Has the success of Microsoft Office 365 exacerbated the already complex task of purchasing email security? New Buyer’s Guides give a framework and provide a checklist to get it right.
Over the last few years, the way businesses use technology has undergone a complete transformation, driven by two major trends — mobility and cloud application adoption.
At the same time, we are seeing constant evolution of internet threats, which when combined with mobility and cloud, is putting huge pressure on traditional security infrastructure. Cyber threats are becoming more frequent, sophisticated and evasive. The majority start with a malicious email, resulting in email security being one of the main focus areas for cyber security spend, second only to firewalls.
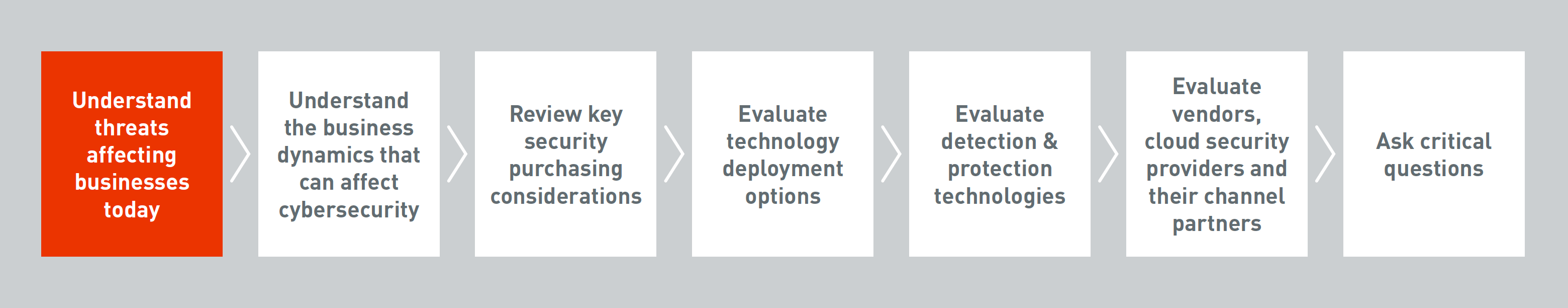
Figure 1: Framework for selecting email and web security solutions covered in new Buyer’s Guide
Office 365 Migration Creates Special Issues
Everyone who works in IT already understands this of course, but why suggest that Office 365 has any bearing on the email security buying process? There are two parts to the answer.
The first is that, through no fault of Microsoft’s, Office 365 is a victim of its own success. In much the same way that the popularity of Windows resulted in it being targeted by cyber criminals, as the number of Office 365 users increases rapidly, so do the threats specifically targeting those users. Cyren Security Lab research into phishing kits available on the dark web found that kits that phish for Office 365 credentials comprised 25% of the total number being sold. As a consequence, IT and information security professionals with Office 365 deployed are increasingly finding themselves challenged to ensure their email security controls protect their users, company, business partners and customers.
The second part of the answer is related to this challenge. The choices available to those evaluating email security products and services today are many and confusing. For companies that have migrated to Office 365, the inclusion of some bundled, basic email security exacerbates the complexity of this process.
Buyer’s Guides Now Available to Navigate Complexity
Large enterprises are having their fair share of difficulty in defending against modern internet threats, but they are (more likely than not) advantaged in terms of planning resources. They have dedicated security teams who assess their security posture and understand the technical, process and people controls that they need to put in place to mitigate the risks to the business. If well-organized, they are able to specify required functionality and work with the messaging infrastructure and operations teams to evaluate products and services.
Smaller and mid-sized enterprises will often not pursue the same depth of analysis and planning, as they are likely more budget and resource constrained.
Here at Cyren we do believe that the email security buying process has become more difficult, so to help those needing to cut through the complexity we have created a 27-page buyer’s guide specifically for Office 365 customers, as well as a general buyer’s guide relevant for those looking for any system, along with other resources also available at those links.
