3a94a7aa97f49fa1aa89d04a49b03a3ef40e7842172ccd | Win32 DLL | carpc1.dll | W32/Agent.BEH.gen!Eldorado | |
| b41def8d777a13dd709bfbb2b46f572ed69d08263e98a6868de5751b4b015bd4 | Win64 DLL | carpc2.dll | W64/Agent.BEH.gen!Eldorado | |
| hxxps://update365-office-ens[.]com/rb8 | URL | Malware Host | W64/Agent.BEH.gen!Eldorado | |
| 3f13c868705e6b09194d2a5db4fc3a2bc991de718f4a4e89ae08f21fbacb34e6 | Payment information | W32/Agent.BEH.gen!Eldorado | ||
| 8fbcc5e457c4e223148820cf4a1b6f760c819bf0bf0b5c61b92dcf8d5f8b5805 | OLE Workbook | PMT_2387718626_200054047_201112170000.xls | W32/Agent.BEH.gen!Eldorado | |
| 24bfc5cb1ec25bd914d5561a9972f50ea4da6aae9013e2c9c0f7e19fd02d1d31 | Document for Signature | W32/Agent.BEH.gen!Eldorado | ||
| 025a5d51b42f1c8868881d18a6043511c6dffdc402a4eefd988957e924711396 | OLE Workbook | SM_091019_44627044104226.xls | W64/Agent.BEH.gen!Eldorado | |
| 27a328a7a46f6d6ad5e09accb2d1d54d53763645c3c479adef4b44df2e01f314 | Document for Signature | W32/Agent.BEH.gen!Eldorado | ||
| 37e84a72f10d6776cdc73da0acabbc54d155f10e9ee1582b6355657b00740c42 | OLE Workbook | SM_091019_33138272845852.xls | W64/Agent.BEH.gen!Eldorado | |
| 120721eb9a6b01afd9a7c2396b272216fe418da8495fa05cf89d4bf07d72f18f | Document for Signature | W32/Agent.BEH.gen!Eldorado | ||
| df7316a4fb5b69a98bd2fc13c2feb5e3cb2b66e78e1f9edf153f35e7859c7b5e | OLE Workbook | SM_091019_10207745772443.xls | W64/Agent.BEH.gen!Eldorado | |
| cf6ea94045e1c617740a868b63cf5ce1ac852847b3a65f31b45fe498fd2377ef | Psr: Emailing: SKM_C78700614072127.xls | W32/Agent.BEH.gen!Eldorado | ||
| 19cf85cd5b43237c2aa22af41435e052c99eba5383768df3acdb60c1d664c8dc | OLE Workbook | SKM_C78700614072127.xls | W64/Agent.BEH.gen!Eldorado | |
| dbcbb94f1ca2893d05d6a71cca719bff01ae4ce4a35060e9f78a8bfaa523d122 | Scanned | W64/Agent.BEH.gen!Eldorado | ||
| 836d893a99137a0944d02caddea626586ce0ae081acfe2476997ebb2e6b49bc1 | OLE Workbook | scan0880.xls | W64/Agent.BEH.gen!Eldorado |
If you are thinking about evaluating new email security services, why not try Cyren’s Email Security Gap Analysis assessment, which is easy to deploy alongside your existing email security and free of charge to qualifying companies.
