Phantom is a browser based crypto wallet where you can store, send, receive, stake and exchange tokens in the Solana blockchain. With the skyrocketing prices of crypto currencies including SOL, a crypto wallet is one of the things we can use in order to get into the crypto currency action.
Just recently there were several reports of wallets being wiped clean. An incident was reported by a user on twitter on how it happened. With just a copy/pasted message sent by a friend to a messenger group chat which includes a phishing link, he clicked it without verifying and it all went wrong from there.
And now, they are trying to run pay per click campaigns to target more unsuspecting users. We previously reported fraudsters using online advertising in a phishing campaign that targeted Axie Infinity users through a fake Ronin wallet page. Malicious ads are not uncommon and large ad platforms like Google have processes to identify and remove fraudulent content. However, we were able to spot a fraudulent ad before it was quickly spotted and removed by Google.
In this campaign, criminals trick users into creating a crypto wallet on a phishing site so the bad actors have access to the wallet. Once the victim transfers crypto into the wallet, the criminals steal the funds.
Here is a step by step of the attack.
- Victims are lured to the phishing page with a fraudulent online ad.
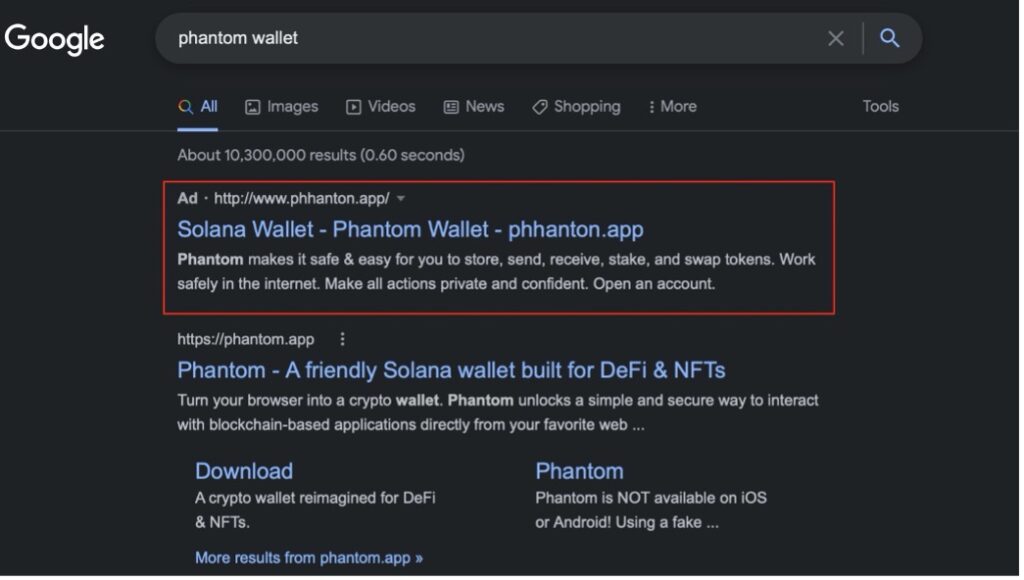
2. The ad linked to a phishing page designed to mimic the real Phantom site.
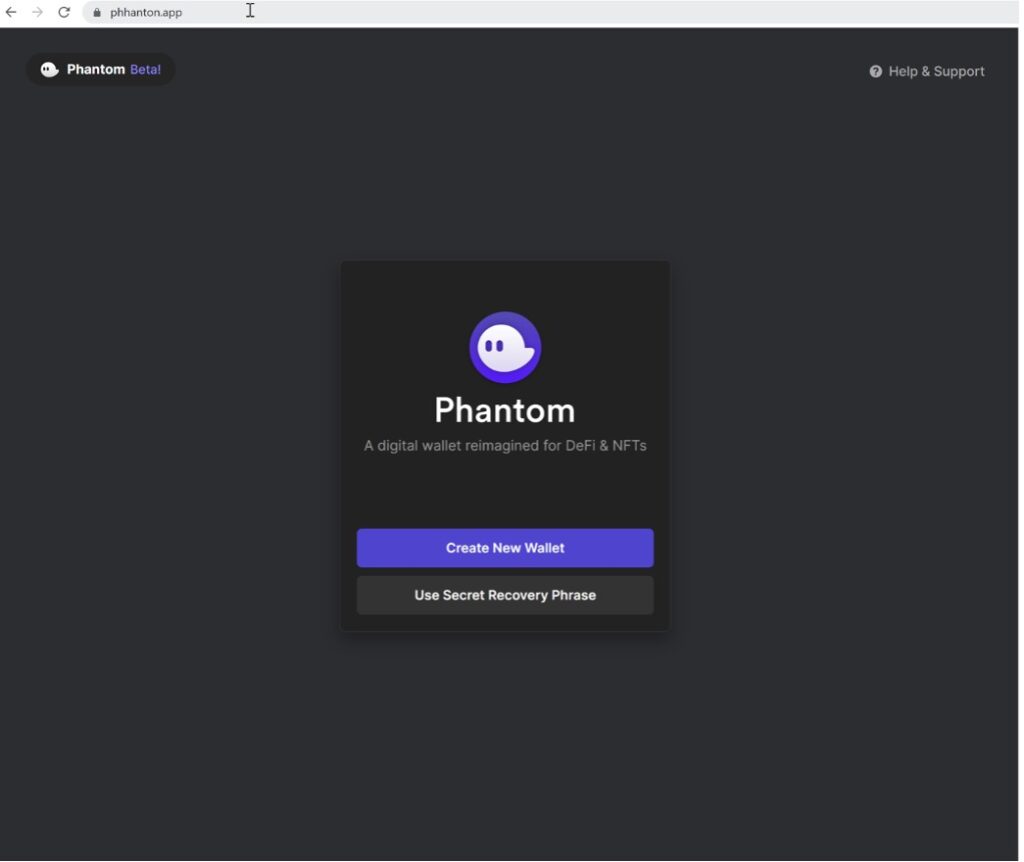
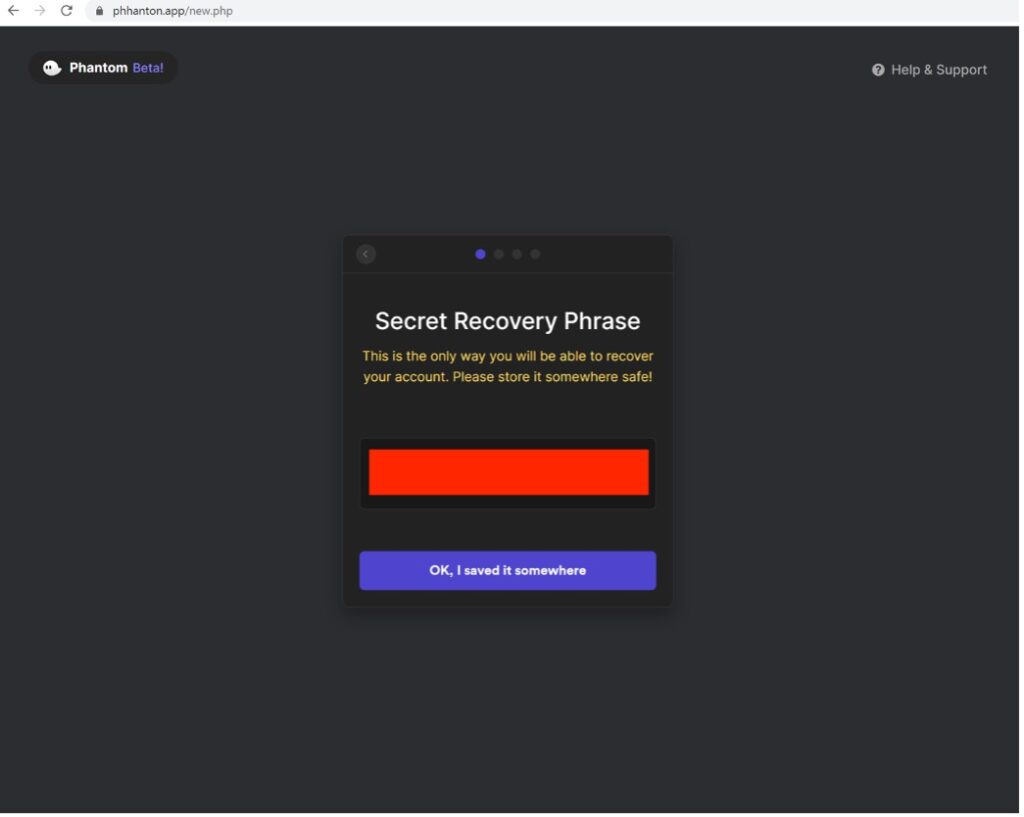
3. The victims navigate the same user experience as they would when interacting with the real Phantom site. Below the user receives their Secret Recovery Phrase after choosing the “Create New Wallet” option
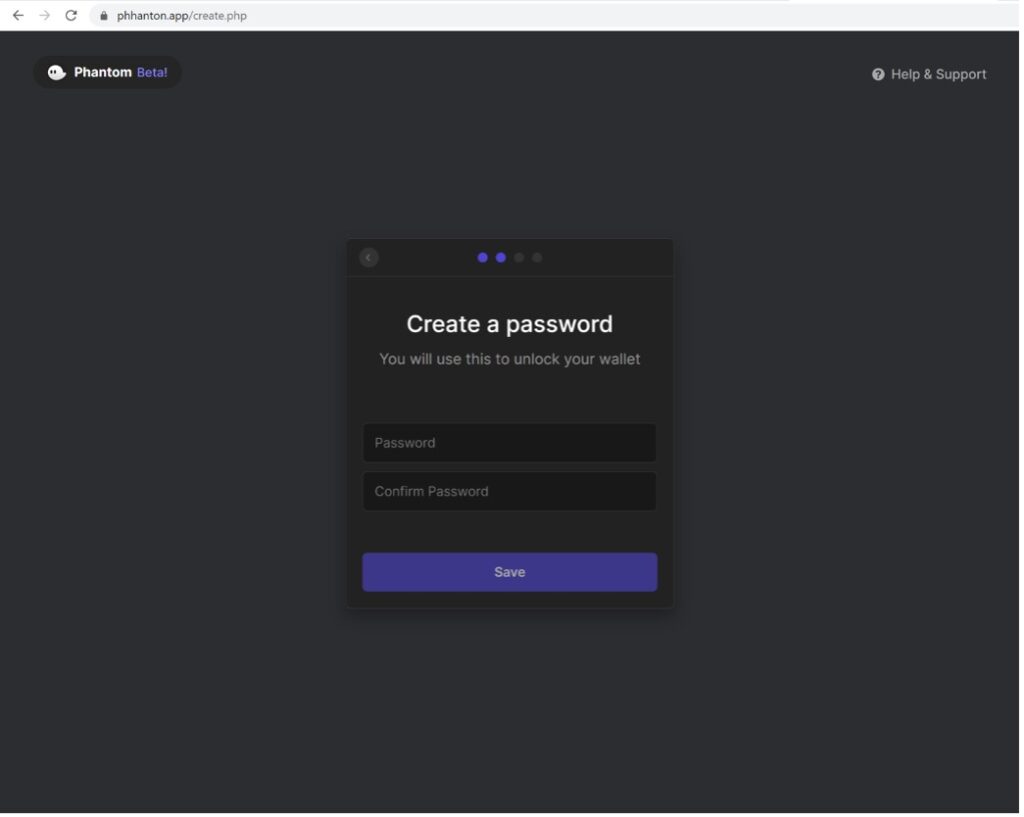
4. Then the user enters and confirms their wallet password. Note the user is still interacting with the phishing site.
5. Next the user receives instructions to open the malicious browser extension.
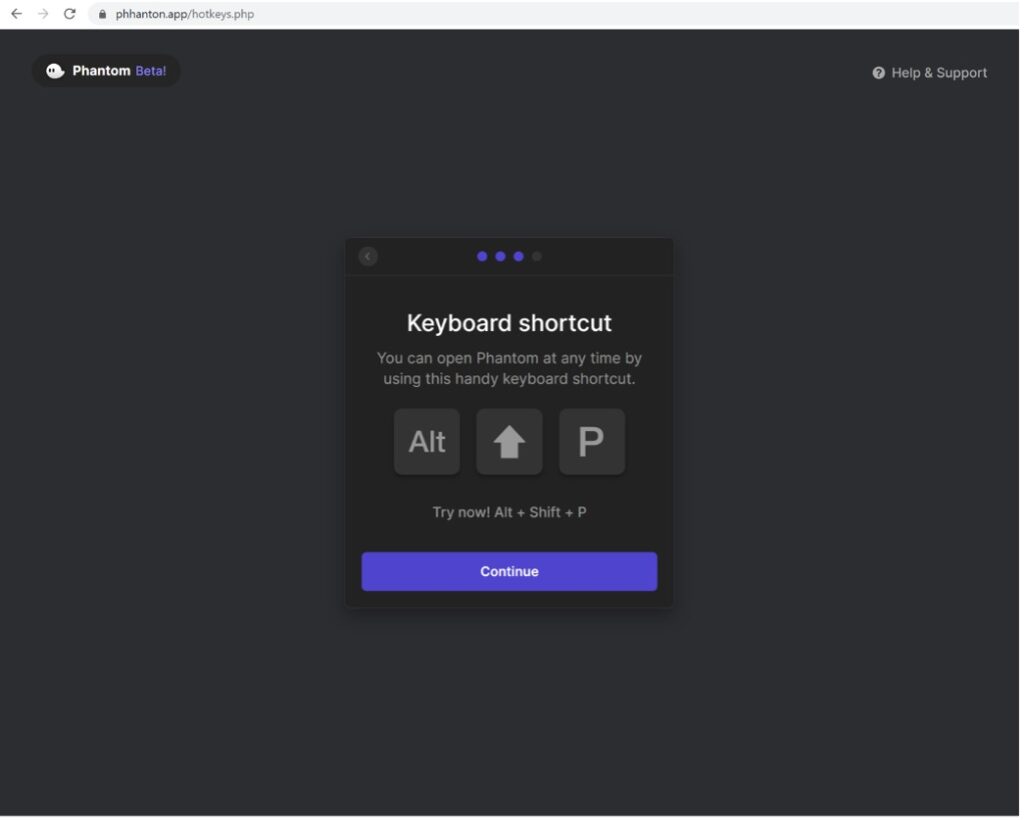
6. The criminals now have all the information from the victim they need to empty the crypto wallet.
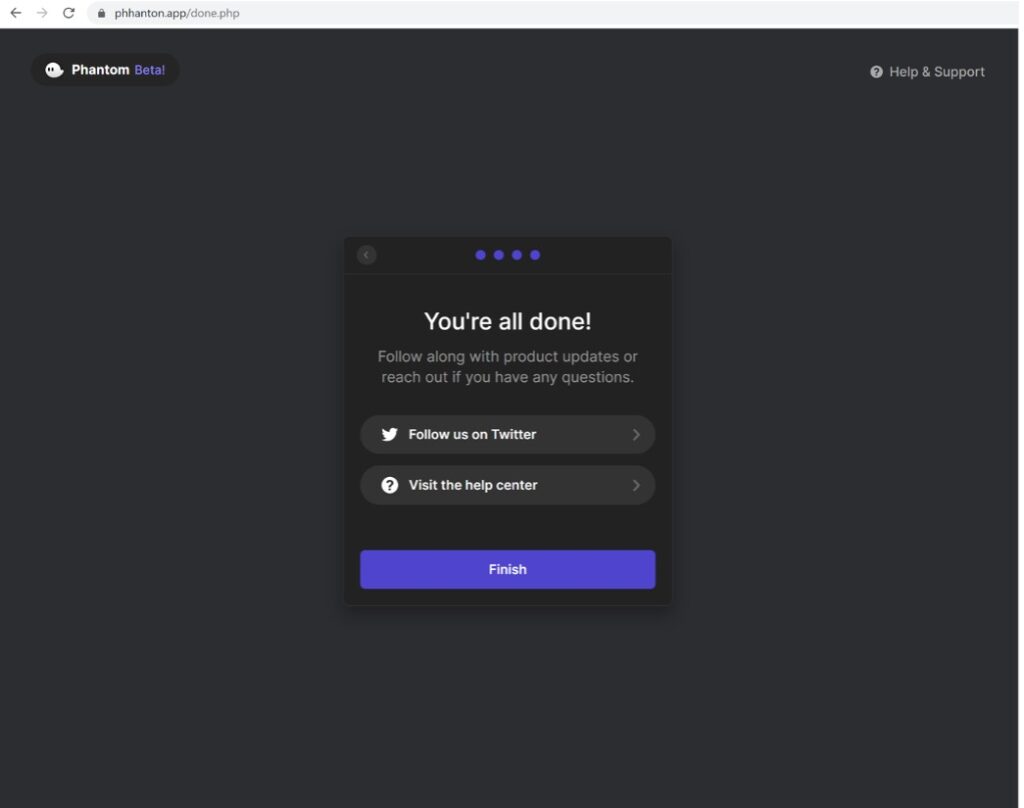
7. And of course, to make the victim feel this process was legitimate, the “Finish” button redirected them to the actual Phantom site.
Although the ads were immediately taken down, there were already several transactions done in the wallet that was created in the phishing page. This is mostly likely because the phishing page was used prior to it being published via the short-lived advertisement.
Following the crypto currency transaction associated with the exposed wallet, some SOL ended up in this wallet which contains over 870,00 SOL.
https://explorer.solana.com/address/5VCwKtCXgCJ6kit5FybXjvriW3xELsFDhYrPSqtJNmcD
It is the same wallet that was used when the Nobu Ninjas NFT minting website was hijacked via DNS cache poisoning. Details of how the hacking transpired are on Nobu Ninjas Twitter page.
Best Practices and Recommendations:
As of this writing, the phishing page has been suspended. Users are advised to verify every link before clicking/opening the site. Also, browser based crypto wallets need to be installed first as an extension in the browser, not after creating the wallet. In this scenario, the option to create a wallet comes first so it should trigger a red flag that it most probably a phishing page.
IOCs:
- https[:]//phhanton[.]app
- https[:]//phanton-account[.]website
- https[:]//phanton-account[.]space
References:
- https://finance.yahoo.com/news/solana-phantom-adds-safety-rails-185842905.html
- https://twitter.com/chasedevens/status/1432742408991690753
- https://twitter.com/NobuNinjas/status/1450611432060604421
Find out how to investigate targeted phishing incidents.

