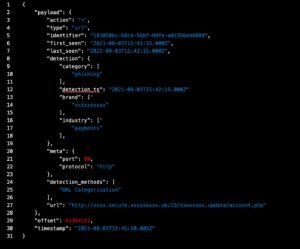
Key Points:
- Smishing is causing millions of dollars in losses.
- Robokiller insights show that consumers have received over 12 billion in robotexts.
- Fraudsters are smart people who are very good at designing texts that make people take immediate action.
- When receiving a text message that claims to be from your bank, the best thing to do is to delete it and avoid clicking on any links.
What is Smishing?
Before we dive deeper into our main topic, let us first define Smishing. Smishing, a term that combines SMS and Phishing, is a form of phishing, which is delivered via Short Message Services (SMS) or better known as text messages on the mobile platform.
Smishing scammers are always on the lookout for new ways to steal your information. When you get an SMS claiming that it’s from your bank or another financial institution, something is going on, and precautions should be taken. Text messages from banks asking to confirm account details, reset passwords, or contain links should be completely avoided. Banks will typically leave requests with more traditional means such as phone calls or within their platform.
How Does Smishing Work?
Like phishing in general, smishing attacks are executed with an intent to steal personal information or credentials such as social insurance, credit card numbers and/or online banking login information. It often involves social engineering attacks, which exploit human trust, since people are more likely to trust messages received through SMS on their phone than from other online platforms such as emails or social messaging apps.
Smishing attacks commonly use messages disguised as notifications from legitimate companies such as banks, credit card companies or even government agencies. These messages often include clickable links that lead to phishing websites in attempts to lure victims into exposing non-public personal information or even login credentials.
Learn more about “industry” trends, and how phishing kits work.
Understanding Smishing: The Steps to an Attack
Let’s break down the Smishing message into parts to learn how such an attack may prove effective to some users.
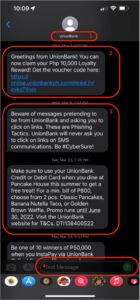
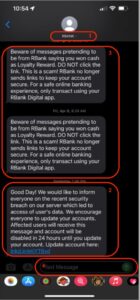
Figure 1 Smishing message broken into parts
As shown in the images above, a Smishing message can be broken into the following parts:
1. Sender ID
In most cases, when you receive an SMS from an unknown sender, the Sender ID would show phone number in either an international (country code-area code-phone number) or a domestic (area code-phone number) format. However in this case, the Sender ID is shown to be using the bank’s name or what we call a custom word or brand id.
2. Smishing Message
This message is a socially engineered notification that entices a user to click on a malicious link included in the text message.
3. Legitimate Messages
Notifications are then sent out by the legitimate organizations, which in this case are banking institutions.
4. Disabled Response
Recipients of the message cannot reply to messages to this type of SMS.
What Kinds of Text May Be Used?
In the case of smishing attacks, the banking institutions are using A2P (application to person) messaging to send OTP, advertisements, promotions and/or notifications to their clients. This refers to any kind of messaging traffic where a person receives messages from an application, which includes marketing messages, chat bots, notifications, one-time-passwords (OTP) or pin codes, appointment reminders and more.
Now you might wonder, how did cyber criminals hijack banking notification messages in this smishing campaign? This is where the Sender ID comes into play.
When you receive an SMS message, you would usually see the sender ID as a phone number if you haven’t saved and named it in your phone book. However, in A2P messaging, a sender ID can be viewed as any of the following Sender ID types:
1. Custom Sender ID – custom alphanumeric words that can use up to eleven (11) characters. This could be any word or phrase a business deems suitable for their purpose such as business/brand name.
2. Dedicated Numbers – a virtual number consisting of up to 16 digits, which is unique to a certain business/organization.
3. Shared Numbers – similar in format to a dedicated number but it is not unique to one business/organization.
In this smishing campaign, cyber criminals took advantage of using custom Sender IDs to slip their malicious messages into existing A2P message history from legitimate banks in a person’s mobile phone by simply using the same custom sender ID used by the banks they are spoofing. By doing this, the cyber criminals can easily manipulate bank clients into trusting their messages and eventually lure them into their malicious scheme. There are several methods to accomplish this scheme, but the most common and widely available is to use a paid SMS gateway service that allows the use of custom sender ID and sending of bulk SMS messages using an API.
How to Prevent Smishing Attacks
In a world where mobile/online banking is no longer available just for convenience but more for necessity, more and more people are relying on online mobile devices for day-to-day transactions. Naturally, cyber criminals keep finding ways to abuse these situations to get their hands on people’s hard-earned money. Here are a few ways to reduce the chances of falling victim to a smishing campaign.
1. Keep Your Personal Information Private
One of the best ways to protect yourself from smishing scams is to keep your personal information private. This includes your Social Security number, bank account information, credit card numbers, and birth date. Be wary of any text message or email that asks you for this type of information, as it is likely a scam.
2. Do Not Respond to Suspicious Text Messages
If you receive a text message from an unknown number or from a number that looks suspicious, do not respond to it. Scammers will often try to get people to respond to their messages so that they can then use that response to steal your personal information, make educated login attempts, or confirm that the number is at least active to continue sending you repeated text messages.
3. Do Not Click on Links in Suspicious Text Messages
Another way scammers try to steal your personal information is by including links in their text messages that lead to fake websites. These websites may look like legitimate companies, but they are designed to trick you into entering your personal information.
4. Be Wary of Free Offers
Scammers will often use smishing scams to try to get people to sign up for free offers, such as free trials or contests. These offers may seem legitimate and enticing at first, but they are often just traps designed to steal your personal information. If you receive an offer that seems too good to be true, it probably is.
5. Do Not Respond to Threats
Smishing scams will often include threats in an attempt to get people to respond quickly without thinking about the consequences. For example, a scammer may threaten to cancel your credit card if you do not provide them with your account information immediately. Do not respond to these threats, instead, report them to the proper authorities.
6. Ignore Requests for Money
Scammers will sometimes use smishing scams to try to get people to send them money. They may claim that you owe them money or that they need money for an emergency situation that needs to be resolved. Regardless of the reason they give, financial transactions should always be handled professionally and not by third-party applications.
7. Check Your Credit Report Regularly
One way to stay on top of smishing scams is to check your credit report regularly for any unauthorized activity. You are entitled to one free credit report from each of the three major credit bureaus every year. If you see any activity on your credit report that you did not authorize, contact the credit bureau and file a dispute.
8. Use Two-Factor Authentication Whenever Possible
Two-factor authentication is an extra layer of security that can help protect you from smishing scams and other types of fraud. With two-factor authentication enabled, you will be required to enter both your password and a code that is sent to your phone whenever you log into an account. This makes it much more difficult for scammers to access your account.
Smishing Campaign Examples (Bank Alert Text Scams)
Smishing Targeting Mobile Bank Users in the Philippines
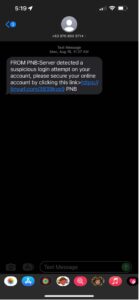
Figure 2. Smishing message spoofing Philippine National Bank (PNB)
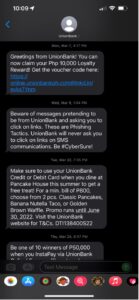
Figure 3. Smishing message spoofing Union Bank of the Philippines
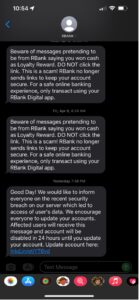
Figure 4. Smishing message spoofing Robinsons Bank Philippines
As shown in the SMS screenshots above, both attacks use deception and fraud as the attacker assumes an identity that a user would trust. In these cases, both are banking institutions known in the Philippines. Social engineering tactics are used by attackers to manipulate a person’s decision making by:
1. Masquerading as a legitimate individual or organization to gain trust. By doing the attack through a more personal communication platform, a person is more susceptible to lowering their guard against possible fraud.
2. Appealing to human’s greedy nature by offering benefits, such as rewards in the form of vouchers as shown in Figure 3.
3. Heightening one’s sense of urgency, affecting the person’s critical thinking and driving them into panic to quickly take action, such as a possible security breach as shown in Figure 4.
Let’s take a quick look into the links contained in the recent messages shown above.
Union Bank Loyalty Reward Voucher Scam
Enticing one’s interest with cash rewards is one way that cyber criminals lure mobile banking users to fall prey to their scams. In this campaign, the link hxxps://online[.]unionbankph[.]com@lnkd[.]in/eyks7Ynm, appears to be the legitimate link to Union Bank’s website. However, the real destination is the portion of the URL after the “@” character, which has been shortened with LinkedIn’s URL shortening feature. At the time of this writing, the shortened URL redirects to the legitimate banking website but using the developer tools network panel in the browser reveals a brief visit to a suspicious server before the user is redirected to the legitimate Union Bank web site:
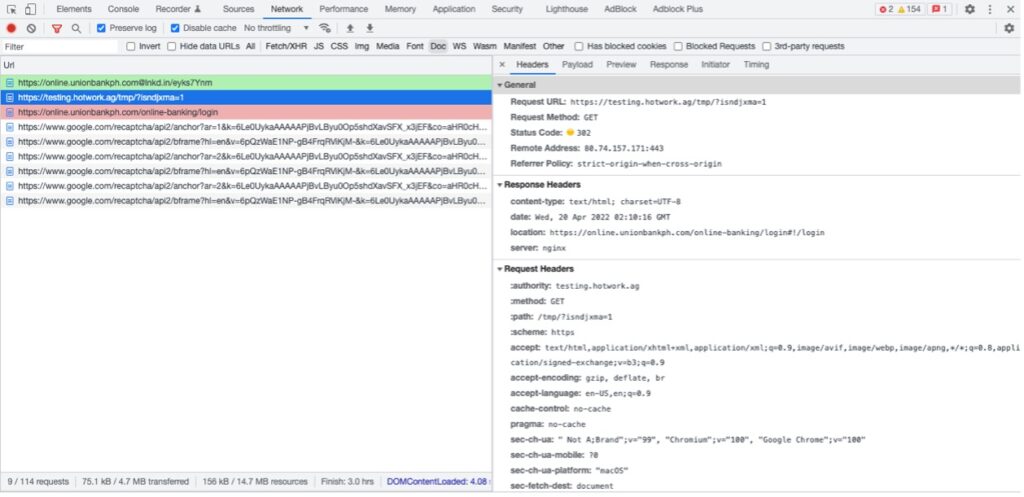
Figure 5 Initial redirection from LinkedIn shortened URL from UnionBank Smishing Campaign
Robinsons Bank Security Breach Scam
In this campaign, the attackers engage in fearmongering tactics to frighten the recipient of a “recent security breach” that may lead to accounts being disabled if they do not take action within a specified period of time. Apparently, this campaign also takes advantage of LinkedIn’s URL shortening service and initially redirects to the same third-party host used in the Union Bank campaign:
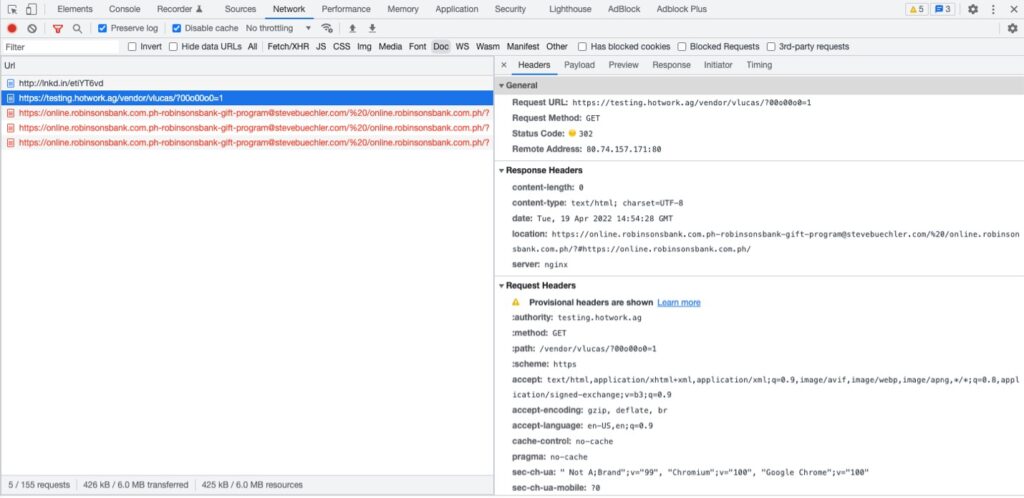
Figure 6 Initial redirection from LinkedIn shortened URL from Robinsons Bank Smishing Campaign
We were able to get a screen capture of the landing page for this campaign. It is clearly a phishing page masquerading as the bank’s login page:
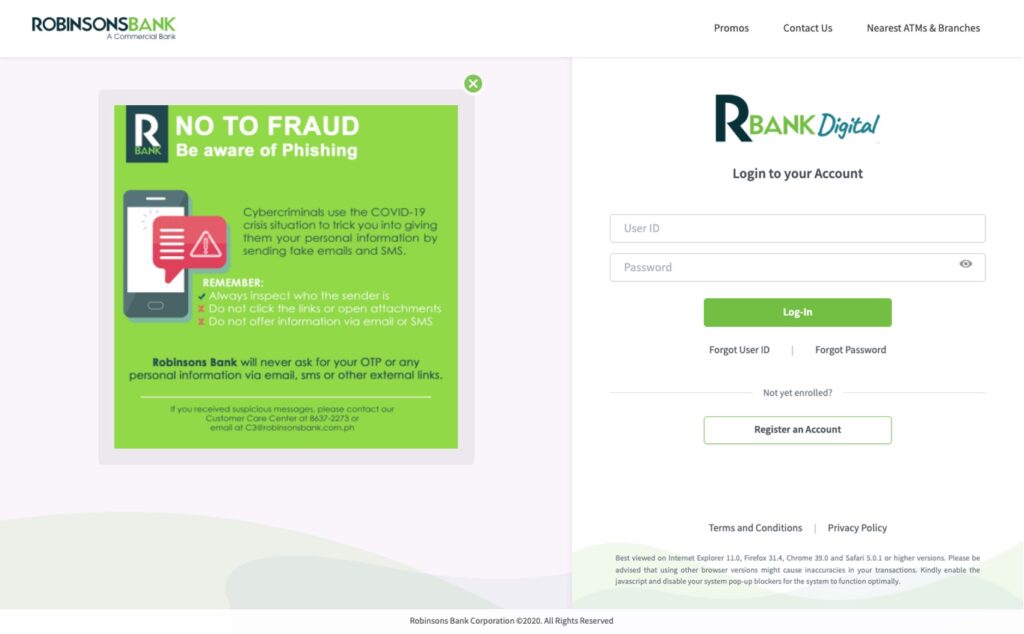
Figure 7 Phishing Page Imitating Robinsons Bank Login Page
Final Thoughts
With the information we have discussed in this post, we hope to encourage more people to be vigilant and think twice before clicking on links in SMS or text messages, even if they appear to be coming from legitimate sources. Avoid clicking on embedded links, especially those that use URL shorteners to obfuscate their true intent.
[/et_pb_text][et_pb_text _builder_version=”4.14.2″ _module_preset=”default” global_colors_info=”{}”]Indicators of Compromise
- hxxp://lnkd[.]in/etiYT6vd
- hxxps://testing[.]hotwork[.]ag/vendor/vlucas/?00o00o0=1
- hxxps://online[.]robinsonsbank[.]com[.]ph-robinsonsbank-gift-program@stevebuechler[.]com/%20/online[.]robinsonsbank[.]com[.]ph/?
- hxxps://online[.]unionbankph[.]com@lnkd[.]in/eyks7Ynm
- hxxps://testing[.]hotwork[.]ag/tmp/?isndjxma=1
Discover a behind the scenes look at phishing kits.