Every internet user participates in surveys every day: “Do you like our service?” “Are you satisfied with the order?” “Please, fill the form below to make us better for you!”
Scammers know these survey forms are mundane, and often filled out reflexively. By using free “form-builder” services, attacks:
- can be quickly spun up, without any special equipment or high computing skills
- are ignored by most detection engines. Microsoft forms, Google forms, Typeform, 123formbuilder and Native forms are considered trustworthy.
Anatomy of the attack – Phishing via Typeform
The most common technique Cyren sees? Victims are asked to insert credentials in a disguised form.
In this attack, the victim is informed their account was blocked, compromised or deactivated. The victim is invited to update credentials or upgrade to another version (which is not getting blocked or is safer for usage).
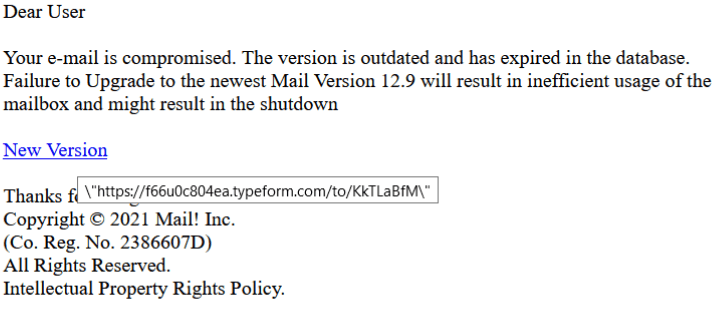
Phishing email
Under the button “New Version”, the scammer hid a redirected URL created on “typeform.com.
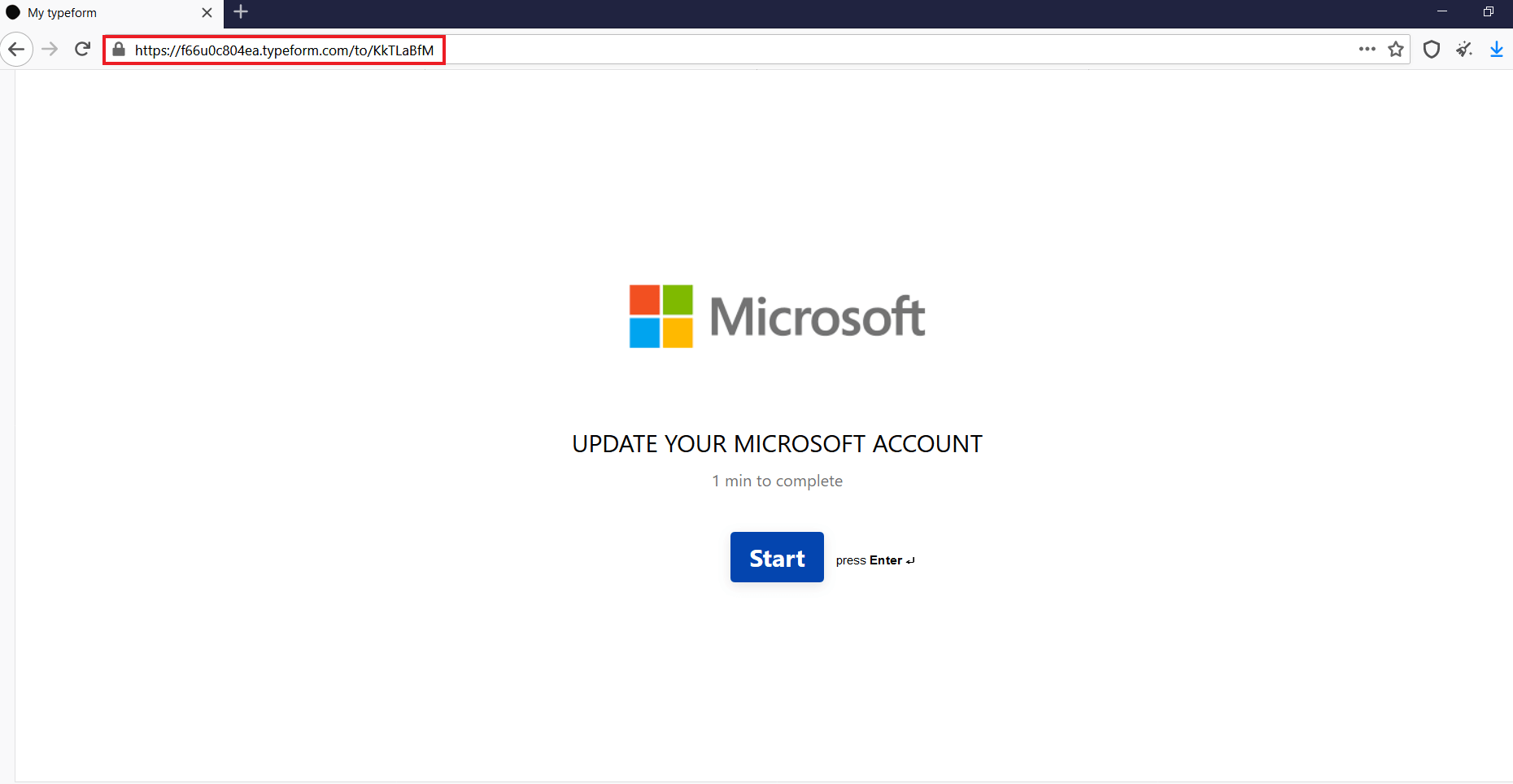
Phishing Microsoft page based on “Typeform”: hxxps://f66u0c804ea.typeform.com/to/KkTLaBfM
Once clicked, a fake Microsoft page asks the user to start a survey with two easy questions: e-mail and password. No complicated redirects or sophisticated URL wrapping… in just two clicks the victim is hooked.
Anatomy of the attack – Phishing via Microsoft Forms
In the previous attack, the targeted user could notice the mismatched Microsoft page content and Typeform URL.
By hosting the attack on Microsoft forms, the domain “forms.office.com” looks much more trustworthy.
In this attack, the victim is similarly informed their account was blocked, compromised or deactivated:
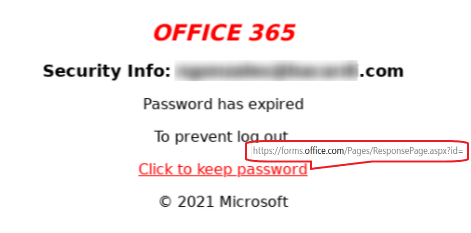
Phishing email
To save their password, the user is prompted to click on the red button, which reveals a fake Microsoft page hosted on “forms.office.com.”
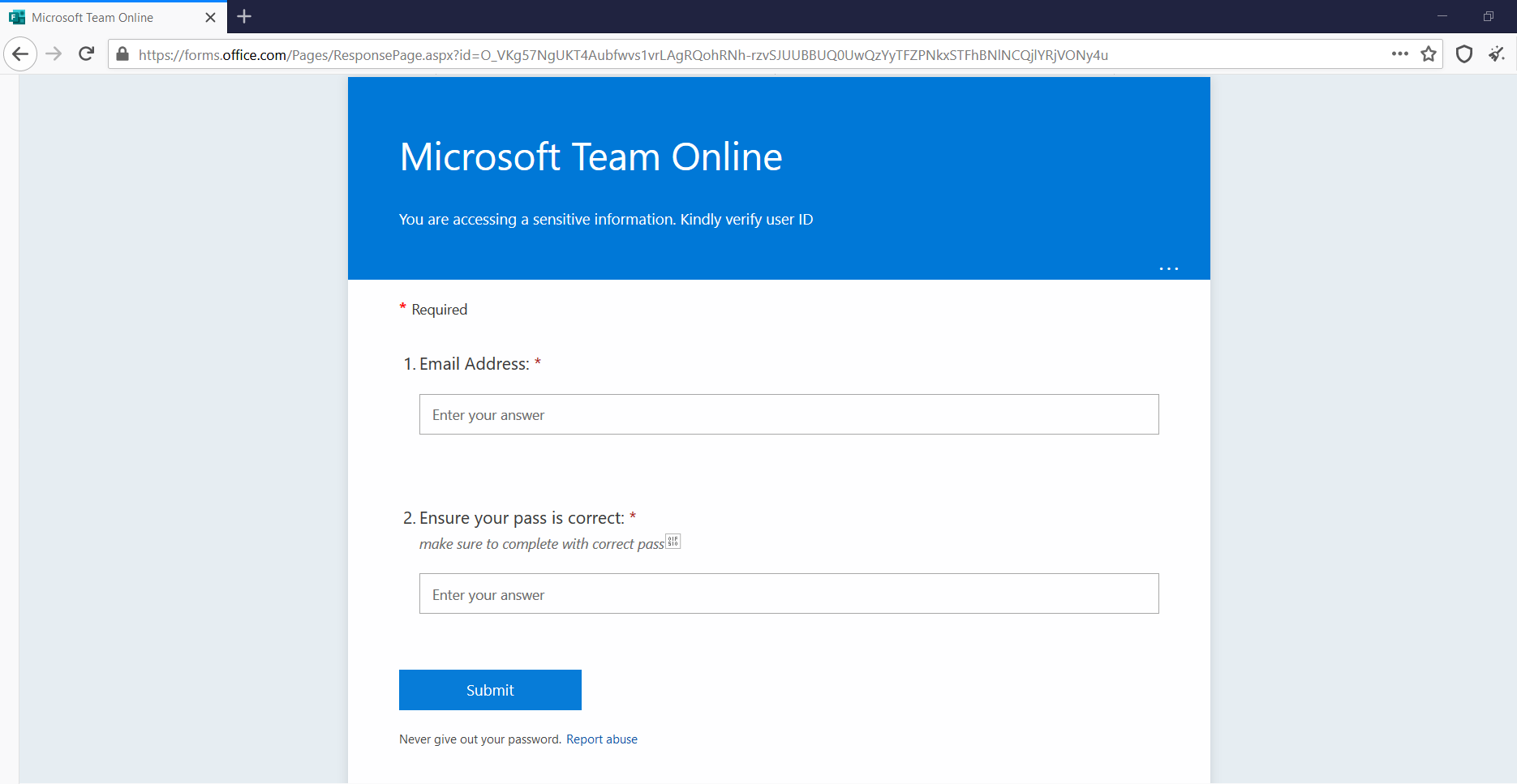
Fake Microsoft page based on “Microsoft Forms”: hxxps://forms.office.com/Pages/ResponsePage.aspx?id=O_VKg57NgUKT4Aubfwvs1vrLAgRQohRNh-rzvSJUUBBUQ0UwQzYyTFZPNkxSTFhBNlNCQjlYRjVONy4u
Detected and Protected by Cyren Inbox Security
Cyren Inbox Security was able to scan and automatically detect these suspicious emails. We successfully removed every copy of these masquerading emails from the employees’ mailboxes.
Ready to play with Cyren Inbox Security for Microsoft 365 Start a 30-day trial >
