Cyren caught a new Locky email spam campaign today which uses a new tactic, delivering the Locky downloader script component as an HTML application, specifically HTA files. The emails are disguised as voice message notifications sent by Peach Telecom, which suggests that the campaign is targeting users in the UK.
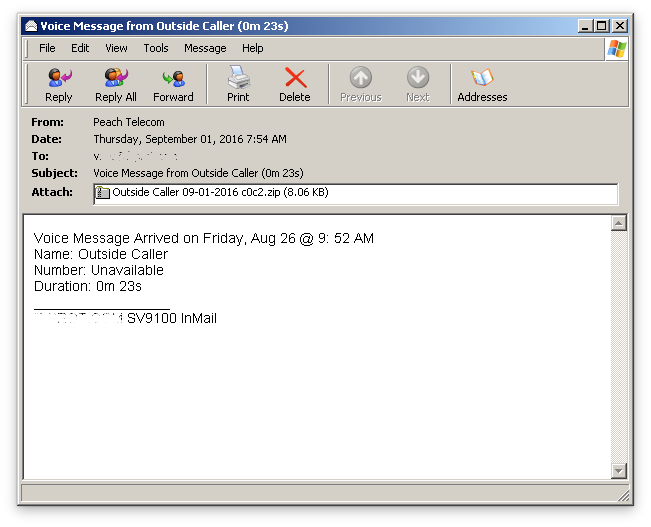
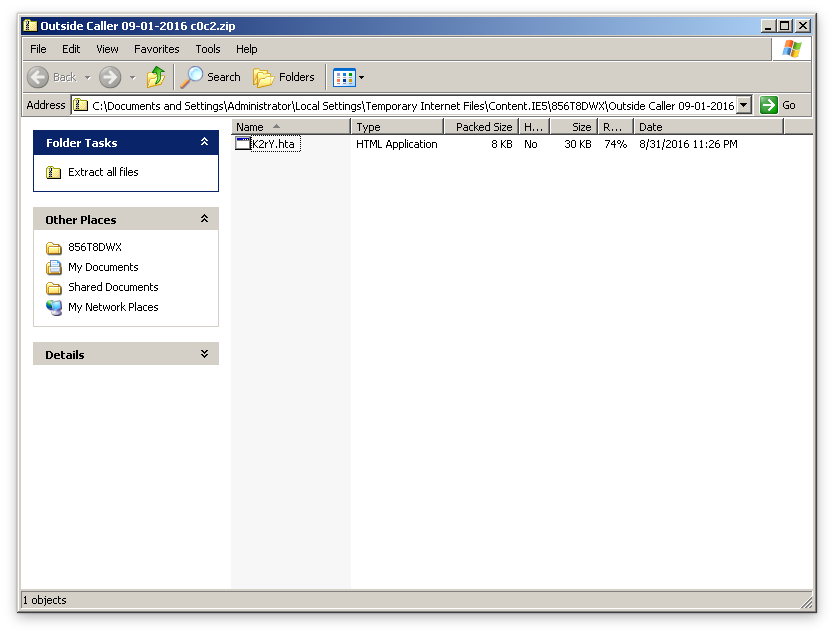
HTA files are loaded by the system using the program MSHTA.exe, and are executed by instantiating the Internet Explorer rendering engine (MSHTML) along with the required script engines such as jscript.dll and vbscript.dll.
Opening the HTA file in a text editor shows use of the JScript language, which is used in most of the Locky campaigns. Cyren detects this downloader script variant as JS/Locky.AY.
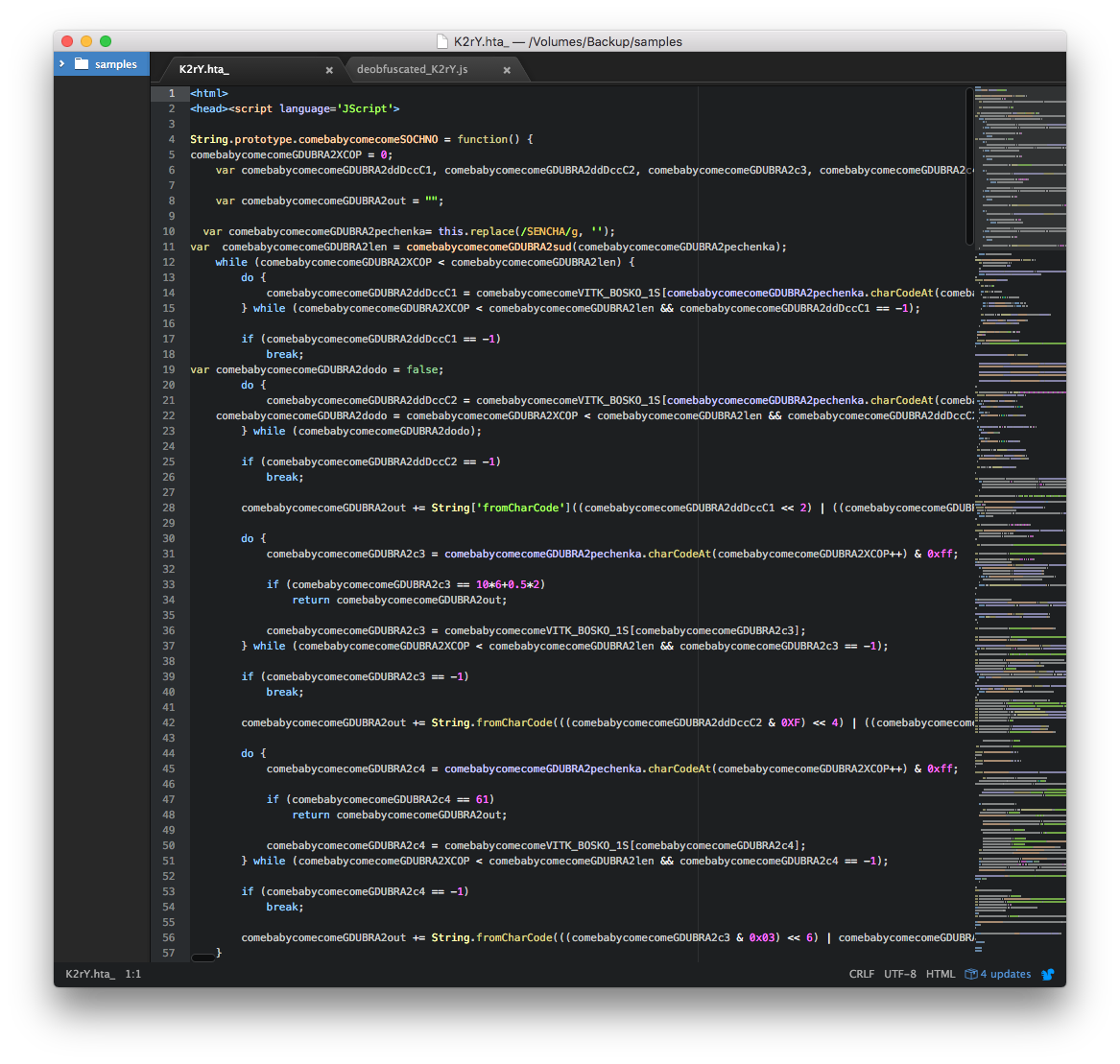
Deobfuscating part of the code shows a decryption code structure similar to what we saw in the previous Locky samples we have analyzed.
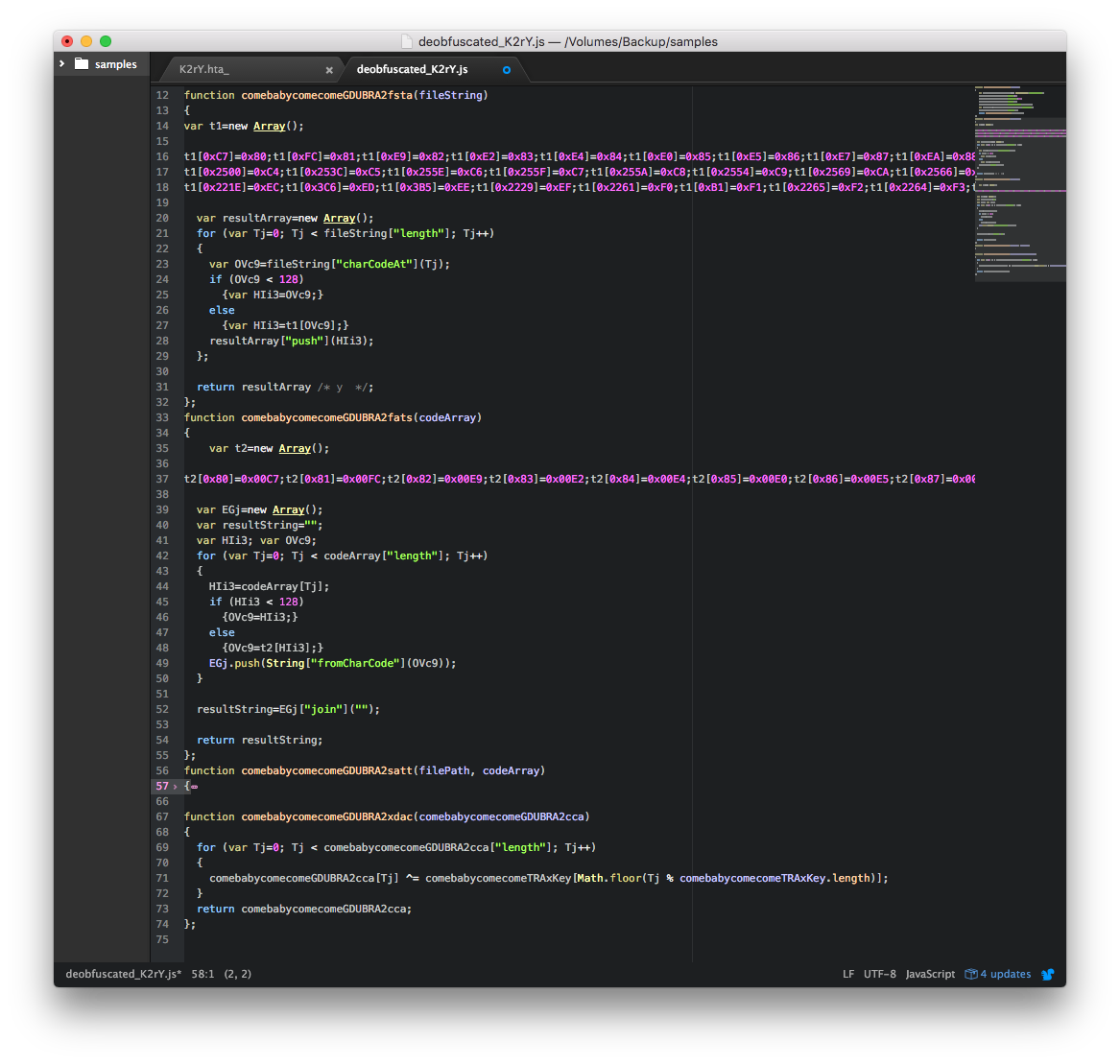
Each sample has at least four URLs from which it tries to download, and as usual the downloader script decrypts before executing.
Similar to the variant we reported last week, the decrypted ransomware component is a DLL file and is loaded using rundll32.exe. We also observed that it no longer uses a code parameter along with the called export function.
CYREN detects the decrypted DLL as W32/Locky.IA.

And just like the previously reported variant, this ransomware component finds and encrypts files in the affected system, renaming the files and appending the string “.zepto” as the file extension.
Listed below are the files which are searched for and encrypted by this variant.
.n64 |
.ltx |
.gif |
.c |
.lay |
.xltx |
.pdf |
.m4a |
.litesql |
.raw |
.php |
.ms11 (Security copy) |
.xltm |
.XLS |
.m4u |
.litemod |
.cgm |
.ldf |
.ms11 |
.xlsx |
.PPT |
.m3u |
.lbf |
.jpeg |
.mdf |
.sldm |
.xlsm |
.stw |
.mid |
.iwi |
.jpg |
.ibd |
.sldx |
.xlsb |
.sxw |
.wma |
.forge |
.tif |
.MYI |
.ppsm |
.slk |
.ott |
.flv |
.das |
.tiff |
.MYD |
.ppsx |
.xlw |
.odt |
.3g2 |
.d3dbsp |
.NEF |
.frm |
.ppam |
.xlt |
.DOC |
.mkv |
.bsa |
.psd |
.odb |
.docb |
.xlm |
.pem |
.3gp |
.bik |
.cmd |
.dbf |
.mml |
.xlc |
.p12 |
.mp4 |
.asset |
.bat |
.db |
.sxm |
.dif |
.csr |
.mov |
.apk |
.sh |
.mdb |
.otg |
.stc |
.crt |
.avi |
.gpg |
.class |
.sql |
.odg |
.sxc |
.key |
.asf |
.aes |
.jar |
.SQLITEDB |
.uop |
.ots |
wallet.dat |
.mpeg |
.ARC |
.java |
.SQLITE3 |
.potx |
.ods |
|
.vob |
.PAQ |
.rb |
.011 |
.potm |
.hwp |
|
.mpg |
.tar.bz2 |
.asp |
.010 |
.pptx |
.602 |
|
.wmv |
.tbk |
.cs |
.009 |
.pptm |
.dotm |
|
.fla |
.bak |
.brd |
.008 |
.std |
.dotx |
|
.swf |
.tar |
.sch |
.007 |
.sxd |
.docm |
|
.wav |
.tgz |
.dch |
.006 |
.pot |
.docx |
|
.mp3 |
.gz |
.dip |
.005 |
.pps |
.DOT |
|
.qcow2 |
.7z |
.pl |
.004 |
.sti |
.3dm |
|
.vdi |
.rar |
.vbs |
.003 |
.sxi |
.max |
|
.vmdk |
.zip |
.vb |
.002 |
.otp |
.3ds |
|
.vmx |
.djv |
.js |
.001 |
.odp |
.xml |
|
.wallet |
.djvu |
.h |
.pst |
.wb2 |
.txt |
|
.upk |
.svg |
.asm |
.onetoc2 |
.123 |
.CSV |
|
.sav |
.bmp |
.pas |
.asc |
.wks |
.uot |
|
.re4 |
.png |
.cpp |
.lay6 |
.wk1 |
.RTF |
After encrypting the files, the desktop wallpaper is replaced with the ransom instructions and the ransom instructions page is loaded.
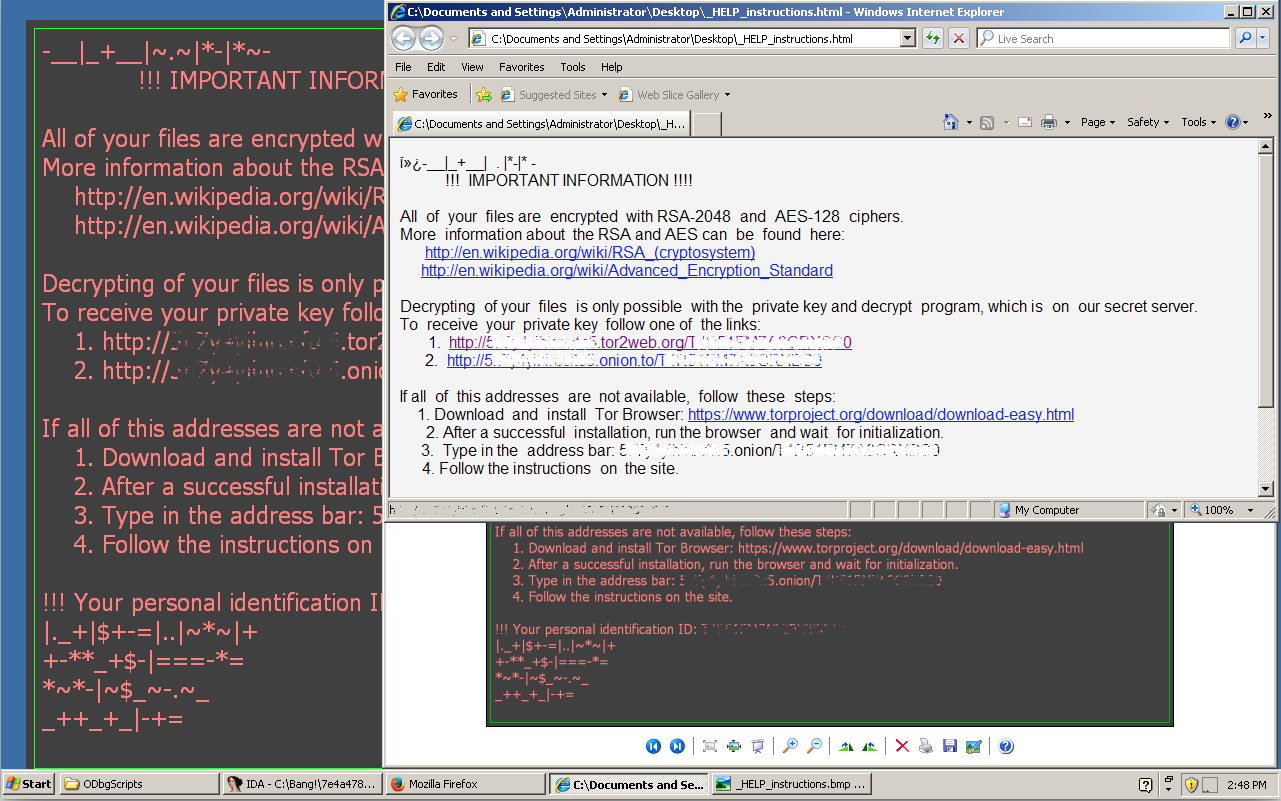
Clicking on the tor links redirects the users to the Locky decryptor page.
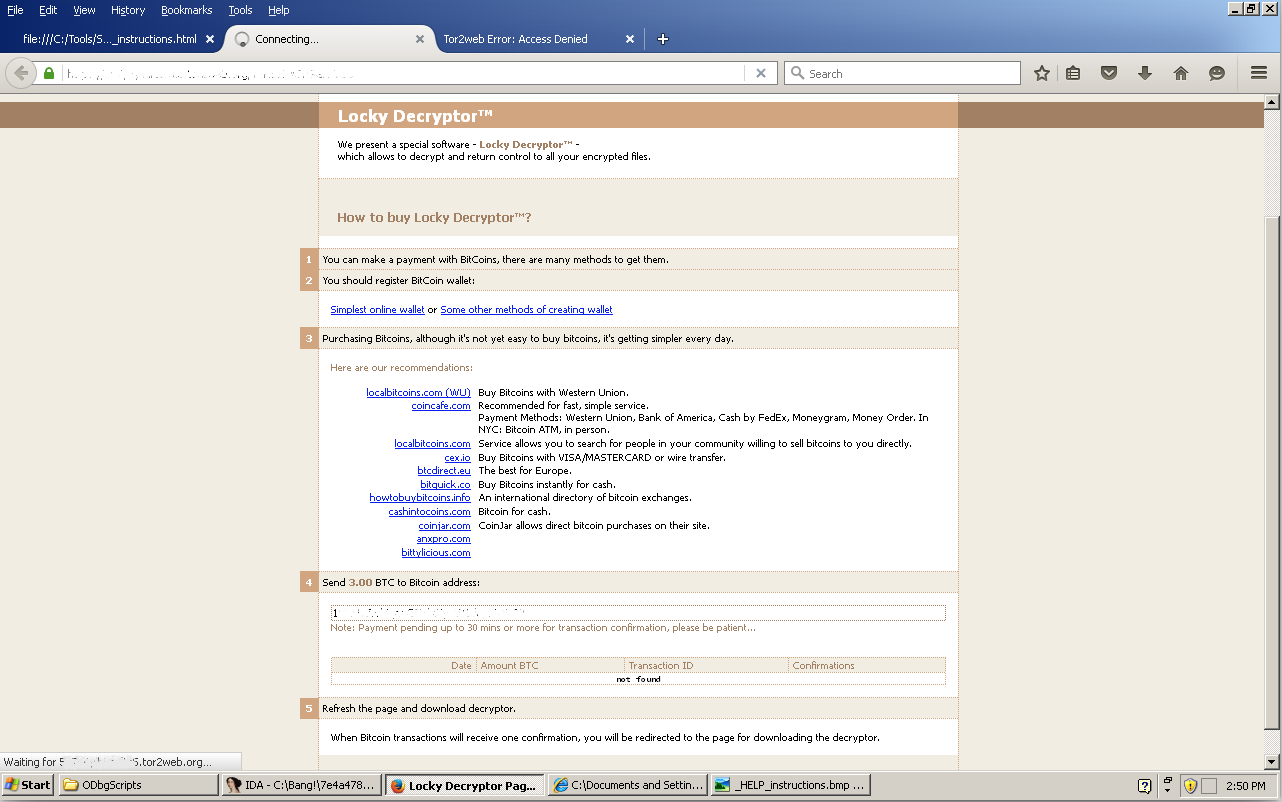
While reviewing the domains of the download URL’s, we found one particular domain, which was recently created and was registered using the email galicole@mail.com.
WhoIs Info
Domain Name: HOTCARSHHHS6632.COM Registry Domain ID: 2056315296_DOMAIN_COM-VRSN Registrar WHOIS Server: whois.publicdomainregistry.com Registrar URL: www.publicdomainregistry.com Updated Date: 2016-08-31T09:34:43Z Creation Date: 2016-08-31T09:34:42Z Registrar Registration Expiration Date: 2017-08-31T09:34:42Z Registrar: PDR Ltd. d/b/a PublicDomainRegistry.com Registrar IANA ID: 303 Domain Status: clientTransferProhibited https://icann.org/epp#clientTransferProhibited : : : Registrant Email: galicole@mail.com
This registrant email has a history of registering domains for the binary payload of Locky Ransomware in August:
rejoincomp2.in tryfriedpot.co.in
File Hashes
EML 1df85dba3870318dbecc9dc6cb7a3d49e61bf2a89eeb28b2e4c5dce824bd55e7 HTA 36a2055152cb61411d1275fc53cd659a72e66399f59a312013edcfa4cecd9bfd DLL ed8965e9834248a177fd0062149410c63c612d68518aff31b35eb58a33b6ce59
URLs being used
hxxp://portadeenrolar.ind.br/jtfinwo?OIxbvVT=NWocFL hxxp://hotcarshhhs6632.com/js/76g78uf4sw?rQrPsyExOz=ethvMq hxxp://fingermousedesign.co.uk/ctkvyio?rQrPsyExOz=ethvMq hxxp://www.primaria-adamclisi.go.ro/ueeldwe?nPPrVCPinPp=zrdPHU hxxp://www.trade-centrum.eu/ibghgdp?scYkAI=uRPKpwONAus hxxp://209.41.183.242/adjxlax?scYkAI=uRPKpwONAus hxxp://wapnn.vov.ru/ummvyia?XCmHOiPueIj=TEqUHJAH hxxp://albertowe.cba.pl/rejsill?xDVbhWSzARn=QFdSrnvoQsS hxxp://hotcarshhhs6632.com/js/76g78uf4sw?XCmHOiPueIj=TEqUHJAH hxxp://www.association-julescatoire.fr/yjqhgff?XCmHOiPueIj=TEqUHJAH hxxp://www.alpstaxi.co.jp/therodk?IKmacGFG=ddrSDzk hxxp://yggithuq.utawebhost.at/opdcrhh?OIxbvVT=NWocFL hxxp://www.trauchgauer-weihnachtsmarkt.de/frcmmhv?IKmacGFG=ddrSDzk hxxp://www.dietmar-bernhard.de/rthvkws?nPPrVCPinPp=zrdPHU hxxp://www.ediazahar.com/mllpeqd?xDVbhWSzARn=QFdSrnvoQsS hxxp://pennylanecupcakes.com.au/lfigasv?UlXIkkwe=kIkGHdxeh hxxp://www.btb-bike.de/psoexes?UlXIkkwe=kIkGHdxeh hxxp://hotcarshhhs6632.com/js/76g78uf4sw?OIxbvVT=NWocFL hxxp://pennylanecupcakes.com.au/lfigasv?OIxbvVT=NWocFL hxxp://www.rioual.com/bddoxvg?UlXIkkwe=kIkGHdxeh hxxp://hotcarshhhs6632.com/js/76g78uf4sw?nPPrVCPinPp=zrdPHU hxxp://www.trauchgauer-weihnachtsmarkt.de/frcmmhv?XCmHOiPueIj=TEqUHJAH hxxp://hotcarshhhs6632.com/js/76g78uf4sw?xDVbhWSzARn=QFdSrnvoQsS hxxp://wapnn.vov.ru/ummvyia?IKmacGFG=ddrSDzk hxxp://www.trade-centrum.eu/ibghgdp?rQrPsyExOz=ethvMq hxxp://www.btb-bike.de/psoexes?xDVbhWSzARn=QFdSrnvoQsS hxxp://ajedrezimprov.50webs.com/yfotxbo?nPPrVCPinPp=zrdPHU hxxp://hotcarshhhs6632.com/js/76g78uf4sw?UlXIkkwe=kIkGHdxeh hxxp://www.primaria-adamclisi.go.ro/ueeldwe?scYkAI=uRPKpwONAus hxxp://portadeenrolar.ind.br/jtfinwo?rQrPsyExOz=ethvMq hxxp://hotcarshhhs6632.com/js/76g78uf4sw?scYkAI=uRPKpwONAus hxxp://hotcarshhhs6632.com/js/76g78uf4sw?IKmacGFG=ddrSDzk
To get further up to speed on Locky, download Cyren’s special threat report:
We also previously reported our detection of key changes in Locky’s methods on:
- June 27 (new sandbox evasion techniques),
- July 4 (new downloading technique),
- July 14 (attachment format change), and most recently
- July 21 (embedded in JavaScript).
