Phishing remains one of the most popular types of corporate attacks in terms of its prevalence, and therefore it is not surprising that attackers are coming up with increasingly sophisticated methods to obtain the victim’s personal data.
Signs of an Office 365 Phishing Attack
- A Warning from Microsoft: The warning usually states that you should call Windows support now at XXX-XXX-XXXX, creating a sense of urgency, however it will rarely say “Microsoft Support”. This warning might come up as partial or full screen, but will be hard to close the window. Clicking the close button usually won’t allow you to exit from the popup. You’ll have to end the task through task manager in order to close the alert box.
- A Prerecorded Audio: You may also hear a pre-recorded audio that announces the alert. These types of warnings have been reported on legitimate websites. While they are usually harmless, you will want to make sure you do not follow the instructions on the alert.
- Warning Messages: Your pop-up blocker will not be able to block these kinds of alerts. It’s best to try clearing your browser history once you encounter a message like this and then follow that up with an in-depth virus scan.
- Using Tried and True Methods: The best defense is educating your employees, filtering email & making sure everyone uses multi-factor authentication.
A Recent Office 365 Phishing Email Attack Example
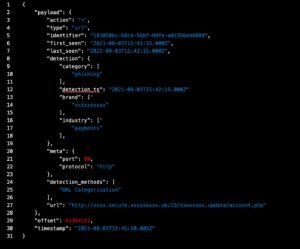
One of the most recent phishing attacks detected by Cyren Inbox Security was trying to gain the personal passwords of the emails’ recipients through the attached HTML page that appeared to be an Excel file titled ‘Microsoft Office Center’.
Employees of several organizations using Cyren Inbox Security solution started to receive emails sent from the automatically generated email addresses all hosted on the compromised <server5.fngnetde-dns.com> sender domain.
The sender’s display name mirrored the targeted organization <[Company] Invoicé Repoŕt> and the subject prompted ‘Invoiće ID:XXXXXX is ready for paymeńt’. Phishers cleverly used the special characters in the subject and display name (é, ń) in order to minimize the chances of the automatic email spam filtering by the “Invoice” and “payment” keywords.
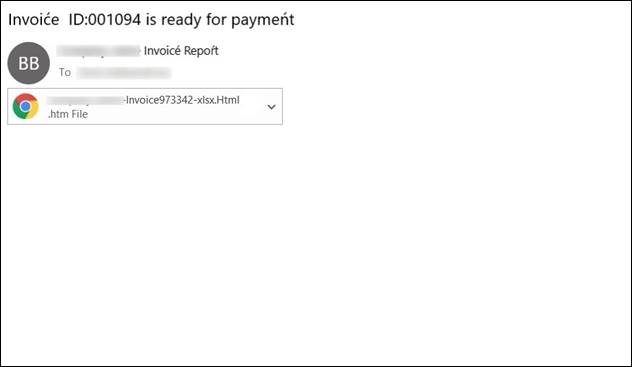
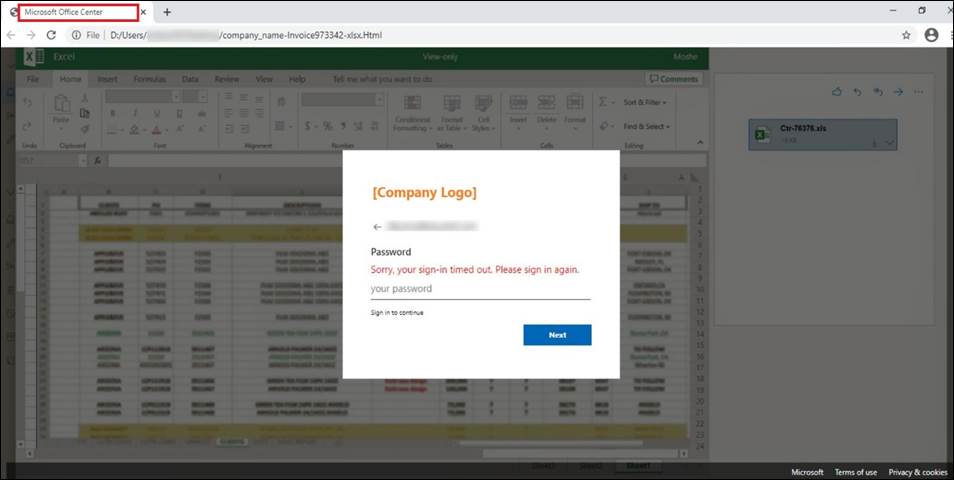
Email body was empty, but the email contained an HTML attachment passing for the xlsx file of an invoice mentioning the specific targeted company in its name, increasing the chances of the recipient to open the file. Once opened, the fake login page titled ‘Microsoft Office Center’ on the Excel background appeared aiming to steal the user’s password.
Visually, this attack looks identical to the one mentioned in the recent article by Bleeping Computers, where Morse code is used in the HTML attachment code to hide a phishing URL. But in this case, instead of the Morse code in the HTML attachment, the obfuscated Javascript code is used which makes it harder to unveil its true purpose until it is executed.
The script contained a separate function personalizing the visuals of the phishing campaign:
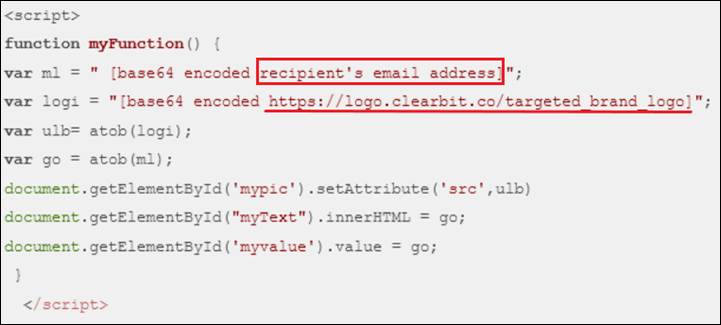
The ml variable was responsible for the recipient’s email address, and the var logi added the targeted brand logo image onto the phishing page. The images were taken from the logo.clearbit.com – a legitimate Logo API tool from Clearbit in which hundreds of company logos are freely available. This script not only makes the attack personalized but also significantly expands the potential number of affected companies by the attacker changing the logo variable only.
The password field on the HTML attachment is responsible for stealing personal information. This is executed in a PHP form with method post and action URL that would send all the inserted credentials and password information to the attacker:
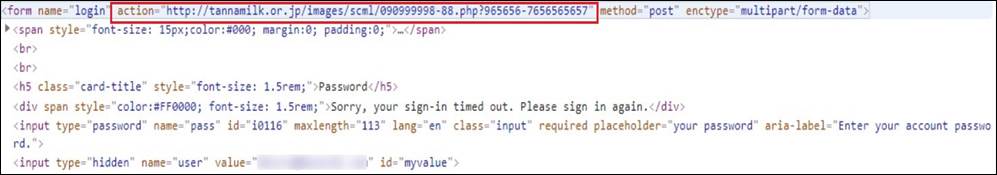
The action URL is exploiting the legitimate Japanese site for its hostile purposes: enctype=”multipart/form-data” which indicates that all the submitted login and password information would have been divided into multiple parts and sent to the phishing server.
Cyren Inbox Security Detection
With Cyren Incident Response and its 24×7 support for phishing investigation, the attack was rapidly investigated and all the emails related to the attack were appropriately classified as phishing for all the targeted Cyren Inbox Security customers.
Discover a behind the scenes look at phishing kits.