Mysterious Transformation from Scammer to Executive Manager
Trust but verify – how often have you heard this saying? Most likely a lot, it’s so easy for users to forget this important instruction when our email inboxes are busier than ever. As the number of sent and received emails has increased to around 300 billion in 2020 so have the number of opportunities for scammers.
Business email compromise (BEC) is an attempt to impersonate someone to illegally take over the victim’s finances. A BEC attack excludes phishing URLs and malicious files in the attachment. This specific attack is based on social engineering skills, making it hard for the security engines to detect the email once it arrives into the victim’s mailbox.
Usually, BEC is a small-scale attack, which implies a clearly targeted victim. As a general rule, attackers target the person which deals with or indirectly relates to the organization’s finances, or has access to corporate banking accounts, etc. It is easy to understand that such an attack requires careful preparation. The criminal must have detailed knowledge of the recipient and the impersonated sender – the trust relationships, their habits and personal qualities. The scammers need strong social engineering skills to be.
Low Volume, High Impact
According to Cyren Inbox Security statistics, the average percentage of BEC emails is around 2% out of total malicious emails. This does not seem like an astronomical amount, however, we should remember that such an attack is specifically targeted with the main purpose of tricking the victim to submit a money transfer, and it can accumulate to billions of dollars. In comparison with other types of cybercrimes, BEC is considered the most expensive attack.
There are a few well known techniques to trick an employee to send money into the scammer’s pocket. Usually, an impostor tries to impersonate someone from inside the company and pretends to be an internal employee, or trusted vendor/business partner. To make fake emails look more realistic, impostors usually use newly created short-lived email addresses. Often the email address itself has nothing to do with the impersonated person. In such a case the scammer might use the name, email address, or corporate domain of the impersonated person to mislead the victim. It is especially effective when the sender’s address is hidden, and only the name is displayed on the recipient side, as if often the case when reading email on a mobile device.
Gmail as the Primary Free Webmail Provider Used by BEC Actors
The cheapest and the most affordable way to deliver business email compromise attacks is using free webmail providers. According to 4th Quarter 2020 Phishing Activity Trends Report from APWG, around 75% of the BEC attacks were sent from free webmail providers. Gmail is the preferred service of BEC threat actors. Cyren research shows that the main distributor of business email compromise attacks in Cyren Inbox Security traffic is free webmail provider Gmail. Of the BEC incidents detection by Cyren Inbox Security, over 70% were delivered through Gmail webmail, 60% of which were sent from ‘gmail.com’ sender address domain directly, and 40% used ‘gmail.com’ domain in reply-to.
How Does the Potential Victim Get Hooked?
To answer this question, let’s see a few real examples from the recent detected business email compromise attack in Cyren Inbox Security.
Usually, an Impostor email is characterized by a short message. It includes keywords that prompt the victim to react and respond quickly, for example “ASAP”, “Urgent”, “Request”, “Task” etc.
Also, due to the fact that BEC attacks are mostly about money transfers, fraudsters often mention bank accounts or payrolls.
1. Business Email Compromise emails sent directly from the Gmail
Below are a few examples of an attacker using Gmail to directly send a BEC or impersonation attack.
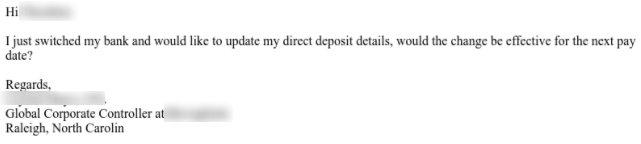
Email body
The screenshot above shows that the scammer tried to update personal deposit details by impersonating an employee and created a sense of urgency by stating the task should be performed before the next pay. The email was sent from the “cupc774@gmail.com”, which of course did not belong to the real employee.
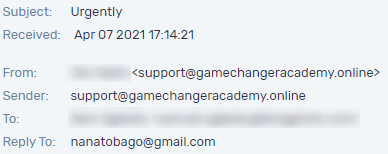
Email header
Below is a slightly different BEC attack detected in Cyren Inbox Security. The attacker tried to impersonate a company employee (Senior Software Engineer) to change the payroll account.
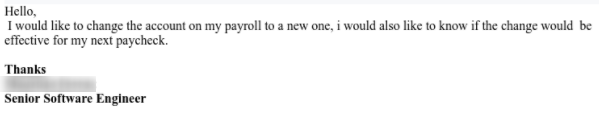
Email body
Here the scammer highlighted the seriousness of the email by the subject “Urgent”, meaning it was quite important and wanted to change the payroll account till the next payment date. The email, as qith the previous example, was sent from a Gmail address.
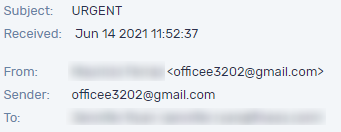
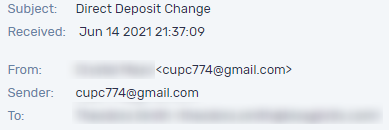
Email header
2. Business Email Compromise emails with Gmail address in reply-to
Sometimes, an impostor starts the attack with a quick message related to an urgent task or an important call. Such a technique allows the scammer to establish a history with the victim and avoid the security engines and gain the victim’s trust by assuring the authenticity of the email.
![]()
Email body
The sender used different addresses in the “From” and “Reply-to” fields, which allows the sender’s identity to be hidden.