Spear-phishing spoofed attacks have been and remain one of the most substantial cyber threats that organizations face nowadays.
And once we talk about spear-phishing, we can’t help but mention business email compromise (BEC) attacks which if successful result in staggering losses for the companies: the FBI’s Internet Crime Complaint Center stated that BEC attacks resulted in more than $1.7 billion in losses in 2019.
Email spoofing: one of the most common types of BEC attacks
BEC attacks focus on a specific individual or group of people and require some diligent preparation done by the attacker as well as the usage of social engineering techniques to make the phishing look credible.
Email spoofing is one of the most common types of BEC attacks we’ve been observing lately in Cyren Inbox Security.
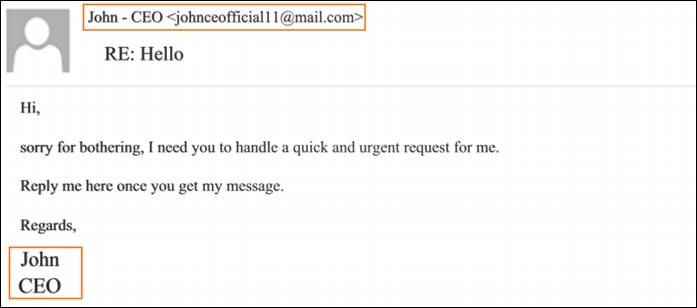
Basic example of the email spoofing BEC attack
The most frequently used patterns of the email spoofing attack include:
- sender display name & mail address (forged headers are the #1 indicator of the spoofed email)
- mail’s subject (usually short and simple: ex. “Hello”, “Task” etc)
- brief and demanding mail content (convincing the potential victim to act fast)
- attack scale (targeted specifically at several employees with access to corporate confidential information and/or funds)
Forged email headers along with the urging mail content make the email look more valid and trustworthy which might easily manipulate the victim into providing all the requested by the attacker data and thus, being phished.
Massive BEC attack on numerous employees at once
Even though the small-scale BEC attacks are the ones that have been occurring more frequently, just recently in Cyren Inbox Security we’ve observed the massive email spoofing attack targeting numerous employees of one company all at once.
Details of the attack
On Wednesday, September 02, at 13:15 UTC an email spoofing BEC attack started, targeting the employees of one of the Cyren Inbox Security biggest customers. Within two hours, a total of 60+ employees of the targeted company received a request letter to ‘complete a discrete task’ from their alleged co-employee.
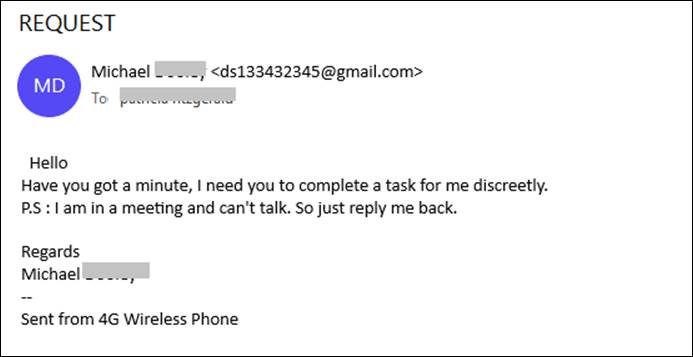
BEC spoofed email targeting the organization’s employees
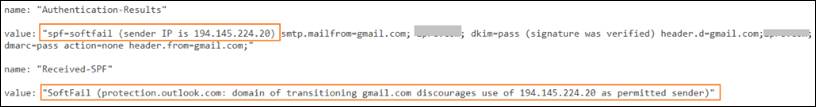
Authentication results for the spoofed email: spf=softfail – one of the indicators of the forged email headers
The attacker used a number of techniques that made the message look visually more genuine and helped to bypass the existing security email filtering capabilities:
- email sent from the legit sender domain which belongs to the trusted web mail provider
- display name looks as it’s coming from someone legitimate and email does not include any suspicious payload
- the sender mail address is not visible for the recipient if opened in the mobile client. And it is noteworthy that mobile remains the leader in mails reading environment with 42% of all emails being opened on smartphones or tablets. [https://www.litmus.com/blog/infographic-the-2019-email-client-market-share/]
By sending a spoofed email to such a large number of employees, this attack appears to be very unusual in terms of scale for the BEC type of attacks. Usually the limit of the potential victims of BEC email spoofing is up to 10, and average is about four.
Cyren Inbox Security Detection
Even though this attack was invisible to the traditional Secure Email Gateway and reached the employee’s mailboxes, the targeted company uses Cyren Inbox Security and as a result the attack was stopped! Every email was automatically scanned and marked as suspicious by Cyren Inbox Security informing the recipients that the email might not be legit.
And furthermore, as a result of Cyren Incident Response Service with its 24×7 support for phishing investigation used by the targeted organization, every copy of the email was additionally investigated, marked as phishing and removed from the mailbox in just several minutes after the emails originally arrived.
