Anatomy of an Attack: Evasive Zoom phishing campaign using multiple phishing techniques at once
In the final days of November, Cyren Inbox Security detected a massive phishing attack with a fake Microsoft 365 login page. Interestingly, they used many techniques to make the attack more evasive.
Related: Microsoft reports a “leap in attack sophistication”
The Attack
On Thursday, November 26, at 09:51 UTC, an immense phishing campaign started targeting more than two thirds of the organizations using Cyren Inbox Security at once. It became one of the biggest malicious attacks in November by the number of phishing emails totally distributed.
The emails were sent as if from a “Zoom” account ,while spoofing the target organization’s domain as a sender domain. This made the email look trustworthy, as if it was sent internally inside the enterprise. But once checking the authentication results, the sender mail address was spoofed:
- dkim=fail (no key for signature);
- dmarc=fail (failure in both SPF and DKIM);
- compauth=fail reason=601 (marked by Office365 ATP as spoofed).

Attackers used the SendGrid infrastructure for emails to reach the maximum number of victims’ mailboxes (sender IP is 168.245.36.62, which is a SendGrid mail server).
The email itself contained a message urging the recipient to “Review a video conferencing invitation.
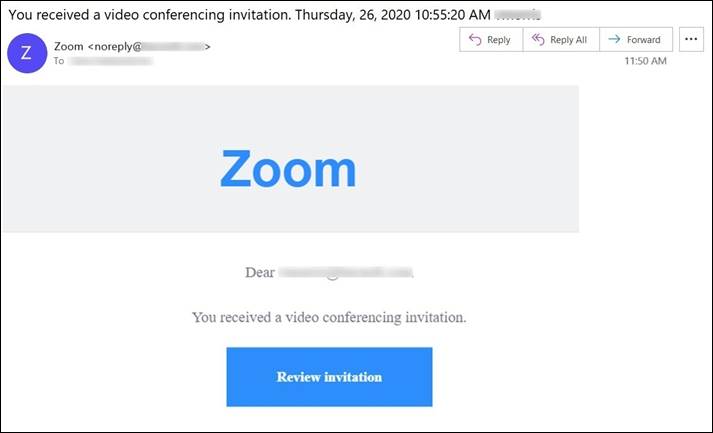
In order to “review invitation” the target would click on the phishing URL “hxxps://email.utest[.]com/ls/click?upn=” under the button. This query opened a fake Microsoft 365 login page hosted on an “appspot.com’”domain.
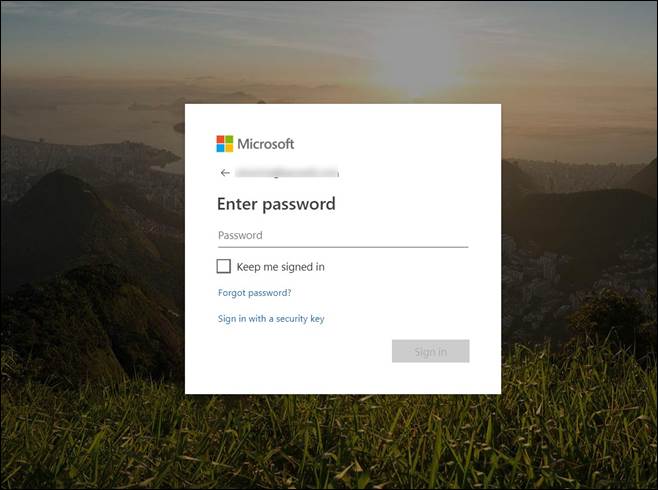
Example of the phishing landing page {hxxps://cebxbhilakscgyzdcjdilniduq-dot-chrome-backbone-296016.uc.r.appspot[.]com/?utm_campaign=website&utm_source=sendgrid.com&utm_medium=email#}
The phishing was distributed by abusing a high-Alexa uTest domain, which redirected to the URL with auto-generated subdomains hosted on another high-Alexa domain (appspot.com).
Each URL contained sendgrid.com as a UTM source, which attackers could misuse to visualize and measure the impact of the sent emails on the potential victim.
This phishing attack combined several techniques:
- abusing the high-Alexa popular domains (utest.com and appspot.com);
- leveraging SendGrid infrastructure;
- spoofing the target enterprise’s domain as mail sender,
which made it easier for the phishing emails to by-pass the existing security email filtering capabilities.
Cyren Inbox Security Detection
With Cyren Incident Response Service and its 24×7 support for phishing investigation, the attack was rapidly investigated and all the emails related to the attack were appropriately classified as phishing for all the Cyren Inbox Security customers. Learn more about Cyren Inbox Security >
