Online Business — Icing on the Phisher’s Cake
As businesses accelerated their digital transformation over the past year, Cyren Inbox Security has been observing huge increases in the number of phishing incidents related to User Generated Content (UGC) platforms. This increase makes sense as bad actors take advantage of business and consumer trends to use trusted services to commit fraud and other crimes.
Easy to use. Easy to abuse.
Website builders or Content Management Systems have three important advantages for anyone looking to enable a legitimate online business or a targeted phishing attack:
- Simple
- Accessible
- Inexpensive
Website builders or CMS platforms enable you to quickly create attractive and professional-looking business pages. This requires minimum effort and, in most cases, it is inexpensive. This seems to be a huge advantage, doesn’t it? Unfortunately, no. Along with all these good intentions, there is always place for phishers’ activities. Distribution of phishing emails created on website builders, or CMS platforms, provides a lot of opportunities for bad actors, helps avoid detection engines and mailbox filters, and manipulates a victim’s trust.
A Short Cookbook
Website builders, which we observe in Cyren Inbox Security traffic have high Alexa rank (top 500) in global internet traffic and engagement. Phishers take advantage by using highly ranked domains like “wix.com” or “weebly.com’’ slip through email security gateways or mailbox antivirus scanners. Phishing hosted on such popular domains can be easily overlooked in traffic, and security tools ignore them to avoid unwanted false positive alerts.
According to Cyren Inbox Security statistics, the most targeted brand is Microsoft Office 365. Fraudsters can use the domains mentioned above to create and host spoofed login pages for Outlook or any Microsoft O365 service to steal victim’s credentials. If the phisher is creative, then more sophisticated methods will be used to avoid detection, like employing a series of redirects of the URL used in the email body. Another sophisticated scheme is one of the so-called tiered attacks which involve more stages that are harder to catch.
Compromised Web Pages
Do you lack the time and financial funds to create a new website?
Are you an expert in exploiting Flash?
Do you want to create a phishing page as soon as possible?
Then the solution is very simple. Don’t waste your time creating a new site when you can simply compromise an existing one! This is not an advertising campaign slogan, we just want to talk about compromised web pages.
Why does this matter? Compromising a WordPress site, for example, allows the scammer to host malicious content on a domain from an established business that has worked hard to gain users’ trust. Using a good website to do bad things, allows bad actors to infect the victim’s computer with ransomware, trick them into exposing credentials or other sensitive data, or even to use the hacked web page to redirect potential targets to other phishing or malware sources.
A Few Examples for Dessert
1. Phishing page created on Wix.com
Here is an example of the recent phishing attempt, with the phishing page that was created on the Wix site builder. A fraudster sent the request to the potential victim to verify their account for further incoming messages to be reviewed.

Email body of phishing email detected by Cyren Inbox Security
When the “Confirm” button is clicked, the URL redirects to a phishing page for Outlook login credentials. As you might guess, there are no incoming messages that have been suspended. Clicking under the “Confirm” link has no purpose but to direct the user to a phishing page.
If the phishing attack succeeds, the user inserts their credentials and clicks on the “Sign in” button, and the information will fall directly into the phisher’s hands.
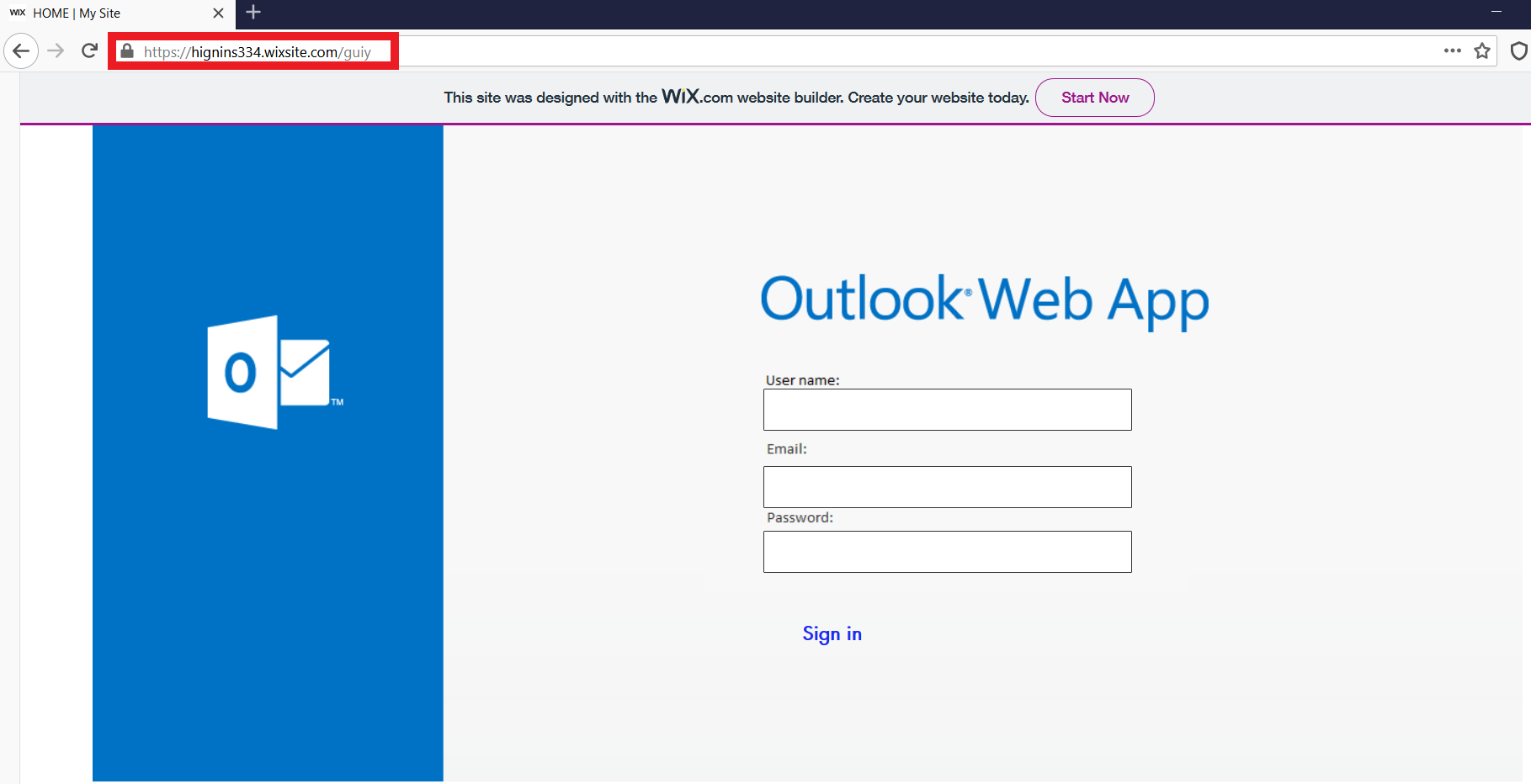
Phishing page created on “wix.com”: hxxps://hignins334.wixsite.com/guiy
2. Multistage phishing attack with Weebly.com
Some of the scammers are sophisticated and inventive and create multistage attacks to ensure that phishing will arrive in the victim’s mailbox. Cyren Inbox Security detected this scenario in some recent incidents, when two-site builder services were used at once. In this case, the user receives an email about a newly shared encrypted document. To view the document, the user should click on the “Click Here to view” link.
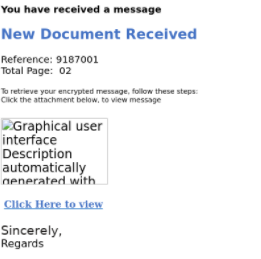
Email body of phishing email detected by Cyren Inbox Security
After the user has clicked the link, the first stage of the attack begins. The phishing page is is a fake SharePoint page hosted on the website builder Zyro, and allegedly contains an unread fax message. To review the document, the user must click the “Preview document Here>>>” button.
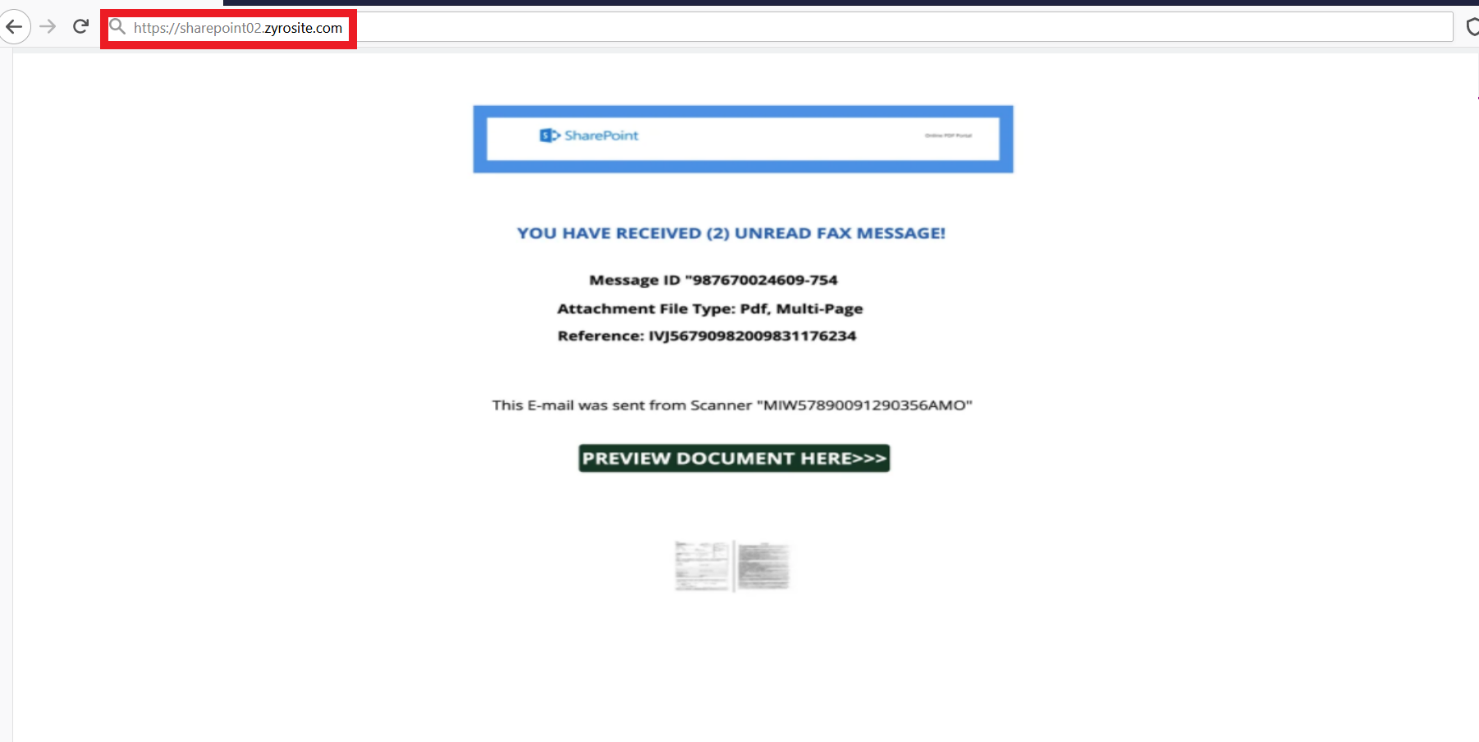
Phishing page created on “zyrosite.com”: hxxps://sharepoint02.zyrosite.com
The last step, and probably the worst for the victim, is an Office 365 phishing login page created on the Weebly website builder.

Phishing page created on “weebly.com”: hxxps://onlinevoicemessageunreadlogin365.weebly.com/
3. Compromised WordPress attack
While compromising a website may take some skill, using the compromised site to host a phishing page is relatively easy. After this WordPress site got hacked, a fraudster placed the phishing content in any folder on the server they wanted. The result (below) is the phisher posted a Microsoft phishing login page that looks just like the real one.
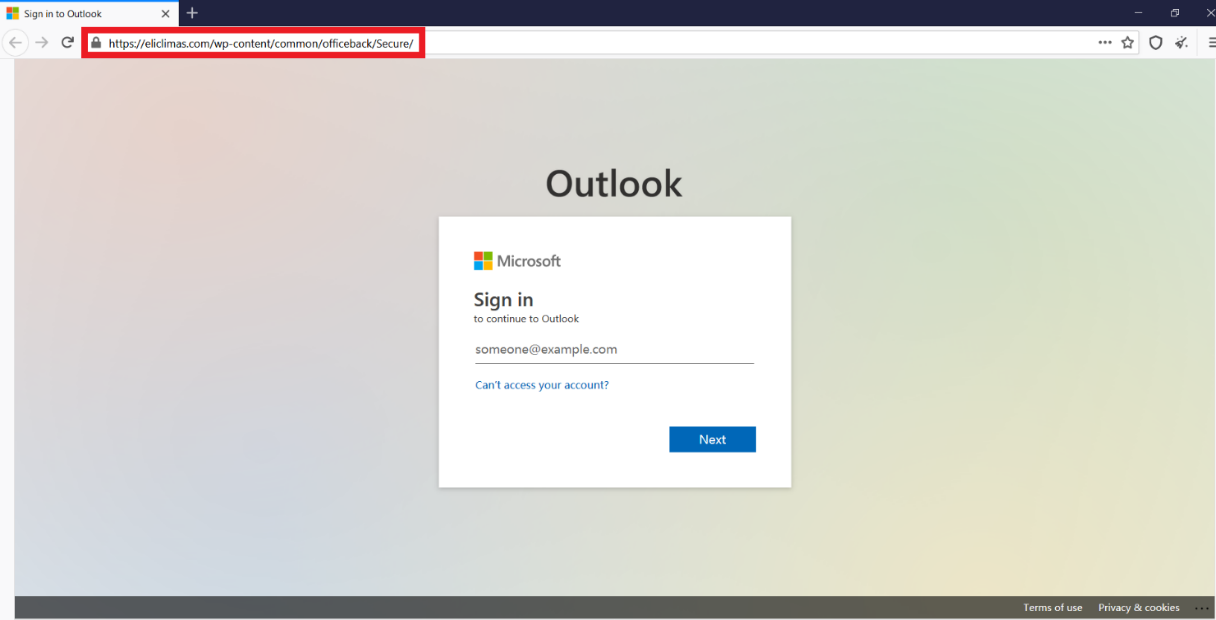
Phishing page placed on compromised WordPress website: hxxps://eliclimas.com/wp-content/common/officeback/Secure/
Detected and Protected by Cyren Inbox Security
Cyren Inbox Security was able to scan and automatically detect these suspicious emails. With our 24×7 Incident Response service, all the attacks were immediately investigated by qualified analysts and confirmed as phishing for all Cyren Inbox Security customers.
