Viral pandemics are certainly cause for a hospital to declare a “state of emergency.” But in the case of Methodist Hospital in Kentucky, the virus that caused the “internal state of emergency” didn’t relate to hundreds of patient-filled stretchers…
In this instance, Locky had infected the hospital’s entire computer system, forcing the hospital to pay four bitcoins (approximately $1,600) to obtain the decryption key!
Methodist Hospital wasn’t the first medical facility to feel the bitcoin bite; earlier this year, another California-based hospital system was forced to pay $17,000 in bitcoins as a result of another ransomware attack that infected their networks. Other medical centers to be infected include MedStar Health, which operates in the Washington, DC metro area, as well as Desert Valley Hospital and Chino Valley Medical Center, both in California. Law firms, tax and accounting businesses, and police departments are also reporting ransomware attacks.
A Day in the Life of Locky
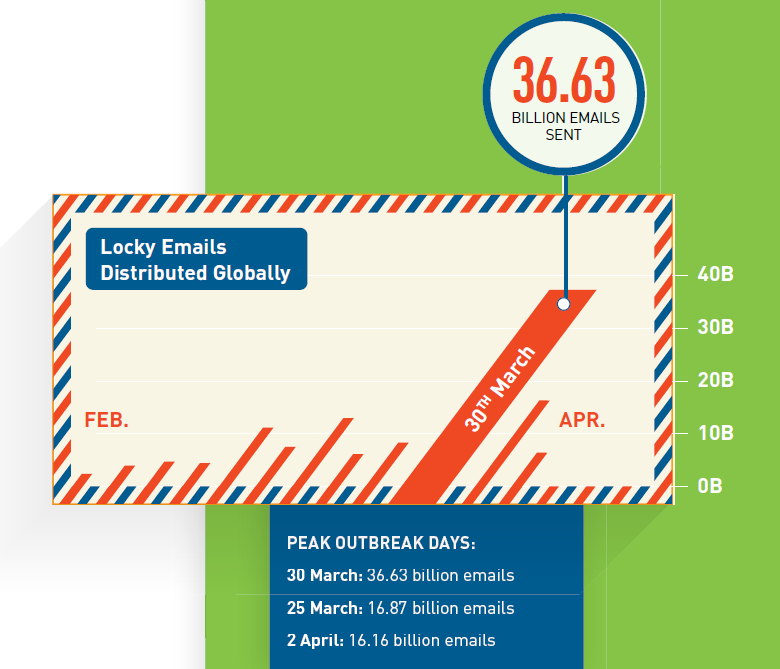
Since its initial launch, CYREN researchers have observed phenomenal expansion in the Locky distribution rates:
The surge of Locky-infected emails occurred primarily during weekdays and between working hours (attacks are usually 12:00 – 20:00 UTC), suggesting the campaign targets email recipients who are most likely at work in North America, South America, or Europe.
Some numbers:
- On March 31, CYREN’s honeypots saw 1.5 million unique JavaScript samples in a 24-hour period.
- During a seven-hour period, Locky-JavaScript variants represented 90% of all malware-embedded email traffic through CYREN systems.
- Over 1 million unique URLs were used to host the malware.
- Ransom varies between $200 – $20,000
Any Organization That Provides a Critical Public Service is at Increased Risk
According to the Vice President of CYREN’s Antivirus Platform, Sigurdur Stefnisson, any organization that provides a critical public service is at increased risk. “Organizations that provide services that directly affect peoples’ lives, are perfect targets for ransomware. Criminals know that medical professionals and police departments can’t afford to have their mission-critical systems shut down when people’s health is at risk. By the same token, the last thing a tax accountant wants during April is ransomware blocking his ability to finish tax filings for his clients.”
What Can Businesses Do?
Prevent and protect using a combination of common sense Internet security practices and employing cybersecurity services like email gateways and web security from companies that offer the benefits of mass-scale analysis and updates.
Learn more about Locky and Ransomware: CYREN May 2016 Cyberthreat Report – Free Download